Table of Contents
5 Step Strategy to Implement Micros Segmentations
In the early days of networking, people struggled to simply connect computers together. Today, the challenge has shifted to protecting those connected computers from cyber threats. With the growing technology and cyber threats, it has become increasingly difficult task for security architects and engineers to design robust security systems that can combat modern cyber risks.
A couple of decades ago, security architects started using a perimeter security model to design security systems. This is now considered a more traditional or conventional approach that may soon become obsolete because of its limitations. Many organizations and security architects are moving towards a zero trust architecture (ZTA) model instead. Microsegmentation is one of the key strategies used to implement a zero trust model. Let’s dive into the challenges with the perimeter security model, how ZTA addresses those challenges, what microsegmentation is, how it works, strategies to deploy it, the benefits it offers, and a real-world example.
What is Perimeter Security Model And Challenges With Perimeter Security Model?
“North-south” (client to server) traffic vs. “east-west” (workload to workload) Source: PaloAlto
The perimeter security model sets up a hardened boundary around an organization’s internal trusted network using security controls like firewalls, VPNs, IDS/IPS, and web proxies.
The goal of these perimeter controls is to create a line of defense that blocks untrusted traffic from entering the internal trusted network. Anything inside the perimeter is implicitly trusted under this model. Once inside the secured perimeter, an attacker has relatively unrestricted lateral movement capabilities across the network. Since east-west traffic inside the network is not inspected or restricted, attackers can easily pivot between workloads and assets.
Perimeter security model was effective for traditional static corporate networks. There are some limitations with perimeter security model that imposes several challenges to the dynamically changing infrastructures.
It provides a false sense of security inside the perimeter. If an attacker breaches the perimeter defenses, they have broad access to sensitive assets.
It is less effective for dynamic cloud environments and mobile workforces where the network perimeter is porous and fluid.
The rapidly growing volume of east-west traffic inside the perimeter is left uninspected as a blind spot.
There is no identity or context associated with internal traffic flows between workloads.
When breaches occur, it can be challenging to determine the blast radius and respond effectively.
It leaves organizations vulnerable to insider threats, compromised credentials, and brute force attacks. A malicious insider or stolen credentials can bypass the perimeter.
Meeting compliance regulations can be difficult without granular controls and visibility into internal traffic.
Secure configuration and patching of internal assets is often lax compared to hardened perimeter systems.
As per the Colortokens blog post, perimeter security is akin to a castle model. Once the outer walls are breached, attackers have free reign inside. More granular inner defenses are needed to limit lateral movement.
The shortage of visibility and controls around east-west traffic flows is a critical gap with perimeter security designs. As traffic inside the network grows exponentially, unrestricted lateral movement leaves organizations highly vulnerable.
What is Zero Trust Architecture Model and How Does it Addresses the Limitations of Perimeter Security Model?
The zero trust architecture (ZTA) model provides an alternative approach that addresses the limitations of perimeter-based security designs.
ZTA is based on the principle of “never trust, always verify”. It enforces strict access controls for all traffic – whether inside or outside the network perimeter. Access decisions are based on parameters like user identity, device security posture, and other dynamic variables.
Microsegmentation and least privilege access are core components of ZTA. By dividing the network into small, isolated segments with restricted traffic between them, lateral movement is limited in the event of a breach.
Key benefits of adopting a ZTA model include:
Improved security for cloud environments and distributed networks where the perimeter is porous.
Better protection against compromised credentials and insider threats.
Increased visibility into east-west traffic flows for detection and response.
More effective containment of breaches to small blast radiuses.
Simplified regulatory compliance through workload isolation and controls.
Security policies based on identity not network location.
Network looks with micro segmentation Source: PaloAlto
By leveraging microsegmentation and not relying solely on hardened network perimeters, ZTA provides more flexible, granular security across heterogeneous environments. It aligns better to modern hybrid cloud and mobile environments.
While ZTA involves a strategic shift, it can be deployed incrementally. Starting with high value workloads and expanding over time is a pragmatic approach. Microsegmentation serves as the technical mechanism for organizations to start limiting trust and implementing least privilege controls at a workload level.
