Table of Contents
Learn the Difference Between Events and Incidents with Examples
In cybersecurity and security operations, two terms are quite popular- Event and Incident. Most of the beginners slip in to the confusion and fail to distinguish between them and often used interchangeably. At first glance, both refer to occurrences within a system, but their implications and the required responses differ significantly. Understanding the clear distinction between these terms is crucial for efficient management, prioritization, and resolution of security issues within an organization. Upon reading this article, you will be a position to confidently distinguish between an Event and an Incident.
What is an Event?
An event is an observable occurrence within a system or network. Events happen continuously in every IT environment and can range from routine, harmless actions to activities that may indicate a potential problem. It's important to note that not every event is a cause for concern.
Key Characteristics of an Event:
Events can be informational or adverse.
They are logged occurrences within a network or system.
They may or may not require immediate attention.
Examples of Events:
Login Attempts: Every time a user logs into a system, it is recorded as an event. For example, a successful login to a corporate email system is a normal event.
System Updates: The installation of a software patch or system upgrade is an event that needs to be logged for tracking and audit purposes.
File Access: Accessing files from a shared drive by employees is an event that helps keep a record of user activity.
Adverse Events
Within the broader category of events, we have a subset known as adverse events. An adverse event is defined as an event with negative consequences or potential negative impact on the system or organization.
Examples of Adverse Events:
A failed login attempt
A system crash or unexpected reboot
A sudden spike in CPU usage
An application throwing an error
Unexpected changes to critical system files
Adverse events warrant closer attention and may require further investigation to determine their cause and potential impact.
Informational Events vs. Adverse Events:
Informational Event: These events do not represent a threat or problem. For instance, when a user successfully logs into a system or an automated backup completes successfully, these are logged but don't indicate any issue.
Adverse Event: An adverse event indicates that something has gone wrong, but it may not necessarily require immediate action. For example, a failed login attempt could signal an issue or security concern if it repeats multiple times in a short period.
It's important to note that events are not inherently good or bad; they are merely occurrences that can be observed and recorded. The significance of an event depends on its context and potential impact on the system or organization.
What is an Incident?
While all incidents are adverse events, not all adverse events are incidents. An incident refers to a significant event that indicates a violation of a system’s security policy, acceptable use policy, or standard security practices.
Key Characteristics of an Incident:
An incident involves a violation or threat to the security posture of the system or network.
It usually requires immediate attention to mitigate or stop the breach or attack.
Incidents often lead to activation of a formal Incident Response Plan (IRP).
According to NIST Special Publication 800-61, an incident is defined as a "violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices." This definition emphasizes that an incident must have a direct impact on the security posture of an organization, leading to potential data breaches, service interruptions, or compromise of sensitive information.
Examples of Incidents:
Malware Attack: If malware is detected on a server, it is categorized as an incident because it violates security policies and poses an immediate risk to the system.
Phishing Attack: A user clicking on a malicious email link that results in a compromised system is considered an incident because it represents a security breach.
Denial of Service (DoS) Attack: An attacker flooding a network with traffic to disrupt services would be classified as an incident due to the service disruption and violation of security controls.
Unauthorized Data Access: If an employee downloads sensitive corporate data and uploads it to an unauthorized site like WikiLeaks, it constitutes a severe incident due to the potential exposure of confidential information.
In contrast to events, incidents usually trigger predefined procedures, requiring involvement from specialized teams, such as a Cybersecurity Incident Response Team (CIRT), to mitigate the risk and minimize damage.
Differences Between Events and Incidents
The distinction between events and incidents lies in their nature, scope, and the response they invoke. While an event can be benign or informational, an incident always involves a violation or imminent threat to security.
|
Characteristic
|
Event
|
Incident
|
|---|---|---|
|
Definition
|
An observable occurrence in a system or network.
|
A violation or imminent threat of a violation of security policies.
|
|
Severity
|
Can be informational or adverse.
|
Always adverse with significant risk or impact.
|
|
Impact
|
Events may or may not have an impact on the system or organization.
|
Incidents, by definition, have a negative impact or pose an imminent threat.
|
|
Response Required
|
Usually no immediate action required.
|
Requires immediate action and formal incident response.
|
|
Example
|
Successful login, failed login, software update.
|
Malware infection, DoS attack, data breach.
|
Event vs. Incident – Practical Example
Consider the following scenario:
Event: A user attempts to log in to their workstation. This is logged as a normal event. However, after multiple failed login attempts (adverse event), an alert might be triggered.
