Table of Contents
A Checklist for An Incident Response Life Cycle
If you are working in IT infrastructure teams, especially in Security Operations like SOC, CIRT, PSIRT, CRC, DevSecOps, and Security Auditing teams, understanding of incident response process is mandatory. A security team without the knowledge of the incident response process never be able to handle security incidents- it's like a body with no soul. The Incident Response Life Cycle is the backbone of the incident response process. The Incident Response Life Cycle is a must to know to respond to security incidents.
Every organization must prepare their security teams with a full proof CIRP (Cyber Incident Response Plan) to respond to incidents swiftly and effectively to mitigate the potential damage caused by these incidents. The incident response life cycle provides a structured approach to handle security breaches and minimize their impact.
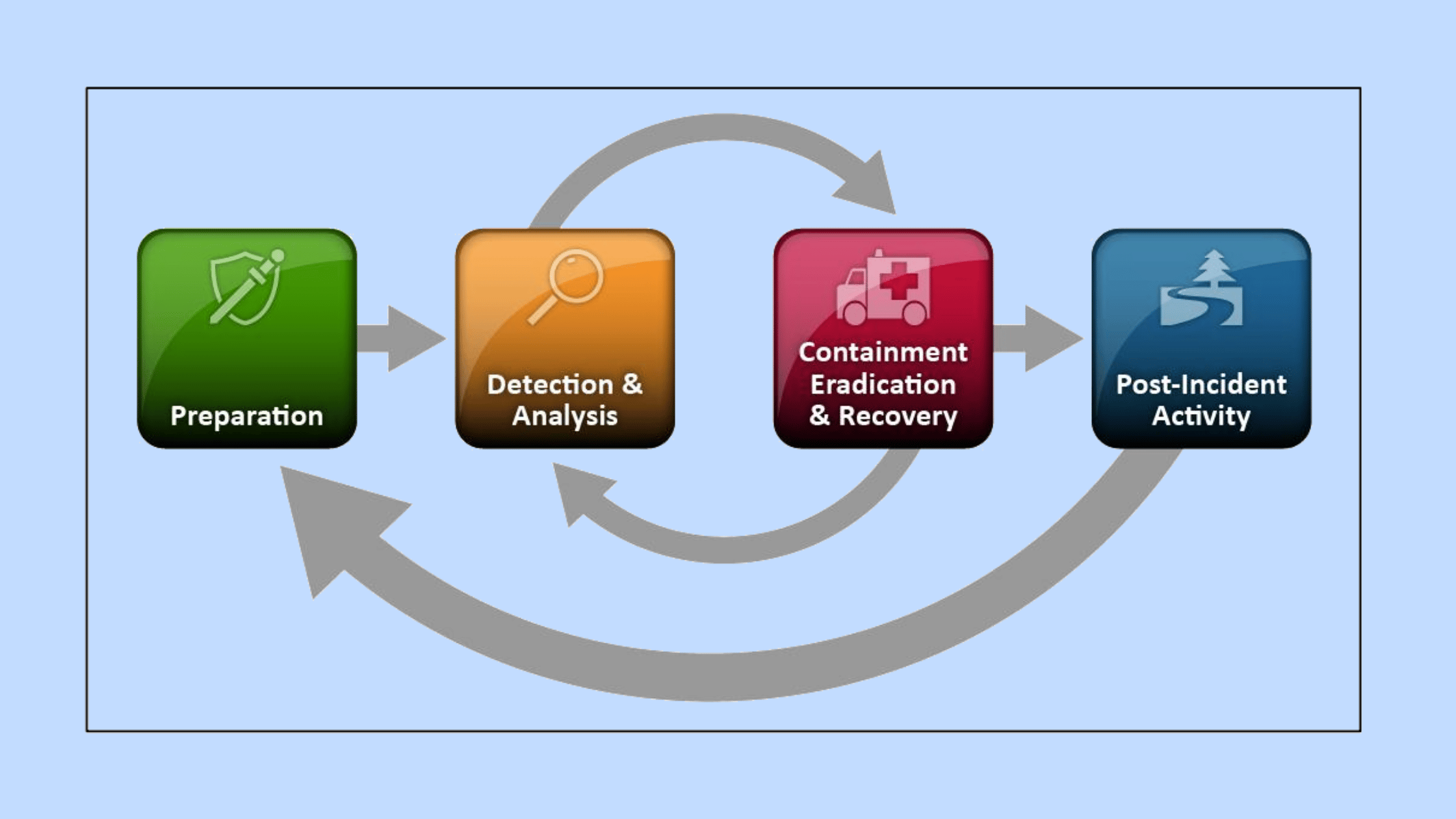
This article will explore the four main phases of the incident response life cycle, as outlined in the National Institute of Standards and Technology (NIST) Special Publication 800-61.