For organizations looking to strengthen security in hybrid cloud environments with porous perimeters and unrestricted east-west traffic flows, ZTA principles enabled by microsegmentation offer a more adaptive trust model.
Defining Micro Segmentation and Workloads
Micro segmentation involves dividing an organization’s infrastructure into small, isolated segments and applying granular security controls between them. These isolated zones restrict communication and access based on the principle of least privilege.
Micro segmentation solutions leverage workload attributes and identities to define security policies, rather than relying solely on traditional constructs like IP addresses, ports and protocols.
A workload refers to any component that consumes compute resources, such as:
Physical servers
Virtual machines
Containers
Serverless functions
Databases
Workloads often power business applications and services. Micro segmentation secures them individually by restricting lateral communication between workloads.
For example, a web server workload may only need to talk to an app server workload over HTTP/HTTPS. A micro segmentation policy would explicitly allow this traffic while blocking other protocols.
Micro segmentation creates a zero trust architecture within environments. It provides deep visibility into east-west traffic flows between workloads. Granular segmentation policies are layered on top of this visibility to minimize potential lateral movement in the event of a breach.
By decoupling security policy from the underlying network and infrastructure, micro segmentation delivers consistent protection for workloads regardless of whether they are on-premises, in the cloud, containers, etc. Policies follow workloads automatically.
Benefits of Microsegmentation
Deploying microsegmentation strategies offers organizations several important security and compliance benefits:
1. Reduced Attack Surface
Microsegmentation minimizes potential attack paths by restricting communication between workloads. Segmenting networks down to the individual workload level reduces the lateral surface area attackers can exploit.
2. Improved Breach Containment
By isolating workloads into secure zones, any compromise is limited to a small blast radius. Microsegmentation policies prevent threats from spreading laterally across the network.
3. Consistent Security Across Environments
Microsegmentation enables consistent workload-centric security policies to be applied across hybrid cloud environments. Workload security travels with the asset as it moves.
4. Greater Regulatory Compliance
