Table of Contents
Ransomware Actors Exploit SSH Tunneling to Target VMware ESXi Hosts
Ransomware threat actors are increasingly leveraging sophisticated techniques to infiltrate VMware ESXi hosts, with SSH tunneling emerging as a primary method for stealthy network intrusion. This approach allows cybercriminals to access critical virtualized infrastructure while remaining virtually undetectable by traditional security monitoring systems.
ESXi hypervisors represent particularly attractive targets for ransomware groups due to their central role in managing multiple virtual machines within an organization's infrastructure. By compromising a single ESXi host, attackers can potentially encrypt or manipulate entire virtualized environments, causing widespread operational disruption.
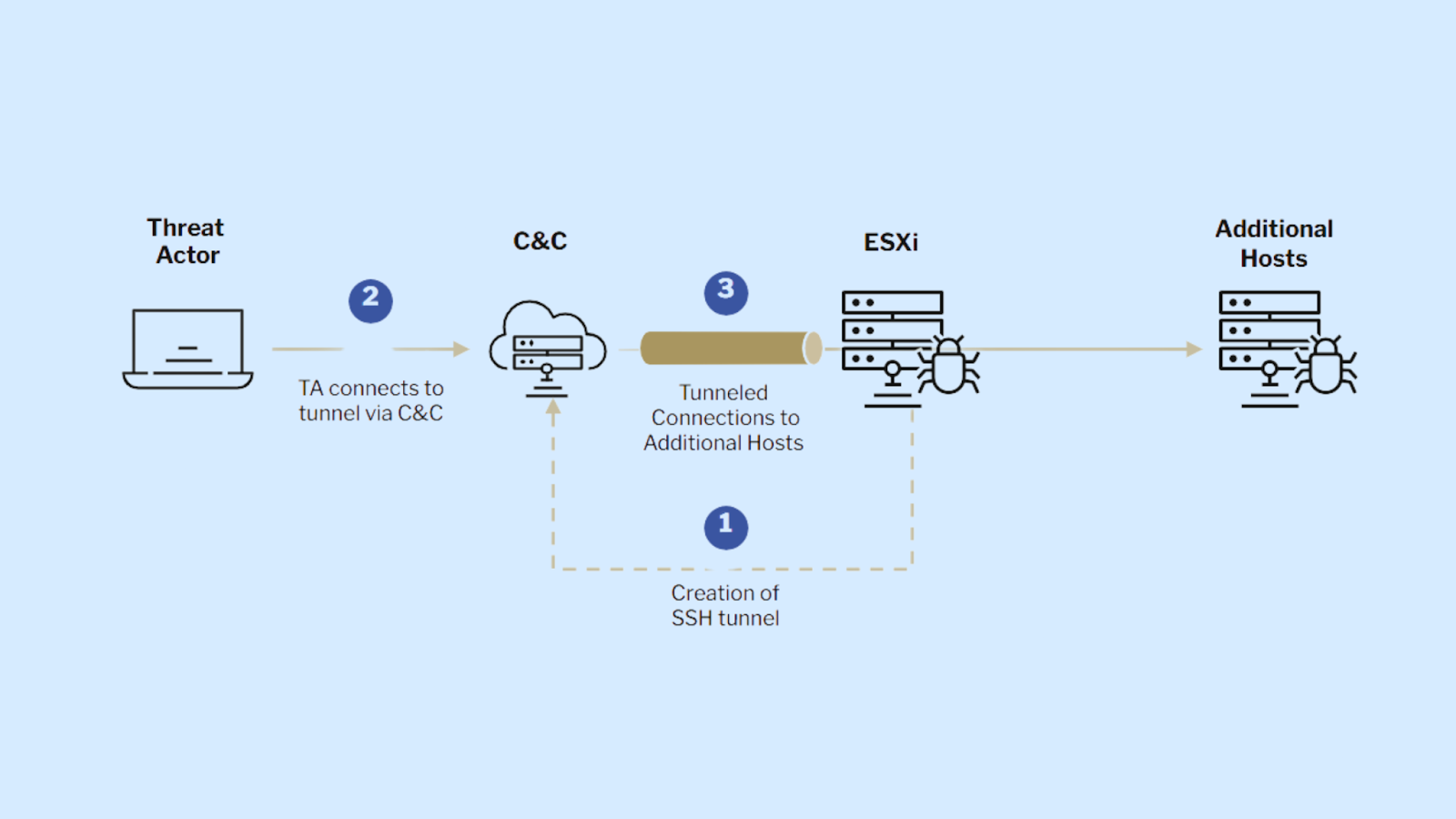
The attack methodology typically begins with gaining initial access to the ESXi appliance, which can be achieved through various means such as exploiting known vulnerabilities or using compromised administrative credentials. Once inside, threat actors utilize the native SSH functionality to establish covert communication channels and maintain persistent access.
SSH tunneling provides attackers with a powerful mechanism to blend malicious traffic with legitimate administrative activities. By creating a SOCKS tunnel between the compromised ESXi host and their command-and-control (C2) server, cybercriminals can route network communications in a manner that appears inconspicuous to standard security monitoring tools.
Cybersecurity researchers have observed that ESXi environments are often inadequately monitored, making them ideal platforms for extended reconnaissance and lateral movement. The resilient nature of these appliances, which are rarely rebooted, further enhances their appeal as potential long-term infiltration points.
The logging architecture of ESXi servers complicates forensic investigations, as logs are distributed across multiple files rather than consolidated in a single location. This fragmentation requires investigators to meticulously piece together evidence from sources like /var/log/shell.log, /var/log/hostd.log, and /var/log/auth.log to reconstruct the sequence of malicious activities.
Cybersecurity experts recommend several strategies to mitigate these risks. Organizations should prioritize limiting administrative privileges, ensuring SSH is disabled by default, and implementing robust authentication mechanisms. Regular vulnerability patching and comprehensive logging through centralized syslog forwarding can significantly enhance detection capabilities.
The evolving tactics demonstrate the adaptive nature of modern ransomware groups, who continually seek innovative methods to circumvent traditional security controls. As virtualized infrastructures become increasingly complex, maintaining vigilant and proactive security measures is paramount to protecting critical digital assets.
Organizations must recognize that SSH tunneling represents more than just a technical vulnerability—it's a strategic approach by threat actors to exploit overlooked infrastructure components. Comprehensive security strategies must therefore extend beyond conventional perimeter defenses to include granular monitoring and rapid incident response capabilities.
Found this article interesting? Keep visit thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive tips like this.
You may also like these articles: Here are the 5 most contextually relevant blog posts:
Anthony Denis
Anthony Denis a Security News Reporter with a Bachelor's in Business Computer Application. Drawing from a decade of digital media marketing experience and two years of freelance writing, he brings technical expertise to cybersecurity journalism. His background in IT, content creation, and social media management enables him to deliver complex security topics with clarity and insight.