1. Preparation
The preparation phase is the foundation of an effective incident response strategy. During this phase, organizations establish and train their incident response team, acquire necessary tools and resources, and implement security controls to limit potential incidents.
Key Activities in the Preparation Phase:
Establishing an Incident Response Team: Form a dedicated team of professionals with diverse skills to handle various aspects of incident response.
Developing Policies and Procedures: Create comprehensive guidelines for incident handling, including roles and responsibilities, communication protocols, and escalation procedures.
Implementing Security Controls: Based on thorough risk assessments, deploy appropriate security measures to prevent and detect potential incidents.
Conducting Training and Awareness Programs: Regularly train staff on incident response procedures and raise awareness about potential security threats.
Acquiring Tools and Resources: Invest in necessary hardware, software, and other resources required for effective incident response.
Creating Communication Plans: Establish clear channels for internal and external communication during an incident.
List of Activities to be Performed in the Preparation Phase
|
Category
|
Task
|
Description Completed
|
|
Policy and Planning
|
Create incident response policy
|
Develop a formal policy that defines incident types and response procedures
|
|
Develop incident response plan
|
Create a detailed plan outlining roles, responsibilities, and procedures
|
|
|
Define incident categories and prioritization
|
Establish criteria for categorizing and prioritizing incidents
|
|
|
Team Formation
|
Establish incident response team structure
|
Define team model (centralized, distributed, or coordinating)
|
|
Identify team members
|
Select and assign roles to incident response team members
|
|
|
Define roles and responsibilities
|
Clearly outline duties for each team member and role
|
|
|
Training
|
Conduct general incident response training
|
Provide basic training to all team members on incident handling
|
|
Provide role-specific training
|
Offer specialized training based on team members' roles
|
|
|
Implement tabletop exercises
|
Conduct scenario-based exercises to test team readiness
|
|
|
Tools and Resources
|
Identify necessary hardware and software
|
Determine tools required for incident detection and analysis
|
|
Acquire incident handling tools
|
Procure and set up tools for incident response activities
|
|
|
Establish secure storage for evidence
|
Set up secure facilities for storing incident-related evidence
|
|
|
Communication
|
Create contact lists
|
Compile contact information for team members and relevant parties
|
|
Establish secure communication channels
|
Set up encrypted communication methods for incident response
|
|
|
Define reporting requirements
|
Establish protocols for internal and external incident reporting
|
|
|
Documentation
|
Create incident handling forms
|
Develop standardized forms for documenting incident details
|
|
Establish a knowledge base
|
Create a repository of information on threats and incident handling procedures
|
|
|
Infrastructure
|
Implement security controls
|
Deploy preventive measures based on risk assessments
|
|
Set up logging and monitoring
|
Establish systems for continuous monitoring and log analysis
|
|
|
Create network diagrams
|
Develop and maintain up-to-date network architecture diagrams
|
|
|
Partnerships
|
Identify external resources
|
Establish relationships with law enforcement and other incident response teams
|
|
Create information sharing agreements
|
Develop protocols for sharing incident information with trusted partners
|
|
|
Legal Considerations
|
Consult with legal department
|
Review incident response procedures for legal compliance
|
|
Establish evidence handling procedures
|
Develop protocols for collecting and preserving forensic evidence
|
|
|
Metrics
|
Define incident response metrics
|
Establish key performance indicators for measuring incident response effectiveness
|
|
Review and Update
|
Schedule regular plan reviews
|
Set up periodic reviews and updates of the incident response plan
|
|
Conduct plan testing
|
Regularly test and validate the incident response plan
|
By investing time and resources in the preparation phase, organizations can significantly improve their ability to detect and respond to security incidents promptly. According to a study by IBM, organizations with incident response teams and plans in place can reduce the average cost of a data breach by up to $2 million.
2. Detection and Analysis
The detection and analysis phase is crucial for identifying and understanding the nature of security incidents. This phase involves continuous monitoring of systems and networks to detect any unusual activities or potential threats.
Key Activities in the Detection and Analysis Phase:
Monitoring Systems and Networks: Utilize various tools such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and log analyzers to monitor network traffic and system activities.
Identifying Indicators of Compromise (IoCs): Look for signs that may indicate a security breach, such as unusual login attempts, unexpected system changes, or abnormal network traffic patterns.
