Table of Contents
Getting Started with Threat Modeling Using OWASP Threat Dragon
In an era of increasing cyber threats, organizations must continuously evolve their security strategies and tools to stay ahead of sophisticated attackers. Threat modeling has emerged as an indispensable process for systematically evaluating system architectures, assets, and vulnerabilities to proactively identify and remediate risks.
While threat modeling can be an arduous undertaking, the right frameworks and software tools can greatly simplify the process. One such tool is OWASP Threat Dragon, an intuitive, open-source threat modeling platform. In this post, we'll explore the value of threat modeling, provide an overview of Threat Dragon's capabilities, and demonstrate how to set up and use the tool to build effective threat models on both Windows and Linux systems.
Whether you're new to threat modeling or looking to improve your existing workflows, this guide aims to demystify the process and empower you to incorporate this critical security practice using a flexible, easy-to-use tool. Read on to learn how OWASP Threat Dragon can help your organization get ahead of threats and make more informed risk management decisions.
What is Threat Modeling?
Threat modeling is a security process where security professionals evaluate the environment to identify the assets and try to narrow down the possible threats and risks.
Threat modeling can be done either proactively or reactively and it is also important to note that it is not a onetime process and must be repeated periodically.
Threat modeling can be a very cumbersome activity to perform, and it is not a onetime activity. Therefore, the ideal way to perform a threat modeling would be to pick a specific area of operations. For example, Organizational level (covering physical controls, network, technical controls), Active directory and privilege access, Email security. By segregating, it becomes easier to narrow down on gaps and helps the security team to not miss out on potential vectors.
There are multiple benefits of performing threat modeling in an organization. Number one obviously being, addressing the security gaps and fixing any vulnerability. Following that would be the overall awareness that the team would get. Third would be the opportunity to liaise with multiple teams who are the stakeholders for different operations (For example, IT team, Network orations team, Unix/Linux team, DevSecOps team, etc.
Frameworks and tools:
Threat modeling can be conducted through the utilization of various established frameworks. Notable examples include MITRE ATT&CK, STRIDE, PASTA, DREAD, TRIKE, OCTAVE, and OWASP Top 10. To aid this process, a range of both paid and open-source tools are available. These tools, such as Threat Modeler, Irius Risk, OWASP Threat Dragon, Microsoft Threat Modeling Tool, and Mozilla Sea sponge, can be effectively employed to develop comprehensive threat models.
What is OWASP Threat Dragon?
In this blog, let us dive deep into one of the open-source tools called the OWASP Threat Dragon tool and see how it works, how to install it on Windows and Linux and create a basic Threat Model.
OWASP Threat Dragon provides a free, open-source, threat modeling application that is powerful and easy to use. It can be used for categorising threats using STRIDE, LINDDUN CIA, DIE and PLOT4ai.
There are a few advantages of the tool which makes this a good starting point for teams looking to get started with the Threat modeling for the first time.
Simplicity: The installation of the tool literally takes 5 minutes
Flexibility: the diagramming and threat generation allows all types of threat to be described.
Accessibility: Different types of teams can benefit from Threat Dragon’s simplicity and flexibility.
Setting up OWASP Threat Dragon in Windows Desktop:
Installing the Threat Dragon tool on windows desktop is a straightforward process.
Step 1: Download the Installer:
Go to the OWASP Threat Dragon page on the official OWASP website or the GitHub releases page to find the latest version of the tool.
Under "Assets", download the Windows installer executable file ending in
.exe. For example,ThreatDragon-1.4.1-Windows.exe.Take note of the location the file is saved to.
Step 2: Run the Installer
Navigate to and double-click the saved
.exeinstaller file to launch the setup wizard.You may get a security warning from Windows - click "Run" or "Yes" to allow the program to make changes to your system.
Step 3: Complete the Installation:
Follow the on-screen prompts from the Threat Dragon installer, including accepting the license agreement and choosing install options.
By default, Threat Dragon will be installed in
C:\Program Fileson most Windows environments.Leave default options unless you have specific needs to change install location, components etc.
