Table of Contents
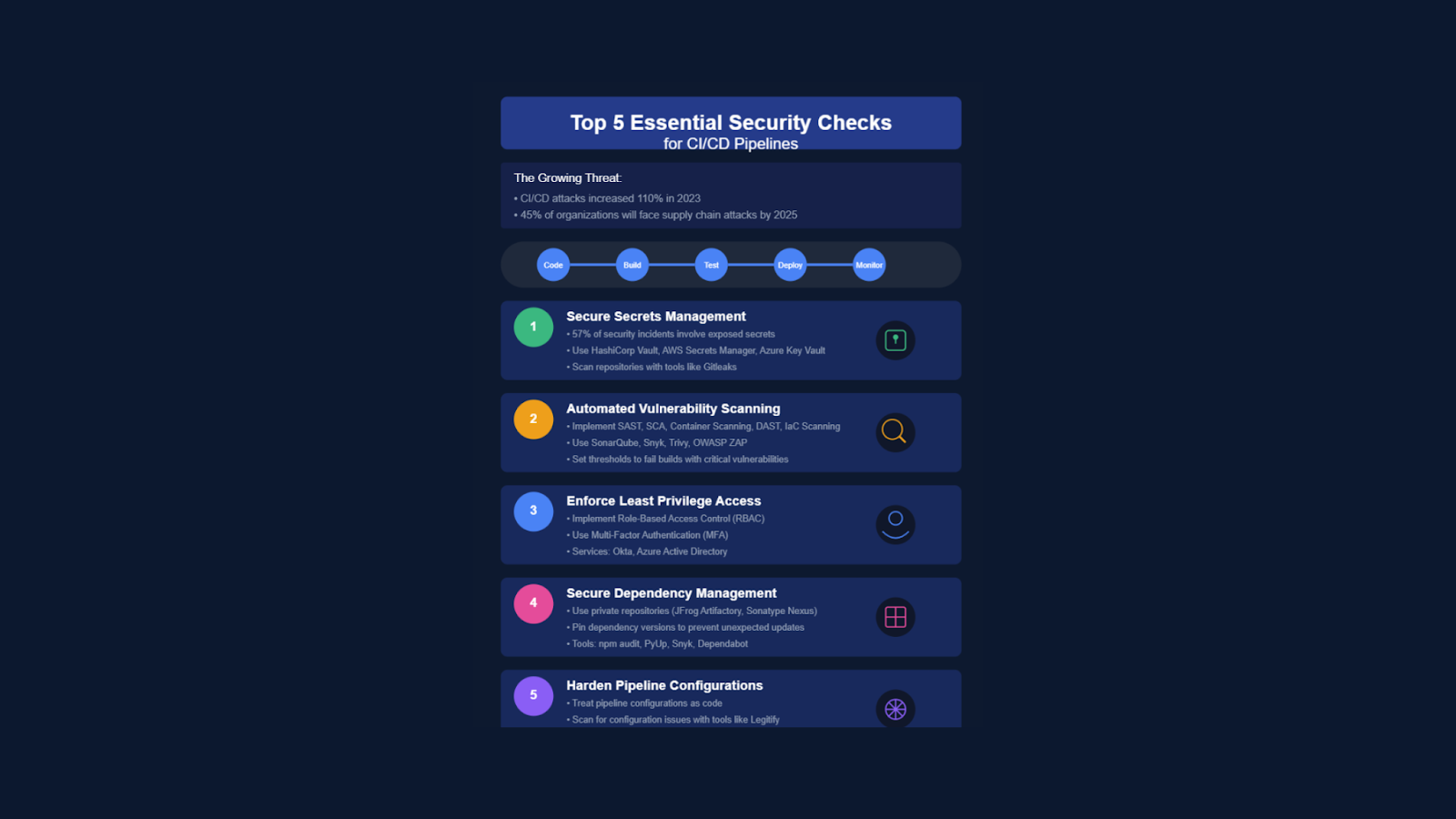
Top 5 Essential Security Checks for Your CI/CD Pipeline
In today's fast-paced software development world, Continuous Integration and Continuous Delivery (CI/CD) pipelines are the backbone of rapid deployment and iterative improvement. They enable teams to automate the software release process, delivering value to users faster than ever before. However, this speed and efficiency come with a significant security caveat: CI/CD pipelines are now prime targets for malicious actors. Think of them as unsupervised toddlers – initially charming, but destined for a chaotic escapade if left ungoverned. And in the world of CI/CD, that "chaos" translates to data breaches, system compromises, and reputational damage.