Incident: If these failed login attempts are part of a brute-force attack aimed at gaining unauthorized access to the system, it is escalated into an incident, requiring immediate action to block the attack and protect the system.
Incident Response Planning and Severity Levels
Organizations often categorize events and incidents by severity levels to determine the appropriate response. Severity levels range from minor incidents, such as the detection of blocked malware, to severe incidents like a full-scale data breach or ransomware attack. In minor incidents, the IT team can often handle the issue internally without escalating to a full incident response plan. However, major incidents often activate the Cyber Incident Response Team (CIRT), requiring a more coordinated and structured approach to containment and resolution.
Real-World Examples: Distinguishing Events from Incidents
To further clarify the difference between events and incidents, let's examine some practical scenarios and determine whether they qualify as events or incidents.
Scenario 1: Successful Login
A user successfully logs into their workstation at the beginning of the workday.
Classification: Event Explanation: This is a routine, expected occurrence that doesn't violate any security policies. It's an observable event that should be logged but doesn't require any specific response.
Scenario 2: Failed Login Attempts
Multiple failed login attempts are recorded for a user account over a short period.
Classification: Event (potentially escalating to an Incident) Explanation: Initially, this would be classified as an adverse event. However, if the number of failed attempts exceeds a predefined threshold or exhibits a pattern indicative of a brute-force attack, it could escalate to an incident requiring investigation and response.
Scenario 3: Malware Detection
The antivirus software detects and successfully blocks a piece of malware from executing on a user's computer.
Classification: Incident (minor) Explanation: Even though the malware was blocked, this situation represents a violation of security practices and policies. It's considered an incident, albeit a minor one that may not require full incident response team activation.
Scenario 4: Unexpected System Reboot
A critical server unexpectedly reboots during business hours.
Classification: Adverse Event (potentially escalating to an Incident) Explanation: Initially, this would be classified as an adverse event. It requires investigation to determine the cause. If the reboot was due to a security issue (e.g., exploitation of a vulnerability), it would be escalated to an incident.
Scenario 5: Data Exfiltration
A security information and event management (SIEM) system detects unusual outbound traffic, indicating potential data exfiltration.
Classification: Incident Explanation: This scenario clearly indicates a potential security breach and violation of data protection policies. It requires immediate investigation and response, qualifying it as an incident.
See this below table with more such examples.
|
Scenario
|
Classification
|
Response
|
|
1. Successful Login
|
Event
|
No specific response required; routine logging
|
|
2. Failed Login Attempts
|
Event (potentially escalating to Incident)
|
Monitor closely; if threshold exceeded, investigate for potential brute-force attack
|
|
3. Malware Detection
|
Incident (minor)
|
Review antivirus logs; check for similar occurrences on other systems; update threat signatures if necessary
|
|
4. Unexpected System Reboot
|
Adverse Event (potentially escalating to Incident)
|
Investigate cause; check system logs; if security-related, escalate to incident and follow incident response procedures
|
|
5. Data Exfiltration
|
Incident
|
Immediate investigation; activate incident response team; isolate affected systems; analyze traffic patterns; initiate containment and eradication procedures
|
|
6. Software Update
|
Event
|
No specific response required; routine logging
|
|
7. Phishing Email Received
|
Event
|
Log the occurrence; consider updating email filters; remind users about phishing awareness
|
|
8. Phishing Link Clicked
|
Incident
|
Isolate affected system; scan for malware; reset user credentials; investigate potential data compromise
|
|
9. Unusual Admin Account Activity
|
Adverse Event (potentially escalating to Incident)
|
Investigate the activity; verify with the account owner; if unauthorized, treat as an incident
|
|
10. DDoS Attack
|
Incident
|
Activate incident response team; implement DDoS mitigation measures; analyze traffic patterns; coordinate with ISP if necessary
|
|
11. Firewall Configuration Change
|
Event
|
Log the change; ensure change management procedures were followed
|
|
12. Unauthorized Firewall Change
|
Incident
|
Investigate the change; revert to known-good configuration; analyze logs to determine how the change was made
|
|
13. New Device on Network
|
Event
|
Log the occurrence; verify if it's an authorized device
|
|
14. Ransomware Infection
|
Incident
|
Immediately isolate affected systems; activate incident response team; assess scope of infection; initiate recovery procedures
|
|
15. Power Outage
|
Adverse Event
|
Verify all systems restart properly; investigate cause if repeated occurrences
|
The Importance of Proper Classification
Correctly distinguishing between events and incidents is crucial for several reasons:
Resource Allocation: Proper classification ensures that incident response resources are deployed effectively, focusing on genuine security threats rather than routine events.
