Table of Contents
PECmd
Free
Digital forensics is a critical field in today's world, where cyber crimes are on the rise. Investigators need efficient tools to analyze digital evidence and uncover crucial information. One such powerful tool is PECmd, developed by Eric Zimmerman. PECmd is a command-line utility that enables investigators to parse and analyze Windows Prefetch files, which can provide valuable insights into system activity and user behavior. In this article, we will explore PECmd in detail, including its features, usage, and benefits for digital forensics professionals.
What is PECmd?
PECmd, short for Prefetch Explorer Command Line, is an open-source tool written in C# that allows investigators to process and analyze Windows Prefetch files from the command line. Prefetch files are created by Windows to speed up application startup times and contain metadata about recently run applications. PECmd extracts this metadata, including file paths, run counts, and timestamps, which can be crucial in reconstructing user activity on a system. With its flexible output options and ability to process entire directories recursively, PECmd is a valuable addition to any digital forensics toolkit.
Key Features
PECmd offers several key features that make it a powerful tool for digital forensics:
Recursive directory processing: PECmd can process entire directories of Prefetch files, making it efficient for analyzing large datasets.
Flexible output formats: Results can be exported in JSON, CSV, and HTML formats, allowing for easy integration with other tools and reporting.
Keyword highlighting: Investigators can specify keywords to highlight in the output, making it easier to identify relevant information.
Volume Shadow Copy support: PECmd can process Prefetch files from Volume Shadow Copies, enabling analysis of historical system states.
Deduplication: Results can be deduplicated based on SHA-1 hash, reducing redundancy in the output.
Who Can Use PECmd?
PECmd is designed for digital forensics professionals, incident responders, and security researchers who need to analyze Windows systems. It requires a basic understanding of the command line and Windows Prefetch files. However, with its straightforward command-line interface and well-documented usage examples, PECmd is accessible to both novice and experienced investigators. Whether you're working on a live system or analyzing an acquired disk image, PECmd can help you uncover valuable evidence.
Supported Platforms
PECmd is a Windows-based tool and requires .NET Framework 4.5 or later. It can process Prefetch files from Windows XP through Windows 10, making it compatible with a wide range of systems. However, it's important to note that if you are running a version of Windows older than Windows 8, you will not be able to process Windows 10 Prefetch files due to format differences. PECmd is a command-line tool and does not have a graphical user interface.
How to Install PECmd?
Follow these step-by-step instructions to install PECmd:
Visit the official GitHub repository for PECmd at https://github.com/EricZimmerman/PECmd/releases.
Locate the latest release of PECmd and click on the ZIP file to download it. The file will be named something like "PECmd_X.X.X.X.zip", where "X.X.X.X" represents the version number.
Once the download is complete, extract the contents of the ZIP file to a directory of your choice. You can use the built-in Windows extraction tool or a third-party application like 7-Zip or WinRAR.
Open the extracted directory and verify that it contains the PECmd.exe file along with any additional files or directories.
PECmd is now installed and ready to use. As a portable tool, it does not require any further installation steps or modifications to your system.
To run PECmd, open a command prompt (cmd.exe) and navigate to the directory where you extracted the PECmd files using the
cdcommand. For example, if you extracted the files to "C:\Tools\PECmd", you would enter:cd C:\Tools\PECmdYou can now run PECmd by executing the
PECmd.exefile followed by the desired command-line options. For example, to process a single Prefetch file, you would enter:PECmd.exe -f "C:\Temp\CALC.EXE-3FBEF7FD.pf"
By following these steps, you will have successfully installed PECmd and can start using it to analyze Windows Prefetch files in your digital forensics investigations.
How to Use PECmd?