This blog post will explore the top 5 essential security checks you need to implement in your CI/CD pipeline to mitigate these risks and ensure the integrity of your software delivery process. Let's get started!
Why CI/CD Security Matters: A Growing Threat
The threat landscape is evolving rapidly. Cloud intrusions exploiting CI/CD vulnerabilities are skyrocketing, increasing by a staggering 110% year-over-year in 2023 (according to CrowdStrike). The time it takes for attackers to break out of an initial compromise is shrinking dramatically – down to a mere 62 minutes. This means security needs to be proactive, not reactive.
Ignoring CI/CD security is no longer an option. Gartner predicts that 45% of organizations will experience a software supply chain attack by 2025, highlighting the critical importance of securing your development processes. Neglecting security in this area has severe consequences, leading to data breaches, operational disruptions, eroded trust, and ultimately, significant business impact.
So, what exactly does CI/CD security entail? It's about securing the entire software delivery pipeline – from code repositories and build environments to deployment stages. This includes managing dependencies, handling secrets securely, and configuring your tools correctly to prevent exploitation. We need a solid incident response plan for any cyber incidents.
Let's dive into the essential checks.
1. Secure Secrets Management: Don't Let Credentials Become Public Knowledge
Hardcoded secrets – API keys, passwords, database credentials – are a CI/CD pipeline's Achilles' heel. They are the easiest way for attackers to gain unauthorized access to critical systems and data. A recent statistic revealed that over 57% of organizations have experienced security incidents due to exposed secrets in their DevOps processes. That’s more than half!
The Problem: Developers often inadvertently commit secrets directly into code repositories, making them accessible to anyone with access to the repo. This is a recipe for disaster.
The Solution: Implement a robust secrets management system. This means using dedicated tools like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault to store, access, and rotate secrets securely. Understanding symmetric and asymmetric encryption can help secure your secrets.
Pro Tip: Integrate your secrets management tool directly into your CI/CD pipeline. Use environment variables or secure injection methods to provide access to secrets only when needed. Never, ever hardcode secrets! Tools like Gitleaks can scan your repositories for accidentally committed secrets.
2. Automated Vulnerability Scanning: Catch Flaws Before They Explode
Vulnerabilities in your code and dependencies are like landmines waiting to explode in your production environment. Manual code reviews and security assessments are simply not enough to keep up with the pace of modern software development. Automated vulnerability scanning is essential for identifying and mitigating these risks early in the development lifecycle. It's important to know about CVSS.
The Problem: Relying solely on manual methods is time-consuming, error-prone, and cannot scale to meet the demands of rapid CI/CD pipelines. The risk of missing critical vulnerabilities is high.
The Solution: Integrate automated security scanning tools into your CI/CD pipeline. This includes:
Static Application Security Testing (SAST): Analyzes source code for potential vulnerabilities before compilation.
Software Composition Analysis (SCA): Identifies vulnerabilities in open-source libraries and third-party dependencies.
Container Image Scanning: Scans container images for OS vulnerabilities, misconfigurations, and embedded secrets.
Dynamic Application Security Testing (DAST): Tests the running application for vulnerabilities by simulating real-world attacks.
Infrastructure as Code (IaC) Scanning: Analyzes infrastructure configuration files (e.g., Terraform, CloudFormation) for security misconfigurations.
Pro Tip: Shift security left by integrating SAST tools into developer IDEs and pre-commit hooks. Use tools like SonarQube, Snyk, Trivy, and OWASP ZAP to automate vulnerability scanning. Set thresholds to automatically fail builds when critical vulnerabilities are detected. Dependency scanning with tools like Dependabot and OWASP Dependency-Check can identify vulnerable components.
3. Enforce Least Privilege Access: Limit the Blast Radius
The principle of least privilege (POLP) is a fundamental security concept that states that users and systems should only have access to the resources they need to perform their job duties. In the context of CI/CD pipelines, this means limiting access to code repositories, build environments, deployment stages, and sensitive data. Understand the role of file ownership.
The Problem: Overly permissive access can allow attackers to compromise the entire pipeline if they gain access to a single account or system. This increases the blast radius of a potential breach.
