Table of Contents
9 Android Apps Stealing Facebook Password Found On The Play Store!
Cybersecurity researchers discovered nine android apps stealing the Facebook passwords of their users. The apps were removed from the Play store in response to the password-stealing campaign. However, the users who downloaded the apps are still prone to the password-stealing campaign.
Victim Of These Nine Apps Stealing Facebook Password:
The research didn’t reveal the attacks on any particular users belong to a specific geo location. However, It’s been said that more than 5,856,010 users have downloaded these apps stealing Facebook passwords from Google’s play store.
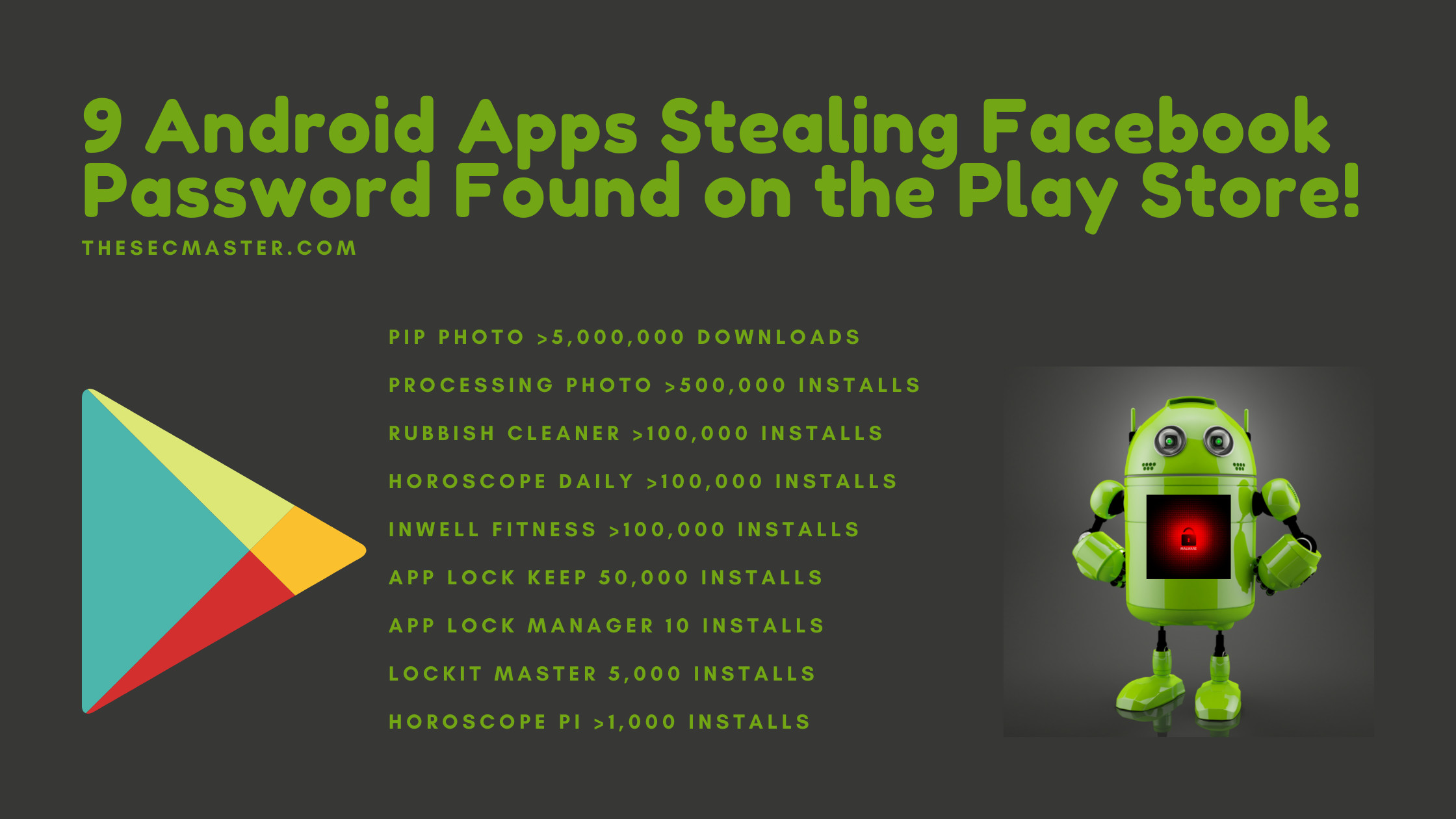
List Of Apps Stealing Facebook Passwords On The Play Store:
Here are the nine apps Doctor Web found on the Play store. See your phone for these apps Immediately and remove them if installed. Most importantly, rest your Facebook password if you haven’t done it yet.
Fig #1: 9 apps stealing Facebook password
PIP Photo (>5,000,000 Downloads): An image editing app that was spread by the developer Lillians.
Processing Photo (>500,000 installs): A photo-editing software that was spread by the developer chikumburahamilton.
Rubbish Cleaner (>100,000 installs): A utility to optimize the Android device performance from the developer SNT.rbcl.
Horoscope Daily (>100,000 installs): An astrology program developed by HscopeDaily momo.