Analyzing Alerts and Logs: Investigate and correlate alerts from different security tools and analyze system logs to understand the scope and impact of potential incidents.
Prioritizing Incidents: Assess the severity and potential impact of detected incidents to prioritize response efforts.
Documenting Findings: Maintain detailed records of all detected anomalies, analysis results, and initial response actions.
List of Actions to be Taken in the Detection and Analysis Phase
|
Category
|
Action
|
Description
|
|
Initial Detection
|
Monitor security events
|
Continuously monitor security alerts from various sources (IDS/IPS, SIEM, etc.)
|
|
Review system logs
|
Regularly analyze logs for suspicious activities
|
|
|
Investigate user reports
|
Follow up on security concerns reported by users
|
|
|
Check network traffic patterns
|
Analyze network traffic for anomalies
|
|
|
Initial Analysis
|
Validate the incident
|
Confirm that the detected activity is indeed an incident
|
|
Document initial findings
|
Record all initial observations and actions taken
|
|
|
Preserve evidence
|
Ensure all potential evidence is properly preserved
|
|
|
Assign incident tracking number
|
Create a unique identifier for the incident
|
|
|
Incident Classification
|
Determine incident type
|
Categorize the incident (e.g. malware and unauthorized access)
|
|
Assess incident severity
|
Evaluate the impact and urgency of the incident
|
|
|
Estimate incident scope
|
Determine the extent of systems and data affected
|
|
|
Identify affected assets
|
List all compromised or potentially compromised assets
|
|
|
Threat Intelligence
|
Correlate with known threats
|
Compare incident indicators with threat intelligence feeds
|
|
Check for similar incidents
|
Look for patterns or connections to previous incidents
|
|
|
Research attack signatures
|
Investigate any identified attack patterns or techniques
|
|
|
Communication
|
Notify incident response team
|
Alert appropriate team members based on incident severity
|
|
Brief management
|
Provide initial incident details to relevant management
|
|
|
Inform affected parties
|
Notify system owners and users as appropriate
|
|
|
Escalate if necessary
|
Involve higher-level management or external parties if required
|
|
|
Further Analysis
|
Perform in-depth investigation
|
Conduct detailed analysis of all available data
|
|
Identify attack vector
|
Determine how the incident occurred or spread
|
|
|
Assess potential impact
|
Evaluate possible consequences of the incident
|
|
|
Look for additional indicators
|
Search for other signs of compromise across systems
|
|
|
Document findings
|
Record all analysis results and conclusions
|
|
|
Containment Preparation
|
Develop containment strategy
|
Plan immediate actions to limit incident spread
|
|
Identify required resources
|
Determine tools and personnel needed for containment
|
|
|
Prepare for business impact
|
Assess potential effects of containment actions on operations
|
|
|
Reporting
|
Create initial incident report
|
Compile all relevant information into a preliminary report
|
|
Update incident tracking system
|
Ensure all incident details are recorded in the tracking system
|
|
|
Prepare for external reporting
|
Gather information required for any mandatory external reporting
|
The detection and analysis phase requires a combination of automated tools and human expertise. According to the SANS Institute, organizations should aim to detect and begin analyzing potential incidents within 24 hours of their occurrence.
3. Containment, Eradication, and Recovery
This phase focuses on limiting the damage caused by the incident, removing the threat, and restoring affected systems to normal operation. It is crucial to act swiftly and decisively during this phase to prevent further spread of the incident.
Key Activities in the Containment, Eradication, and Recovery Phase:
Containment: Implement measures to isolate affected systems and prevent the incident from spreading. This may include disconnecting infected devices from the network, blocking malicious IP addresses, or revoking compromised credentials.
Evidence Collection: Gather and preserve forensic evidence for later analysis and potential legal proceedings. This step is critical and should be performed carefully to maintain the integrity of the evidence.
Eradication: Remove the root cause of the incident, such as malware, unauthorized access points, or exploited vulnerabilities. This may involve patching systems, updating software, or reconfiguring network devices.
Recovery: Restore affected systems to their normal operational state. This includes restoring data from backups, rebuilding systems from clean images, and verifying the integrity of restored data and systems.
Validation: Conduct thorough testing to ensure that all affected systems have been properly remediated and are functioning correctly.
