Table of Contents
Understanding the Components of Splunk Platform
If you read our previous article about Splunk, you might have gotten some idea about the components of Splunk. However, that was just an introduction. You definitely deserve to learn more about Splunk components in greater detail.
In this article, we've got the components of Splunk covered more extensively. We'll dive deeper into each component, exploring their functions and roles within the Splunk ecosystem. Understanding these components is crucial for anyone aspiring to work as a Splunk administrator or architect. So, let's get started!
What are the Components of Splunk Platform?
Splunk is composed of multiple components, each with its unique functions. To work effectively as a Splunk administrator, it's essential to have a deep understanding of each component and its core functionalities.
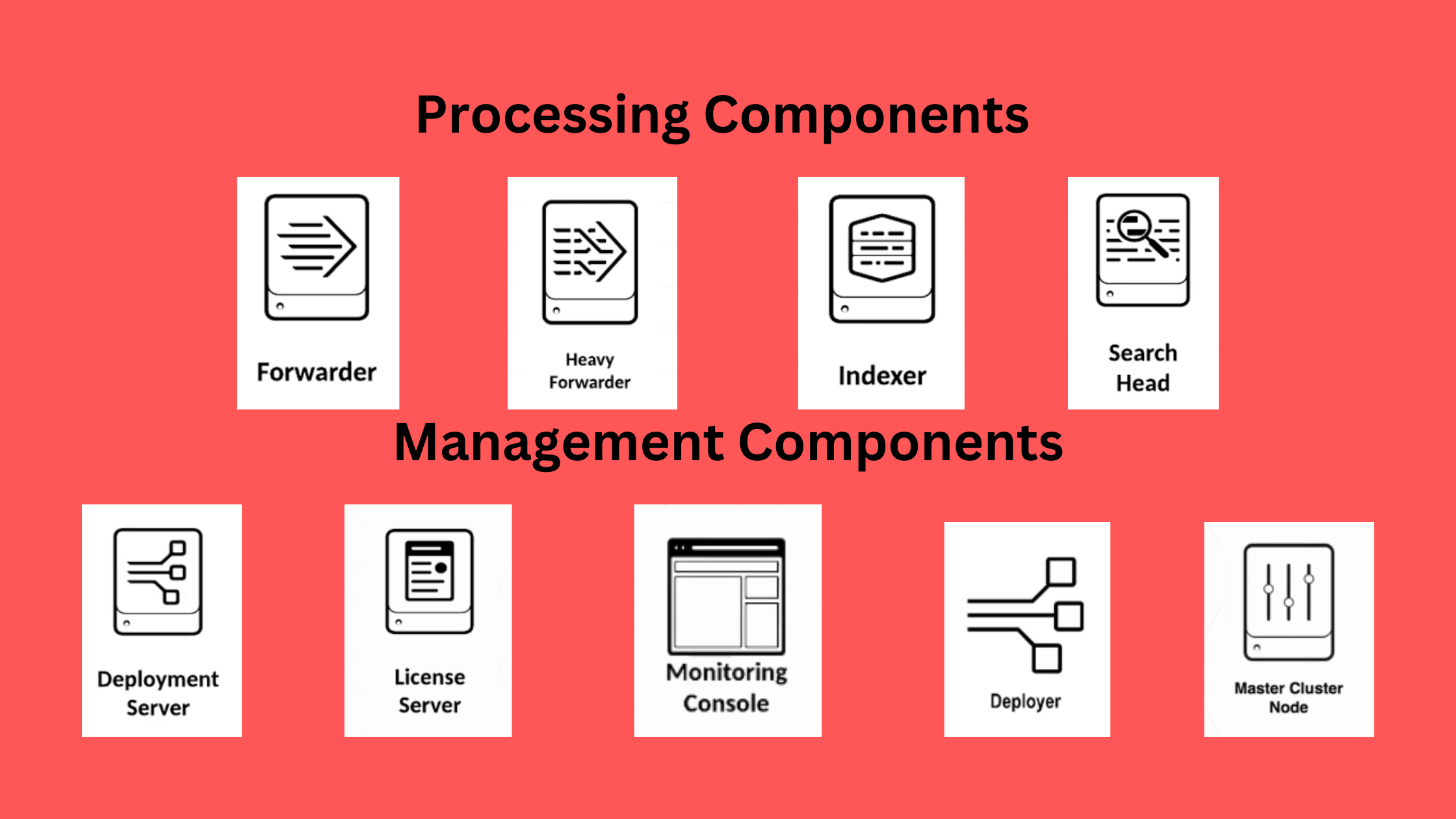
These components are categorized into two main groups: Processing Components and Management Components. The Processing Components handle the data and include the Forwarder, Indexer, and Search Head. On the other hand, the Management Components support the activities of the Processing Components and consist of the Deployment Server, License Server, Master Cluster Node, Deployer, and Monitoring Console.