Inwell Fitness (>100,000 installs): A fitness program from the developer Reuben Germaine.
App Lock Keep (50,000 installs): A app developed by Sheralaw Rence.
App Lock Manager (10 installs): Developed by Implummet col.
Lockit Master (5,000 installs): Developed by Enali mchicolo.
Horoscope Pi (>1,000 installs): An astrology program developed by Talleyr Shauna.
How Do These Apps Steal Facebook Passwords?
Attackers have used Android’s play store to launch the password-stealing campaign. Password stealer trojans were used as a harmless application to steal the Facebook password.
Fig #2: Prompting Facebook login
Authors have published the fully functional applications with the same Trojans, which have identical configuration file formats and identical JavaScript scripts to steal user data.
That application was made to prompt Facebook login to access all of the app’s functions and disable in-app ads.
If users agreed and clicked the Facebook login button, they saw the standard Facebook login form as shown.
In fact, the apps have displayed a genuine login form. However, trojan in the app will get the necessary settings from the C&C servers immediately after launch. It loads the legitimate Facebook web page https://www.facebook.com/login.php into WebView along with the JavaScipt downloaded from the C2 servers into the same page.
Attackers will use the same JavaScript to hijack the user-entered credentials. The script transfers the stolen credentials to the trojan applications, transferring the data to the attacker’s C2 server.
After successful login to the Facebook account, the trojans will capture the session cookies from the current authorization session.
Attackers have been targeted to steal the credentials of Facebook accounts. However, trojan settings are easily customizable to replace Facebook with any other legitimate web service or fake phishing site.
Fig #3: Loading Facebook login web form
Countermeasures:
When it comes to deal with any such password-stealing campaign, we would suggest you to do three basic things:
Uninstall the applications from the device.
Reset the web service password, Facebook in this case.
Install a good premium anti malware solution to scan and remove the malwares.
Identified Indicator Of Compromise (IOC) Apps Stealing Facebook Password:
IOCs indicators of compromise. If you found any of these files on your Android device, which has the corresponding SHA-1 hash, take the countermeasures without delay. Additionally, if you notice your Android phone has communicated to these URLs at any point in time, it’s clear that your phone is compromised. The verification process needs some technical knowledge to check the file fingerprints and communication with the URLs. You can leave this section if you are not from a technical background. We feel it’s our duty to give the details as much as we can.
IOCs:
| SHA-1 | Application name | Package name | Package version | Developer |
|---|---|---|---|---|
| d8f941f6a8dbda39a881ad2a1661e3227e3f8f18 | App Lock Keep | com.enab.lockkeep | 1.0.6 | Sheralaw Rence |
| 8f30f3f176613dbc14aa29bfb3c952b6eb046da3 | Processing Photo | com.pcnts.splicingpp | 1.2 | chikumburahamilton |
| de2ac7091b7c51d0b7e1e9c31d5e8d9aa863aa5c | Rubbish Cleaner | com.snt.rubbishcleaner | 1.5.1 | SNT.rbcl |
| b2d07ac10bba9839fd8a0ccd7a7dcd08b508140b | Horoscope Daily | com.cgi.ygk.iozwrku.izgzw | 1.0 | HscopeDaily momo |
| de93c1c7a0c03ecf79179d2296008f93f48fdcaa | Horoscope Pi | com.iigxuq.xueqe.horoscopepi | 2.4.56 | Talleyr Shauna |
| d68717837c3b3ec7fd95a6b776ec96bef7344928 | App Lock Manager | com.oimjqcnw.mngyz.kqhcrpy.xdrzs | 007.xyz | Implummet col |
| 5a3d2917fe987dea35d1aa4b089743d168a71415 | Lockit Master | com.svbo.oypvn.otpl | 1.3 | Enali mchicolo |
| 903fcfba98f32b00badcec5976a4b401b994be7e | Inwell Fitness | chv.jrd.axiyby.ojs.xevjo | 1.1 | Reuben Germaine |
| f7d6462d16e8c0c81634e8812ae1b19a59bede26 | EditorPhotoPip | com.viewedites.showimg | 1.1 | Laurense |
| 2b931978aaee9e2a9d35b1f8bf35a9b89b74d2fa | PIP Photo | com.piphoto.pipsapp | 1.1.0 | Lillians |
| 8b0451ee56e8a5805b1c501d48066d2cb89e41a5 | PIP Photo | com.piphoto.pipsapp |
URLs:
data.applockkeep.xyzshop.vfgrl.comwap.inwellfitness.xyzcc.horoscopemagic.xyzmxi.applockmaster.xyzmm.superbrightflashlight.xyzwap.lockitmaster.xyzdata.horoscopedaily.xyz
IPs:
108.160.132.1545.32.110.28
Thanks for reading this post. Please share this post to all android users and create a awareness about the apps stealing Facebook password and this password stealing campaign.
You may also like these articles:
How to Protect Your Android Device From The New BrazKing Android Malware?
9 New Fake Apps on the Play Store Which Can Hijack SMS Notifications to Carry Out Billing Fraud
How Does FMWhatsApp Hack Your SmartPhones? What You Should Do To Prevent It?
Protect Your Android Phone From Malicious Apps On Huawei's AppGallery
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.