List of Steps to be Performed in the Containment, Eradication, and Recovery Phase
|
Phase
|
Step
|
Description
|
|
Containment
|
Choose containment strategy
|
Select appropriate strategy based on incident type and potential damage
|
|
Isolate affected systems
|
Disconnect or isolate compromised systems from the network
|
|
|
Preserve evidence
|
Create forensic images or copies of affected systems
|
|
|
Implement firewall rules
|
Add or modify firewall rules to block malicious traffic
|
|
|
Disable compromised accounts
|
Suspend or disable accounts that may have been compromised
|
|
|
Change passwords
|
Reset passwords for affected systems and user accounts
|
|
|
Patch vulnerabilities
|
Apply emergency patches to address exploited vulnerabilities
|
|
|
Document containment actions
|
Record all containment measures taken
|
|
|
Eradication
|
Identify malware
|
Determine the specific malware or tools used in the attack
|
|
Remove malware
|
Use anti-malware tools to remove identified threats
|
|
|
Delete malicious files
|
Remove any malicious files or unauthorized software
|
|
|
Close attack vectors
|
Address and fix vulnerabilities that allowed the initial compromise
|
|
|
Update and patch systems
|
Apply all necessary updates and security patches
|
|
|
Improve defenses
|
Implement additional security controls to prevent similar incidents
|
|
|
Perform vulnerability scan
|
Scan systems to ensure all vulnerabilities have been addressed
|
|
|
Verify eradication
|
Confirm that all malicious components have been removed
|
|
|
Recovery
|
Restore from clean backups
|
Restore affected systems using verified clean backups
|
|
Rebuild systems if necessary
|
Rebuild systems from scratch if clean backups are unavailable
|
|
|
Replace compromised files
|
Replace any corrupted or compromised files with clean versions
|
|
|
Reset passwords
|
Change passwords for all affected user accounts and systems
|
|
|
Restore network connectivity
|
Reconnect cleaned systems to the network
|
|
|
Implement additional monitoring
|
Set up enhanced monitoring for recovered systems
|
|
|
Test system functionality
|
Verify that all restored systems and applications are functioning correctly
|
|
|
Gradually restore operations
|
Carefully restore business operations in a phased approach
|
|
|
Monitor for abnormal activity
|
Closely watch recovered systems for any signs of persisting issues
|
|
|
Conduct security review
|
Perform a thorough security review of recovered systems
|
|
|
Update documentation
|
Update system documentation to reflect changes made during recovery
|
|
|
Communicate recovery status
|
Inform all relevant parties about the recovery progress and completion
|
|
|
All Phases
|
Document all actions
|
Maintain detailed logs of all actions taken throughout the process
|
|
Update incident status
|
Regularly update the incident status in the tracking system
|
|
|
Communicate with stakeholders
|
Keep relevant stakeholders informed throughout the process
|
|
|
Assess effectiveness
|
Continually evaluate the effectiveness of containment, eradication, adnd recovery actions.
|
The time required for this phase can vary greatly depending on the complexity and severity of the incident. According to the Ponemon Institute, the average time to contain a data breach is 280 days. Organizations with well-prepared incident response plans can significantly reduce this timeframe.
4. Post-Incident Activity
The post-incident activity phase is often overlooked but is crucial for improving an organization's overall security posture and incident response capabilities. This phase involves reflecting on the incident, documenting lessons learned, and implementing improvements to prevent similar incidents in the future.
Key Activities in the Post-Incident Activity Phase:
Conducting a Post-Incident Review: Hold a meeting with all relevant stakeholders to discuss the incident, the response actions taken, and their effectiveness.
Documenting Lessons Learned: Identify areas for improvement in the incident response process, security controls, and overall organizational preparedness.
Updating Incident Response Plans: Revise and update incident response plans and procedures based on the lessons learned from the incident.
Implementing Security Improvements: Address any vulnerabilities or weaknesses identified during the incident and implement additional security measures as necessary.
Providing Training and Awareness: Conduct additional training for staff based on the insights gained from the incident.
Reporting: Prepare comprehensive reports on the incident for management, regulatory bodies, and other relevant parties.