It's important to note that these components don't come in separate installation packages. Instead, they are all part of a single Splunk installation package. The specific role of each component is determined by how you configure the package. Let's explore each component in more detail.
Universal Forwarder
The Universal Forwarder is a lightweight agent that you deploy on various IT systems to collect logs and send them to another Splunk Enterprise instance for processing. It is designed to be fast and resource-efficient, with a minimal footprint on the host system.
The Universal Forwarder package is relatively small, typically around 28 megabytes, as it doesn't include a user interface or support for Python. Its primary purpose is to collect logs and forward them in an uncooked state, meaning the data is not parsed or processed on the forwarder itself.
The Universal Forwarder is considered the best data collection method and the most common way to get data into Splunk. In large-scale environments, it is the preferred choice due to its efficiency and scalability. Additionally, there is no license required for the Universal Forwarder, making it a cost-effective solution.
Heavy Forwarder
The Heavy Forwarder is a full Splunk Enterprise instance that can index, search, and change data, as well as forward it to other Splunk instances. Unlike the Universal Forwarder, the Heavy Forwarder has the capability to parse and index data before forwarding it.
One key difference between the Heavy Forwarder and the Universal Forwarder is that the Heavy Forwarder includes Python packages and supports a user interface. It is essentially a full-blown Splunk instance with the added functionality of data forwarding.
When data is sent from a Heavy Forwarder to an indexer, the indexer does not parse the data again. The data is received in a cooked state, meaning it has already been processed by the Heavy Forwarder. This allows the indexer to skip the parsing pipeline and directly ingest the data.
Heavy Forwarders are used in scenarios where additional processing or transformation of data is required before forwarding. They can run Splunk add-ons to receive data from external resources and perform data forwarding and parsing. However, Heavy Forwarders have a larger footprint compared to Universal Forwarders and require a license.
Indexer
The Indexer is responsible for transforming the received data into events, unless it was pre-processed by a Heavy Forwarder. It stores the data on disk and adds it to an index, enabling searchability.
During the indexing process, the Indexer creates various files and organizes them into directories called buckets. These files include the compressed raw data as received, indexes pointing to the raw data for fast search ability, and metadata files that annotate the logs with source and source type information.
The Indexer performs generic event processing on the log data, breaking it into events and extracting relevant fields. This process makes the data searchable and facilitates efficient querying and analysis.
License Server
The License Server acts as a centralized license repository for Splunk Enterprise licenses. It manages and distributes licenses to other Splunk components in the deployment.
With the License Server, you can define license pools and stacks, allowing for efficient allocation and tracking of licenses across your Splunk environment. It ensures that all components have the necessary licenses to operate and helps maintain compliance with licensing requirements.
Search Head
The Search Head provides the user interface for users to submit searches using the Splunk Processing Language (SPL). It allows users to search and query Splunk data, enabling them to explore and analyze the indexed data.
The Search Head provides a distributed search architecture, allowing you to scale up and handle large data volumes. It distributes search requests to the indexers and consolidates the results for presentation to the user.