Organizations can isolate regulated workloads and data into compliant zones. Microsegmentation simplifies meeting regulations like PCI DSS, HIPAA, and GDPR.
5. Simplified Security Policy Management
Microsegmentation aligns to workload identities and requirements. This enables more intuitive policy management compared to traditional IP-based network security rules.
Additional advantages include better visibility into east-west traffic, improved insider threat protection, accelerated breach response, and automated policy adjustments as applications change. By adopting a microsegmentation strategy, organizations can implement workload-focused security that is more scalable, flexible, and aligned to modern hybrid cloud
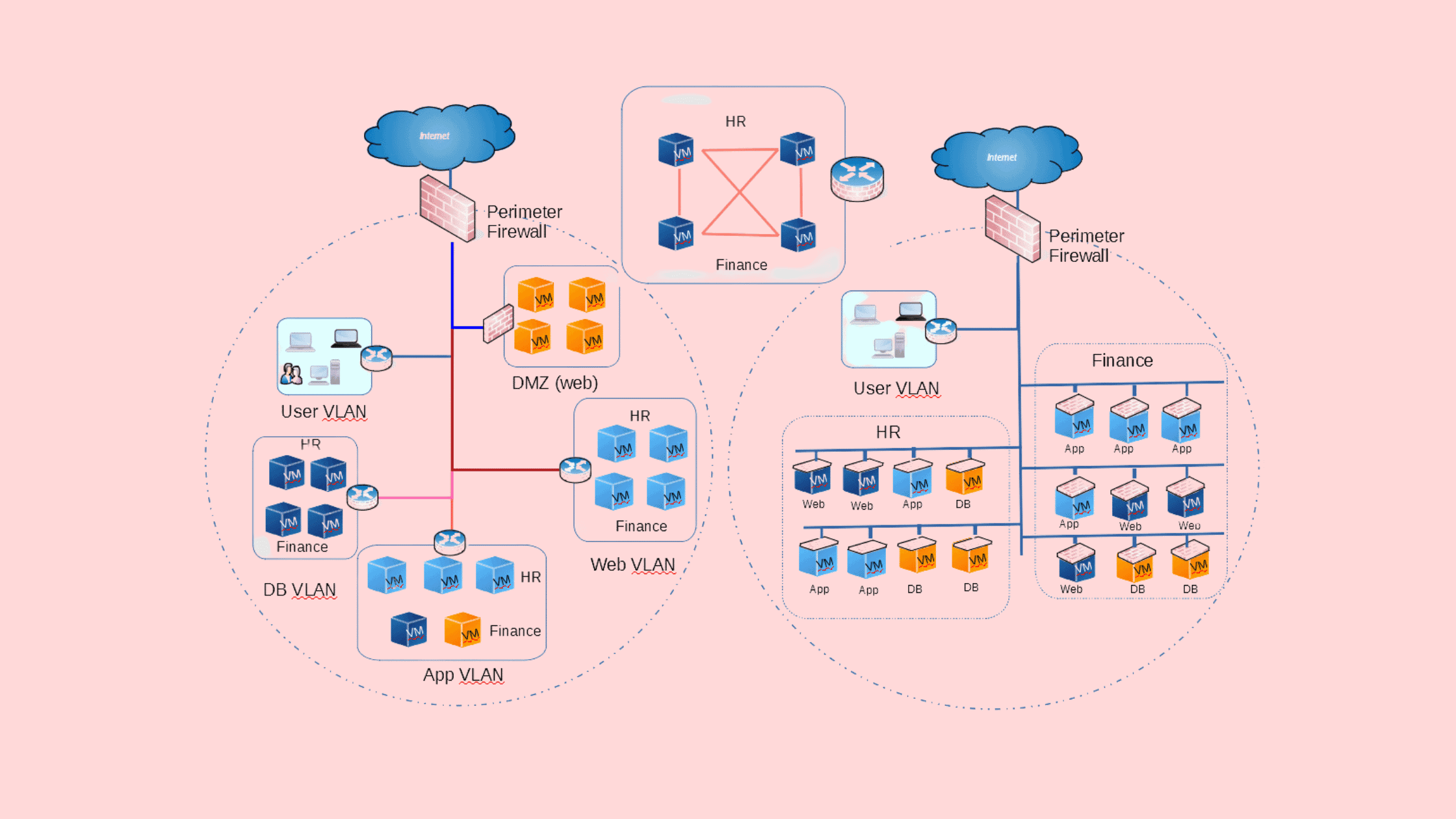
Best Strategy to Implement Micros Segmentations
Granular zones or workloads Source: PaloAlto
Implementing effective micro segmentation requires careful planning and execution. We follow five steps approach to implement Micro Segmentations. Let’s explore all five phases one after another:
Phase 1: Define and Classify Workloads
First, you need to define and classify your workloads. Carefully analyze your infrastructure and categorize workloads based on factors like location, data center, environment, network, departments, assets, applications, processes, and users or user groups. The goal is to develop a clear understanding of the various types of workloads across your infrastructure.
Phase 2: Label Workload
Second, create descriptive labels for each defined workload and associated entities. For example, you may label a workload for your customer database as “Prod DB Workload East Coast”. Precise labeling sets the foundation for the next steps.
Phase 3: Create Zones
Third, use the labels to establish granular zones for segmentation. Define zone boundaries based on workload types, environments, security levels and other relevant factors. For example, you may have distinct zones for development workloads, production databases, internal applications, and external facing services.
Phase 4: Define Granular Access Policies
Fourth, specify security controls appropriate for each zone. A zone containing highly sensitive data may require stricter controls compared to an internal application zone. Outline required security capabilities like encryption, access restrictions, or network microsegmentation firewalls.
Phase 5: Implement Microsegmentation Controls
Finally, convert the defined zone-based security controls into implementable security policies and rules. Deploy these policies through your microsegmentation solution to actively enforce segmentation between workloads and resources. Maintaining updated policies ensures alignment with evolving workload classifications.