List of Tasks to be Done in the Post-Incident Phase
|
Category
|
Task
|
Description
|
|
Lessons Learned
|
Schedule lessons learned meeting
|
Set up a meeting with all involved parties within 2 weeks of incident closure
|
|
Prepare meeting agenda
|
Create an agenda covering all aspects of the incident and response
|
|
|
Review incident timeline
|
Analyze the incident chronology and response actions
|
|
|
Evaluate response effectiveness
|
Assess the effectiveness of the incident handling process
|
|
|
Identify areas for improvement
|
Determine what actions, processes, or policies need enhancement
|
|
|
Document meeting outcomes
|
Record all findings, recommendations, and action items from the meeting
|
|
|
Evidence Retention
|
Review evidence collected
|
Catalogue all evidence gathered during the incident
|
|
Determine retention requirements
|
Identify legal and organizational requirements for evidence retention
|
|
|
Securely store evidence
|
Ensure all retained evidence is stored securely and properly
|
|
|
Create evidence disposition plan
|
Develop a plan for eventual secure disposal of evidence
|
|
|
Incident Documentation
|
Complete incident report
|
Finalize the comprehensive incident report with all details and outcomes
|
|
Update incident database
|
Ensure all incident information is properly recorded in the incident database
|
|
|
Review and approve documentation
|
Have relevant stakeholders review and approve all incident documentation
|
|
|
Follow-up Actions
|
Create action plan
|
Develop a plan to address identified improvements and recommendations
|
|
Assign responsibilities
|
Delegate tasks for implementing improvements to appropriate team members
|
|
|
Set deadlines
|
Establish timelines for completing follow-up actions
|
|
|
Track progress
|
Monitor and report on the progress of follow-up actions
|
|
|
Policy and Procedure Updates
|
Review current policies
|
Examine existing policies in light of incident findings
|
|
Identify policy gaps
|
Determine areas where policies need to be created or updated
|
|
|
Update procedures
|
Revise incident response procedures based on lessons learned
|
|
|
Obtain approvals
|
Get management approval for policy and procedure changes
|
|
|
Training and Awareness
|
Identify training needs
|
Determine areas where additional training is required
|
|
Update training materials
|
Revise training content to incorporate lessons from the incident
|
|
|
Schedule training sessions
|
Plan and conduct additional training for relevant staff
|
|
|
Develop awareness campaign
|
Create materials to increase general security awareness
|
|
|
Security Enhancements
|
Identify security gaps
|
Determine areas where security controls need improvement
|
|
Propose new controls
|
Recommend additional security measures based on incident analysis
|
|
|
Implement approved changes
|
Deploy new or enhanced security controls
|
|
|
Test new measures
|
Verify the effectiveness of newly implemented security measures
|
|
|
Metrics and Reporting
|
Calculate incident metrics
|
Compute relevant metrics (e.g. time to detect and time to resolve)
|
|
Analyze trend data
|
Examine incident data for trends or patterns
|
|
|
Prepare management report
|
Create a summary report of the incident and its implications for leadership
|
|
|
Report to external parties
|
Submit required reports to relevant external organizations (e.g. US-CERT)
|
|
|
Threat Intelligence
|
Update threat database
|
Add new threat information gathered from the incident to threat intelligence database
|
|
Share threat information
|
Disseminate relevant threat data to trusted partners or information sharing groups
|
|
|
Refine detection capabilities
|
Update detection tools and rules based on new threat information
|
|
|
Cost Analysis
|
Calculate incident costs
|
Determine the total cost of the incident (including response and recovery)
|
|
Assess business impact
|
Evaluate the overall impact of the incident on business operations
|
|
|
Prepare financial report
|
Create a detailed report of incident-related costs and impacts
|
|
|
Closure
|
Verify all tasks completed
|
Ensure all post-incident tasks have been addressed
|
|
Obtain final sign-offs
|
Get final approval from relevant stakeholders to close the incident
|
|
|
Archive incident data
|
Securely archive all incident-related information and documentation
|
The post-incident activity phase is critical for continuous improvement. According to a report by Gartner, organizations that conduct thorough post-incident reviews and implement lessons learned can reduce the impact of future incidents by up to 80%.
Conclusion
The incident response life cycle provides a structured approach to handling cybersecurity incidents effectively. By following these four phases - Preparation, Detection and Analysis, Containment, Eradication, and Recovery, and Post-Incident Activity - organizations can improve their ability to respond to and recover from security breaches.
It's important to note that the incident response life cycle is not a linear process but a continuous cycle of improvement. Each incident provides an opportunity to learn and enhance an organization's security posture and incident response capabilities.
As cyber threats continue to evolve, organizations must remain vigilant and adapt their incident response strategies accordingly. Regular testing, updating, and refining of incident response plans are essential to stay ahead of potential threats and minimize the impact of security incidents.
By investing in a robust incident response capability and following the life cycle approach, organizations can significantly reduce the financial and reputational damage caused by cybersecurity incidents, ultimately strengthening their overall security posture in an increasingly complex threat landscape.
We hope this post helped explore the life cycle of Incident Response. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.