Finally, check the box to launch Threat Dragon and click "Finish" to complete setup.
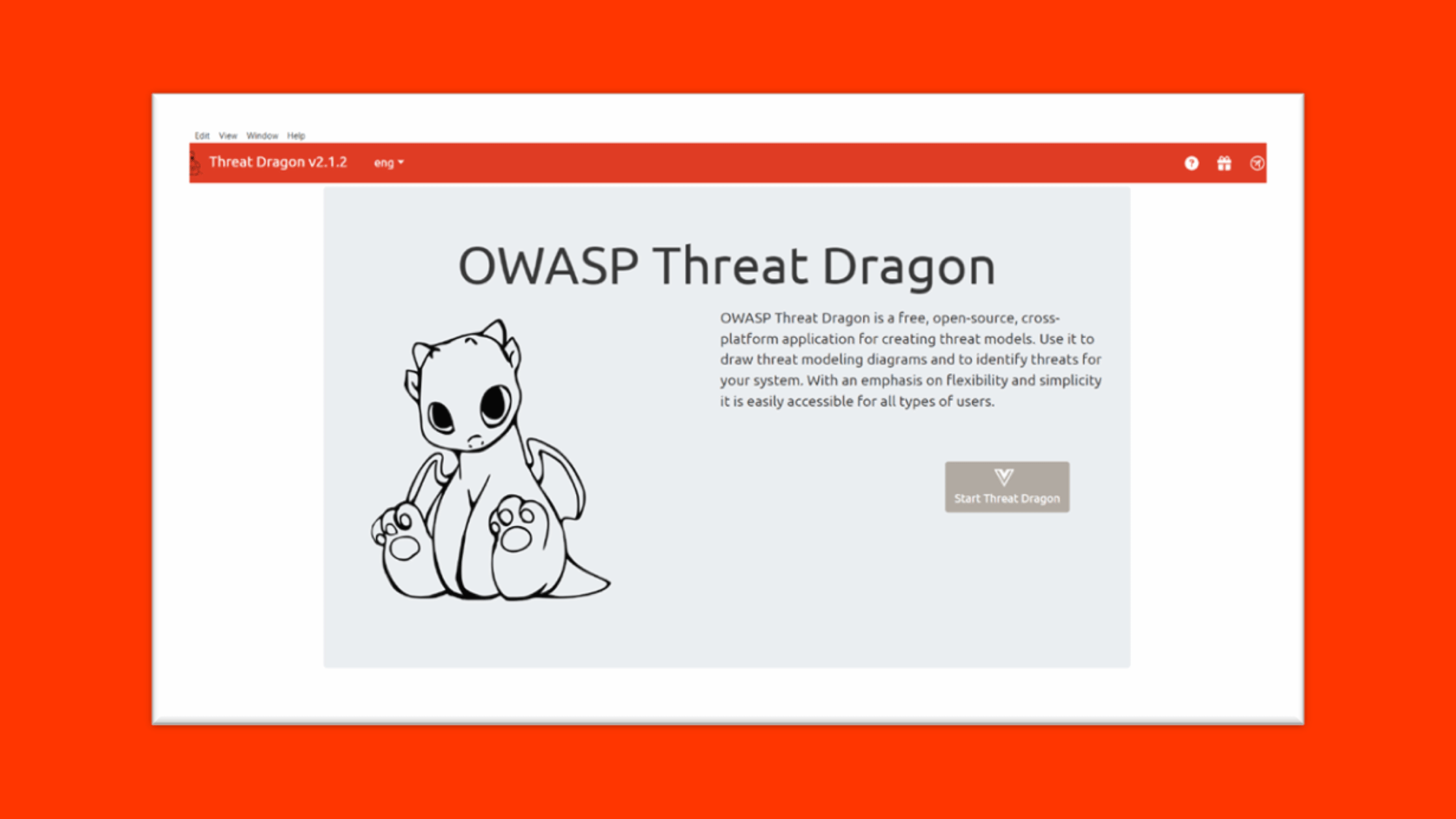
Step 4: Access OWASP Threat Dragon:
After finishing installation:
Threat Dragon may open automatically to a welcome screen with getting started resources.