Response Time: Identifying true incidents quickly allows for faster response times, potentially minimizing damage and reducing recovery time.
Compliance: Many regulatory frameworks require reporting of security incidents within specific timeframes. Proper classification helps ensure compliance with these requirements.
Continuous Improvement: Analyzing the relationship between events and incidents can help improve detection mechanisms and refine incident response procedures over time.
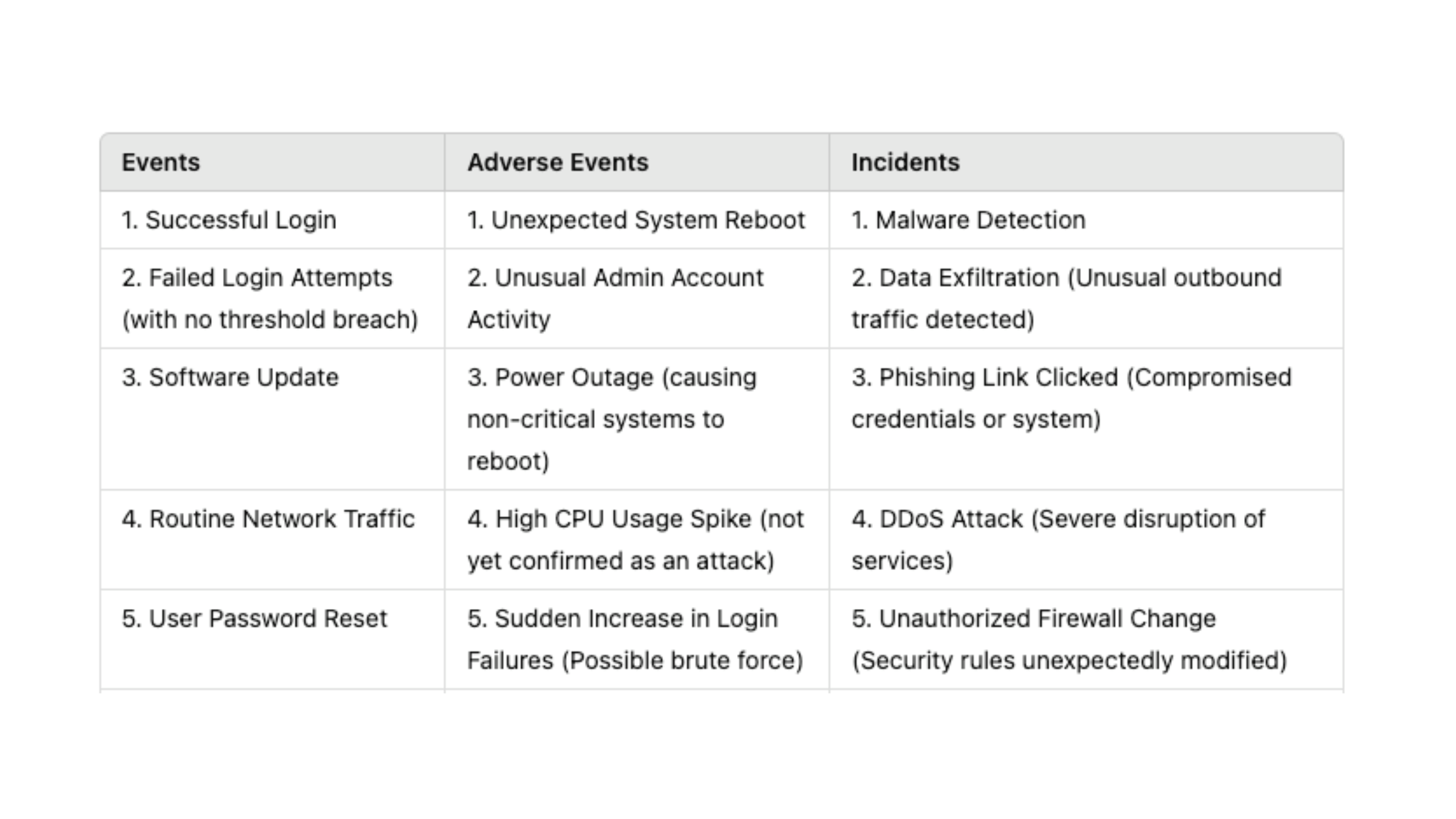
|
Events
|
Adverse Events
|
Incidents
|
|
1. Successful Login
|
1. Unexpected System Reboot
|
1. Malware Detection
|
|
2. Failed Login Attempts (with no threshold breach)
|
2. Unusual Admin Account Activity
|
2. Data Exfiltration (Unusual outbound traffic detected)
|
|
3. Software Update
|
3. Power Outage (causing non-critical systems to reboot)
|
3. Phishing Link Clicked (Compromised credentials or system)
|
|
4. Routine Network Traffic
|
4. High CPU Usage Spike (not yet confirmed as an attack)
|
4. DDoS Attack (Severe disruption of services)
|
|
5. User Password Reset
|
5. Sudden Increase in Login Failures (Possible brute force)
|
5. Unauthorized Firewall Change (Security rules unexpectedly modified)
|
|
6. Email Received (Informational or Routine Email)
|
6. Multiple System Crashes Without Cause
|
6. Ransomware Infection (Files encrypted, ransom note displayed)
|
|
7. New Device on Network (Authorized)
|
7. Slow Network Performance (Potential DoS attack)
|
7. Insider Threat (Unauthorized user downloading sensitive files to an external device or site)
|
|
8. Routine File Access by User
|
8. Misconfigured Software (Causing operational issues)
|
8. Command and Control Node Detected (System beaconing out to malicious actors)
|
|
9. Standard Firewall Rule Update
|
9. Network Device Malfunction (Causing possible downtime)
|
9. Unauthorized Access to Critical System (Admin account compromise)
|
Managing Events and Incidents
Logging and Monitoring Events