In a distributed deployment, multiple Search Heads can be deployed to handle user load and provide high availability. Users interact with the Search Heads to perform searches, create dashboards, and visualize data.
Deployment Server
The Deployment Server acts as a centralized configuration manager for Splunk forwarders. In large-scale deployments with hundreds or thousands of forwarders, managing them individually can be tedious and time-consuming.
The Deployment Server simplifies the management of forwarders by providing a centralized interface. It allows you to deploy apps, configuration files, and updates to the forwarders remotely. Forwarders, such as Universal Forwarders and Heavy Forwarders, periodically check-in with the Deployment Server to retrieve any updates or changes.
By using the Deployment Server, you can easily manage and maintain consistency across your forwarder infrastructure, ensuring that all forwarders have the necessary configurations and apps to collect and forward data efficiently.
Monitoring Console
The Monitoring Console is a tool that provides a detailed overview of the topology and performance of your Splunk Enterprise deployment. It offers a centralized dashboard where you can monitor the health and status of various Splunk components.
With the Monitoring Console, you can view information about search heads, cluster masters, deployment servers, and license masters. It provides insights into CPU performance, memory usage, and other key metrics, allowing you to identify any potential issues or performance bottlenecks.
The Monitoring Console helps you proactively monitor your Splunk infrastructure, ensuring that all components are running smoothly and efficiently. It can be deployed separately in large-scale environments or combined with the cluster master node if sufficient resources are available.
Deployer
The Deployer is a Splunk Enterprise instance used to distribute apps and configuration updates to search head cluster members. It serves a similar purpose to the Deployment Server but is specifically designed for managing search head clusters.
The Deployer distributes configuration bundles, which contain apps and configuration files, to all the search head nodes in the cluster. It ensures that all search heads have consistent and up-to-date configurations, simplifying the management of search head clusters.
By using the Deployer, you can easily deploy and manage apps and configurations across multiple search heads, maintaining a synchronized and harmonized search experience for users.
Cluster Master
The Cluster Master plays a vital role in managing and regulating the functioning of indexers in a Splunk indexer cluster. Its primary purpose is to ensure data replication and maintain multiple copies of data across the indexers.
In an indexer cluster, the Cluster Master coordinates the replication of data between the indexers. It monitors the health and status of the indexers and ensures that data is consistently replicated and available.
By leveraging the Cluster Master, you can achieve high availability and disaster recovery in your Splunk deployment. If one indexer goes down, the Cluster Master ensures that the data is still accessible from other indexers in the cluster. It helps eliminate single points of failure and provides a resilient and fault-tolerant architecture.
The Cluster Master also manages the data replication process, optimizing the distribution of data across the indexers. It ensures that data is evenly distributed and that the indexers are efficiently utilized.
Conclusion
Understanding the components of the Splunk platform is crucial for effectively managing and leveraging its capabilities. From the Universal Forwarder and Heavy Forwarder for data collection to the Indexer for data processing and the Search Head for querying and analysis, each component plays a vital role in the Splunk ecosystem.
The Management Components, such as the Deployment Server, License Server, Monitoring Console, Deployer, and Cluster Master, provide essential functionalities for configuration management, license distribution, monitoring, and cluster management.
By having a deep understanding of these components and their roles, Splunk administrators and architects can design and deploy efficient and scalable Splunk environments. They can optimize data collection, ensure data availability and reliability, and provide a seamless user experience for searching and analyzing data.
Remember, all these components come as part of a single Splunk installation package, and their specific roles are determined by how you configure them. This flexibility allows you to tailor your Splunk deployment to meet your organization's specific requirements and scale as needed.
As you continue your journey with Splunk, keep exploring and learning about these components. The more you understand their functionalities and how they interact with each other, the better equipped you'll be to harness the full potential of the Splunk platform.
We hope this article helps understand different components of Splunk. We are going to end this article for now, however there are more articles to come covering more advanced topics on Splunk. Please keep visiting thesecmaster.com for more such technical information. Visit our social media page on Facebook, Instagram, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive information like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.