Table of Contents
Streamlining Security Operations with SOAR
As cyber threats become more frequent and sophisticated, security teams struggle to keep up. The 2022 SANS Incident Response Survey reveals over 50% of respondents feel overwhelmed by high alert volumes. Moreover, strained resources coupled with manual and repetitive tasks slow down threat investigation and remediation.
To bolster security operations, organizations are turning to SOAR (Security Orchestration, Automation and Response) solutions. Gartner predicts the SOAR market will grow from $1.69 billion in 2022 to $4.43 billion by 2027. What makes SOAR so critical? It empowers resource-constrained security operations centers (SOCs) to modernize processes, accelerate response times and reduce costs.
This blog post explores how SOAR helps optimize SOC workflows to improve productivity, efficiency and outcomes. We analyze SOC metrics showcasing SOAR’s benefits and provide guidance on applying SOAR effectively.
Why Modernize Security Operations?
As outlined in the NIST cybersecurity framework, key functions of a cybersecurity program include identifying, protecting, detecting, responding, and recovering. Conceptually, we can divide these into prevention and response categories. Security operations primarily focus on incident detection and response through the Security Operations Center (SOC).
However, SOCs encounter several challenges today:
Too many alerts overwhelm analysts
Too many false positives waste time and resources
Too many manual and repetitive tasks
Too few skilled analysts to handle incidents
Too few hours to respond to incidents
Too few indicators to uncover the full story of incidents
To solve these problems, we need to modernize security operations. This is where SOAR solutions come in.
Why SOAR is a Critical Piece of the Puzzle?
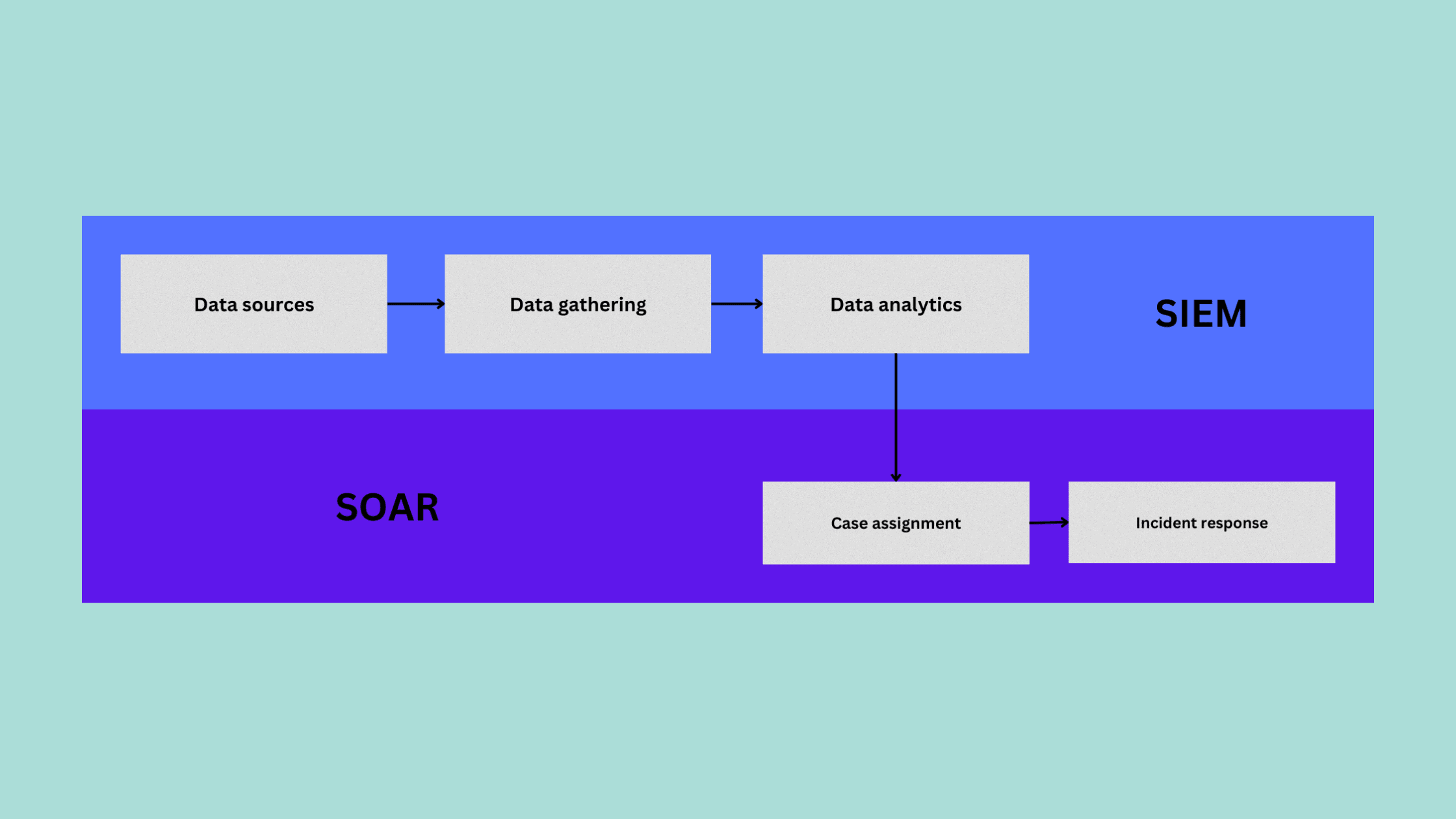
The concept of a security operations center encompasses people, processes and technology working in conjunction. A well-designed SOC workflow typically involves five key stages:
Data Collection: Gather security data from across environments
Data Analytics: Apply analytics to detect potential threats
Case Management: Assign detected threats to cases/incidents
Incident Response: Investigate and remediate security incidents
Post Incident Activity: Carry out recovery procedures
SOAR platforms aim to enhance productivity specifically within the incident response process. According to Gartner, top use cases for SOAR adoption based on client inquiries are:
Automating repetitive/manual tasks
Improving incident response
Enhancing efficiency of Tier 1 analysts
How does SOAR stack up against traditional security operations? Here is a look at key performance indicators before and after SOAR implementation:
| Metric | Before SOAR | After SOAR | Improvement |
|---|---|---|---|
| Alerts Requiring Triage | 3,000/week | 1,500/week | 50% Reduction |
| MTTR | 28 hours | 7 hours | 75% Faster |
| Cost Per Incident | $14,700 | $7,350 | 50% Lower |