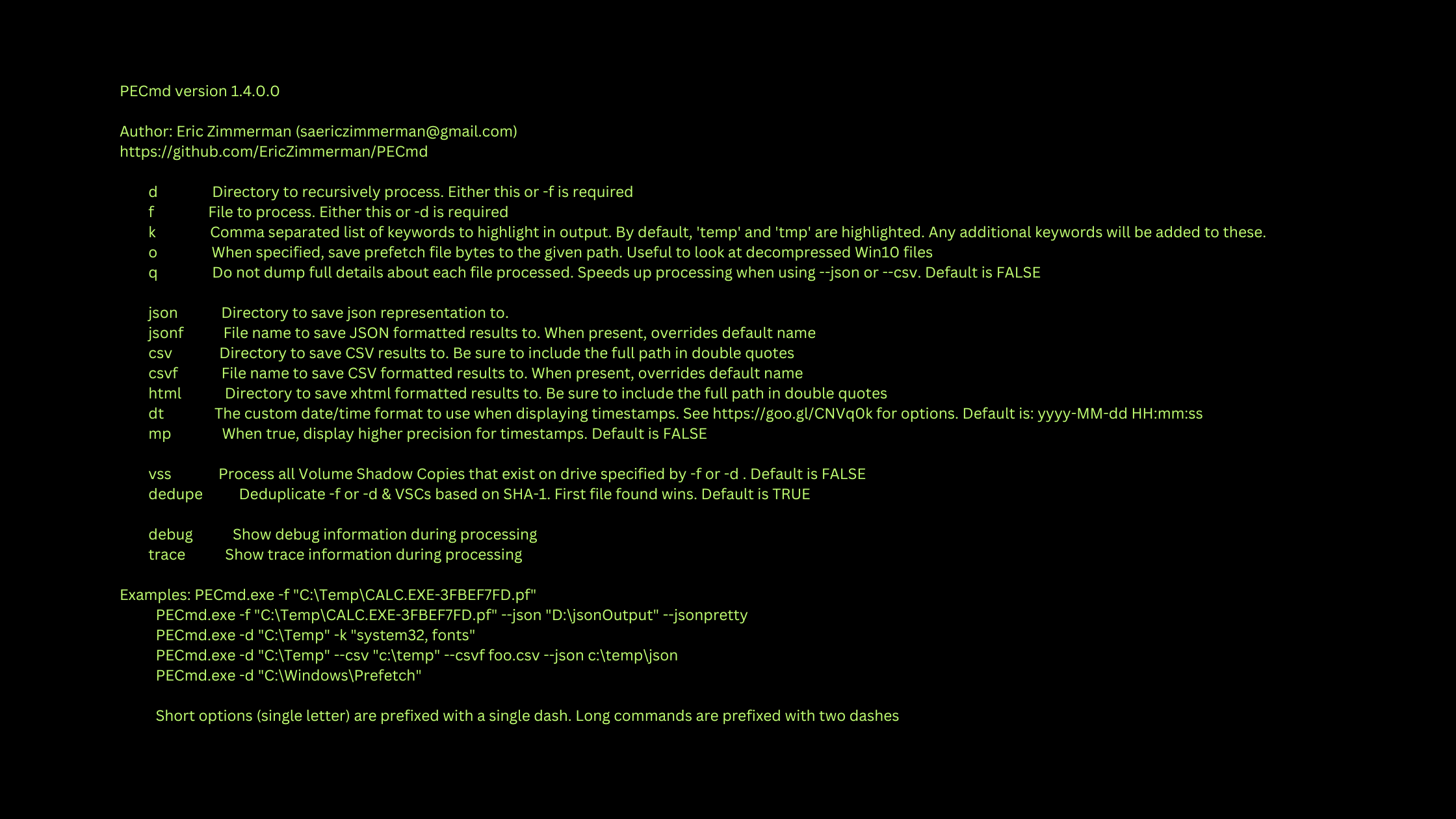
PECmd is a command-line tool that requires specific options and arguments to process Prefetch files. Here are some common commands and their explanations:
Process a single Prefetch file:
PECmd.exe -f "C:\Temp\CALC.EXE-3FBEF7FD.pf"-f: Specifies the path to the Prefetch file you want to process.
Process a directory recursively:
PECmd.exe -d "C:\Windows\Prefetch"-d: Specifies the directory containing Prefetch files to process recursively.
Save results in JSON format:
PECmd.exe -d "C:\Windows\Prefetch" --json "D:\Output"--json: Specifies the directory where the JSON output will be saved.
Save results in CSV format:
PECmd.exe -d "C:\Windows\Prefetch" --csv "D:\Output" --csvf "results.csv"--csv: Specifies the directory where the CSV output will be saved.--csvf: Specifies the filename for the CSV output.
Highlight specific keywords in the output:
PECmd.exe -d "C:\Windows\Prefetch" -k "system32, fonts"-k: Specifies a comma-separated list of keywords to highlight in the output.
Process Volume Shadow Copies:
PECmd.exe -d "C:\Windows\Prefetch" --vss--vss: Processes all Volume Shadow Copies that exist on the specified drive.
Deduplicate results based on SHA-1 hash:
PECmd.exe -d "C:\Windows\Prefetch" --dedupe--dedupe: Deduplicates the results based on the SHA-1 hash of the Prefetch files.
These are just a few examples of how to use PECmd. You can combine multiple options to customize the output and processing behavior. For a complete list of available options, refer to the built-in help by running:
PECmd.exe --helpRemember to replace the file paths and directory paths in the commands with the actual locations of your Prefetch files and desired output directories.
Bottom Line
PECmd is a powerful and flexible tool for analyzing Windows Prefetch files in digital forensics investigations. With its ability to process entire directories, support for Volume Shadow Copies, and multiple output formats, PECmd streamlines the analysis process and helps investigators uncover critical evidence. Whether you're a seasoned forensics professional or just starting in the field, PECmd is a valuable addition to your toolkit. By leveraging the insights provided by PECmd, investigators can better understand user activity, application execution, and system behavior, ultimately leading to more effective and efficient investigations.
Ref:
PECmd
Free
March 18, 2024