We recently followed this five-step approach when implementing microsegmentation for a UK-based telecommunications company. Defining workload types, labeling entities, establishing granular zones, specifying zone-based controls, and deploying policies enabled successful microsegmentation aligned with a zero trust model. Careful planning and phased execution allows you to implement effective microsegmentation across complex environments.
A Real World Implementation of Micro Segmentations
To demonstrate our five-step microsegmentation approach in action, we will overview an implementation for a UK-based telecommunications client. This client operates three data centers in Manchester, Wakefield, and Northampton, along with an additional presence on AWS Cloud.
We began by logically segmenting each data center into multiple environments: Production, Pre-Production, Development, Test Bed, Common Services, Storage, Infrastructure Applications, and more. Underneath each environment, we created further network segments like subnets, VLANs, and cloud tenants. We then segmented within networks by assets, applications, processes, and user groups. Finally, we established granular segmentation of individual services on assets, such as SSH, SFTP, and other ports.
To illustrate, sample workloads were defined as:
| Sl. No | Location | Data Center | Environment | Network | Asset | Application | Process | Users/Groups |
|---|---|---|---|---|---|---|---|---|
| 1 | Manchester | DC01 | Production | Net01 | Ser01 | App01 | Proc01 | Admins |
| 2 | Wakefield | DC02 | Pre-Prod | Net02 | Ser02 | App02 | Proc02 | Users |
With workloads defined, we moved to labeling each entity using a logical convention. For example:
| Sl. No | Location | Data Center | Environment | Network | Asset | Application | Process | Users/Groups | Label |
|---|---|---|---|---|---|---|---|---|---|
| 1 | Manchester | DC01 | Production | Net01 | Ser01 | App01 | Proc01 | Admins | Prod-DC01-App01 |
| 2 | Wakefield | DC02 | Pre-Prod | Net02 | Ser02 | App02 | Proc02 | Users | PreProd-DC02-App02 |
Labels established the foundation to create granular zones for microsegmentation. We aligned zones to workload types, environments, security tiers, and other factors.
Next, we defined appropriate security and access controls like allow or deny between zones or workloads. Controls were tailored to workload risk levels and security priorities.
Finally, we implemented definable policies in our microsegmentation solution to actively enforce zoning and security and access controls. Ongoing policy administration maintains alignment as workloads and priorities evolve.
This example demonstrates our approach to methodically plan, label, zone, control, and policyize microsegmentation step-by-step. The result was a successfully implemented microsegmentation architecture following zero trust principles across the client’s multi-site hybrid environment.
Bottom Line
Traditional network perimeter security models are no longer sufficient in today’s cloud-centric environments with porous edges and exponential east-west traffic growth. While hardening the network boundary provided a measure of protection historically, unrestricted lateral movement once inside leaves modern organizations highly vulnerable.
The zero trust architecture paradigm combined with microsegmentation techniques offers a more adaptive model for the future. By separating security controls from the physical network and aligning them to workload identities, microsegmentation enables granular segmentation that follows workloads across heterogeneous environments.
With comprehensive workload discovery, standardized labeling, least privilege zoning, and adaptive policy enforcement, microsegmentation allows organizations to shrink their attack surfaces, limit blast radiuses, and consistently apply security despite constant infrastructure change.
Zero trust principles of identity-based verification and least privilege access are codified into the fabric of the environment with microsegmentation, not just at the edge. This secures organizations from compromised credentials, insider threats, cloud security gaps, and exposure from excessive intra-application communications.
Microsegmentation does require additional architectural planning compared to perimeter models. But for security leaders looking to enable business velocity while securing dynamic hybrid cloud infrastructures, it provides a powerful mechanism for reducing risk. By combining microsegmentation with cloud-native security tools and practices, modern enterprises can confidently innovate while protecting their most critical digital assets and data.
We hope this article helped in understanding perimeter security, its limitations, how does Zero Trust Architecture and micro segmentation addresses the challenges of perimeter security. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.