Table of Contents
Novel Zero-Day Attack Uses Corrupted Files to Bypass Security Tools and Spam Filters
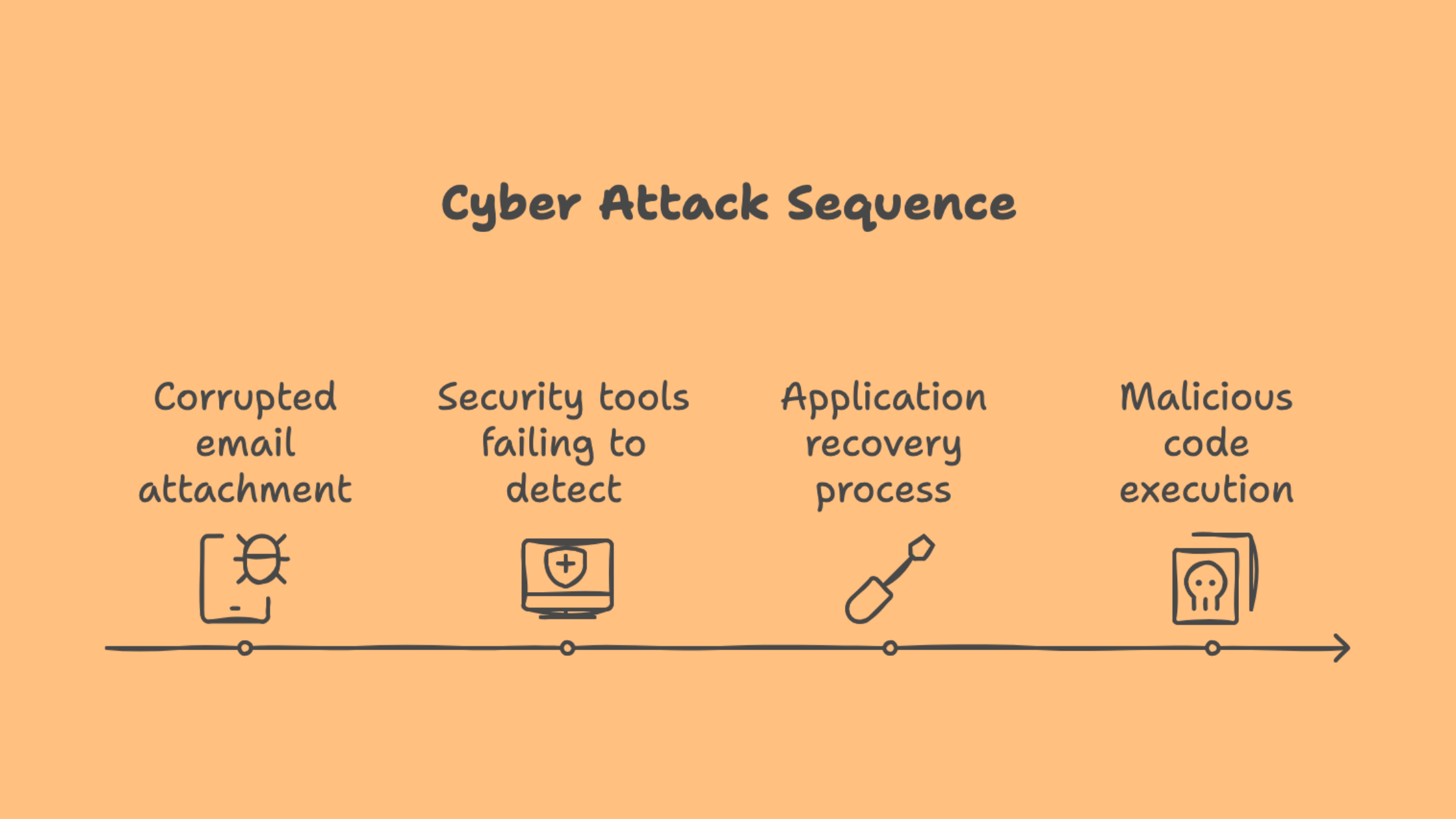
Security researchers have uncovered a sophisticated zero-day attack campaign that leverages deliberately corrupted files to evade detection by antivirus software, sandbox analysis tools, and email security filters.
The campaign, discovered by the ANY.RUN research team, demonstrates how attackers are exploiting file recovery mechanisms built into common applications like Microsoft Word, Outlook, and WinRAR to execute malicious code while remaining undetected by security solutions.
"What makes this attack particularly concerning is its ability to bypass multiple layers of security controls by manipulating how security tools process corrupted files," the researchers explained. "While security solutions fail to properly analyze these files, legitimate applications can still recover and execute them successfully."
How the Attack Works
The attack chain begins when victims receive malicious email attachments, typically masquerading as ZIP archives or Microsoft Office documents. However, these files have been deliberately corrupted in a way that:
Causes security tools to identify them as invalid or broken files
Prevents automated sandbox analysis systems from processing them
Allows legitimate applications to still recover and execute the malicious content using built-in file recovery mechanisms
A detailed analysis of one such attack can be found in ANY.RUN's sandbox report.
When security solutions attempt to scan these corrupted files, they typically:
Misidentify them as regular ZIP or Office files
Fail to properly extract and analyze the contents
Return "clean" or "item not found" results due to processing errors
However, when users open these files in applications like Microsoft Word, the software's built-in recovery features automatically repair and execute the malicious content, bypassing security controls entirely.
Widespread Security Impact
The research team found that this technique has been actively exploited in the wild since at least August 2024, with early instances documented in their threat analysis platform. Most concerning is that files using this method consistently receive "clean" verdicts when submitted to VirusTotal, indicating that major antivirus solutions are currently unable to detect them.
"This attack represents a concerning evolution in evasion techniques," said ANY.RUN researchers. "By exploiting the gap between how security tools and legitimate applications process corrupted files, attackers have found an effective way to bypass traditional security controls."
Detection and Mitigation
To help combat this threat, ANY.RUN has released detailed technical indicators and sample analysis of the attack. Organizations can access related sandbox sessions using the SHA256 hash in their TI Lookup tool.
Organizations are advised to:
Implement additional security controls beyond traditional antivirus
Consider blocking or quarantining files that trigger application recovery mechanisms
Train users to be suspicious of files requiring "repair" or "recovery" actions
Deploy advanced sandbox solutions capable of analyzing files in their intended application environment
Security teams can access more detailed analysis and indicators of compromise through ANY.RUN's threat intelligence platform. The research team continues to monitor this campaign and will provide updates as new information becomes available.
This attack serves as another reminder of how threat actors continue to innovate new ways to bypass security controls, highlighting the importance of defense-in-depth strategies and continuous security monitoring.
Found this article interesting? Keep visit our website thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.