The Solution: Implement Role-Based Access Control (RBAC) and grant users and systems only the minimum necessary permissions. Regularly audit user access and remove unnecessary privileges. Use Multi-Factor Authentication (MFA) to protect accounts from unauthorized access.
Pro Tip: Use a centralized identity and access management (IAM) system to manage user access across the CI/CD pipeline. Implement strong password policies and enforce MFA for all users. Employ network segmentation to isolate different environments (dev, staging, prod) and limit lateral movement in case of a breach. Services like Okta and Azure Active Directory can provide robust IAM capabilities.
4. Secure Dependency Management: Know What You're Bringing In
Modern software development relies heavily on third-party libraries and dependencies. These components can introduce significant security risks if they are not properly managed. Malicious packages and outdated libraries with known vulnerabilities are a common source of CI/CD pipeline breaches.
The Problem: Attackers can exploit vulnerabilities in dependencies to inject malicious code into your applications. Dependency confusion attacks, where attackers create public packages that mimic internal library names, can also compromise your build process.
The Solution: Implement a robust dependency management strategy. This includes:
Using private repositories to store and manage dependencies.
Prioritizing internal sources over public repositories.
Scanning dependencies for vulnerabilities using SCA tools.
Pinning dependency versions to prevent unexpected updates.
Regularly auditing third-party libraries and removing unused dependencies.
Pro Tip: Use tools like npm audit, PyUp, and Snyk to scan dependencies for vulnerabilities. Consider using a private repository manager like JFrog Artifactory or Sonatype Nexus to control access to dependencies and enforce security policies. Regularly audit third-party libraries using tools like Dependabot and OWASP Dependency-Check.
5. Harden Pipeline Configurations: Treat Infrastructure as Code Securely
Misconfigurations in your CI/CD tools and infrastructure can create significant security holes. These misconfigurations can expose sensitive data, allow unauthorized code injection, and leave your pipeline vulnerable to attacks.
The Problem: Misconfigured tools and infrastructure can provide attackers with an easy entry point into your CI/CD pipeline. These misconfigurations often go unnoticed until it's too late.
The Solution: Treat your pipeline configurations as code. This means version controlling your configurations, reviewing them regularly, and using automated scanning tools to detect misconfigurations. Security misconfiguration can create significant security holes.
Pro Tip: Use static analysis tools to scan your pipeline configurations for security issues. Implement hardening guidelines for your CI/CD tools and infrastructure. Regularly audit your configurations to ensure they are compliant with security policies. Tools like Legitify can enforce security policies across your CI/CD pipeline. Regularly audit your settings to ensure all components have appropriate security settings and are up-to-date. This includes analyzing Infrastructure as Code (IaC) with tools like Trivy.
Beyond the Top 5: Continuous Improvement
Securing your CI/CD pipeline is not a one-time fix. It's an ongoing process that requires continuous improvement and vigilance. In addition to the top 5 security checks listed above, consider implementing the following best practices:
Enable Comprehensive Logging and Monitoring: Capture all CI/CD activities and monitor for anomalies. Security logging is crucial for identifying anomalies.
Develop an Incident Response Plan: Prepare for security incidents and have a plan in place to respond quickly and effectively.
Enforce Continuous Compliance: Ensure your pipeline processes and components meet relevant policies, regulations, and standards.
Shifting Left: Embrace a Proactive Security Posture
The key to securing your CI/CD pipeline is to "shift left," meaning to integrate security into every stage of the development lifecycle. By proactively addressing security risks early on, you can prevent costly and disruptive breaches down the line. Embrace security as an enabler of reliable and trustworthy software delivery. It's not about slowing down development; it's about mitigating risks and building secure software from the start. Understand the MITRE ATT&CK framework.
By implementing these top 5 essential security checks, you can significantly reduce your risk of a CI/CD pipeline breach and ensure the integrity of your software delivery process. Remember, security is a journey, not a destination. Continuously assess your security posture, adapt to evolving threats, and invest in the tools and processes you need to stay ahead of the curve. The security of your CI/CD pipeline is not just a technical issue; it's a business imperative. You can use Kali Linux for security purposes.
Found this article interesting? Keep visit thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive tips like this.
You may also like these articles:
• How To Fix CVE-2022-20732- A Privilege Escalation Vulnerability In Cisco VIM
• Step-by-Step Guide to Setup PyTorch for Your GPU on Windows 10/11
• 5 Best Open-Source Tools to Monitor Containers
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.