A fundamental aspect of managing events is having robust logging and monitoring tools in place. Organizations must track every occurrence within the network to identify patterns that could signal adverse events or potential incidents. Event logging tools, like SIEM (Security Information and Event Management) systems, provide real-time insights into system behavior and help in early detection of issues before they escalate into incidents.
Incident Response Plans (IRP)
When an event is determined to be an incident, an Incident Response Plan (IRP) comes into play. This plan outlines the steps required to contain, mitigate, and recover from the incident. The IRP often includes:
Identification: Detecting the incident through monitoring tools.
Containment: Isolating the affected systems to prevent further damage.
Eradication: Removing the threat from the system.
Recovery: Restoring normal operations and verifying that systems are secure.
Lessons Learned: Analyzing the incident to improve future response efforts.
Conclusion
Understanding the difference between events and incidents is fundamental to effective cybersecurity and incident response planning. While events are simply observable occurrences within a system or network, incidents specifically involve violations or threats to security policies and practices.
By correctly classifying and responding to events and incidents, organizations can improve their overall security posture, allocate resources more effectively, and minimize the impact of genuine security threats. Remember, the key lies in developing clear policies, implementing robust monitoring systems, and continually refining your incident response processes based on real-world experiences.
As you develop or refine your incident response plan, consider using tools like MITRE ATT&CK to map out potential incidents and improve your detection and response capabilities. Additionally, frameworks like the NIST Cybersecurity Framework can provide valuable guidance in developing comprehensive incident response strategies.
By mastering the distinction between events and incidents and implementing effective classification and response procedures, you'll be well-equipped to handle the ever-evolving landscape of cybersecurity threats.
We hope this article let you know about the difference between events and incidents with examples. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.