If it does not launch, find Threat Dragon in your Windows Start menu or locate the shortcut created on your desktop.
Click the "Start Threat Dragon" button to begin threat modeling!
And that's it - Threat Dragon is now ready to use for threat modeling and risk analysis on your Windows machine!
Setting up OWASP Threat Dragon in Linux
Setting up TD on Linux entails following a process like that of Windows, with an additional permissions steps.
Before executing the AppImage installer, permissions need to be set:
In your file manager, right click the AppImage and open Properties.
Go to Permissions.
Check the box for "Allow executing file as program".
Close Properties and apply changes.
Double click the AppImage file to launch the installer.
Accept any security warnings and click OK/Yes if prompted.
In the Permissions section, select the “Allow this file to run as a program” and the execute the installer to launch the Threat Dragon tool.
Creating a Threat Model
Step 1: Components of Threat Dragon
In order to get started with the diagramming of the model, we would require components. The below diagram explains about the different stencils present and the possible components that could fall under these categories:
tep 2: Add Model Elements
When launching Threat Dragon, click the "+" icon to start a new threat model document.
Give your model a descriptive name at the top. For example "Acme Company Web Application".
On the left are stencil palettes with different categories of model elements. Drag elements onto the diagram canvas to represent parts of your system architecture. For example, databases, users, servers, networks, data flows, etc.
Arrange elements visually in a way that maps out your environment. Add text descriptions by double clicking elements.
Keep adding relevant elements until you have sufficiently detailed coverage of the system you are modeling.
Step 3: Connect Model Elements
Click the connection icon on the left toolbar to activate linking mode.
Click on an origin element, drag cursor to destination, and release to draw a connection. Add data flows, process flows, and trust boundaries.
Use connections to illustrate the relationships and interactions between components.
Step 4: Assign Threat Properties
Once we have completed diagramming the required model, the next step would be to assign threats properties to the components of the model based on any one of the frameworks supported by Threat Dragon and generate a report.
To do this, select the component and click on the “New Threat” option to assign threats and the appropriate severity for the same.
he environment and the organizational requirements, we can assign the threats.
For example,
the Database could store credentials that are not encrypted and could lead to Information Disclosure if compromised.
The Web server could receive abnormal requests and could cause denial of service, so on and so forth.
A threat model becomes mature when we can provide more detailed information and granularity to the model.
Step 5: Report Generation
Upon assigning threats to the components, its time to generate a report for the Threat model. This is a simple step.
Save the model and close the page.
It will be redirected to the home page of the Threat model.
On the bottom right corner of the page click on the “Report” option to generate a document
Step 6: Sample Report
The below diagram is an example of a sample report generate from the Threat Dragon tool. This is just the summary; in a real scenario a more detailed version is generated.
Conclusion
In summary, OWASP Threat Dragon provides an easy way to get started with the critical security practice of threat modeling. Its simplicity and flexibility make it accessible for teams looking to identify vulnerabilities and proactively improve their security posture.
We walked through installing Threat Dragon on both Windows and Linux systems, diagramming a sample system architecture, assigning threats, and generating reports. While basic, this example illustrates the intuitive workflows and useful outputs of the tool.
Threat modeling is an iterative process that takes time to master, but can pay huge dividends in risk reduction. OWASP Threat Dragon is a springboard into this practice - get started today with a small scope, then build up your models to cover broader systems over time. Integrate with complementary frameworks and tools to enrich models as they mature.
As threats become ever-more sophisticated, taking a proactive security stance is crucial. Threat modeling creates resilience by helping to identify - and therefore secure - the most vulnerable components before attackers do. Empower your team and reduce risk through workflows enabled by tools like OWASP Threat Dragon.
Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Aroma Rose Reji
Aroma is a cybersecurity professional with more than four years of experience in the industry. She has a strong background in detecting and defending cyber-attacks and possesses multiple global certifications like eCTHPv2, CEH, and CTIA. She is a pet lover and, in her free time, enjoys spending time with her cat, cooking, and traveling. You can connect with her on LinkedIn.