With increased automation and orchestration, organizations can respond faster, resolve more incidents and substantially reduce operational costs.
What is SOAR and What Benefits Does it Provide?
Before we go further, let’s learn what is SOAR. SOAR stands for Security Orchestration, Automation and Response. It helps organizations achieve security objectives by:
Orchestration: Integrating disparate security tools/processes
Automation: Replacing manual operations with automated workflows
Response: Optimizing incident triage, investigation, and remediation
Key benefits of implementing SOAR include:
Accelerated response times (reduced MTTA and MTTR)
Increased productivity by focusing on high-value tasks
Cost savings through optimized resource allocation
Enhanced collaboration across security/business teams
How to Apply SOAR in Your Security Operations Center?
Let’s look at how SOAR helps streamline the Security Operations Center (SOC). Here is a high-level view of the SOC workflow:
We gather security data from endpoints, apps, infrastructure etc. These logs/metrics are aggregated and fed into analytics for threat detection. Alerts are assigned to incidents, which are handled by SOC analysts.
A typical SOAR implementation focuses on the stages from incident creation to response by automating repetitive manual tasks. For example:
Tier 1 analysts use SOAR to reduce false positives and accelerate triage
Tier 2 analysts leverage SOAR to enrich threats and auto-remediate issues
Tier 3 analysts utilize SOAR to streamline collaboration and automate threat-hunting
Options for Automation with SOAR
As a core SOAR capability, automation replaces manual operations through three main options:
Automation Rules: Centrally manage conditions and actions for incident handling
Playbooks: Predefined processes comprising orchestrated actions to handle incidents
Artificial Intelligence: Rapidly analyze threats and provide response recommendations
While SOAR platforms provide automation rules and playbook building functions, they also integrate with AI solutions via orchestration.
Implementing SOAR Effectively
Like any other IT solution, effective SOAR implementation entails change management across six key stages:
Understand business needs and problems aiming to solve
Analyze current security processes and workflows
Prioritize and plan SOAR projects starting with small
Design architecture aligned to security best practices
Develop playbooks adhering to software engineering best practices
Continuously re-evaluate objectives and update processes
Rather than attempting to overhaul entire operations immediately, take an iterative approach to building capabilities over time.
SOAR platforms enable security teams to work smarter by increasing automation, optimizing resource usage, and ultimately shortening incident response times. To learn more about streamlining your Security Operations Center with SOAR, check out the attached introductory PDF guide.
We hope this post helped in modernize and streamline security operations. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.