Table of Contents
What is Cyber Incident Response Plan? What Should a CIRP Have?
Cyberattacks pose an ever-present threat to organizations, but having a cyber incident response plan (CIRP) can provide an actionable defense. A CIRP outlines an organization’s strategy and framework to prepare for, detect, respond to, and recover from cybersecurity incidents.
An effective CIRP defines roles and responsibilities for incident response teams, including leadership oversight for strategic decisions. It also covers internal and external communications plans vital to coordinating an efficient response. Detailed incident response procedures supplement the high-level CIRP to give technology teams specific direction across identified threats and common attack scenarios.
This blog post covers:
The purpose and objectives of having a response plan
What should be included in a cyber incident response plan
Why all organizations need to have an incident response plan
An overview of the incident response process
With increasing cyberattack frequency and impact, having and testing an updated CIRP helps organizations minimize disruption by enabling rapid, coordinated action. All organizations need readiness plans for cyber crises tailored to their unique systems, services, and obligations. When cyber incidents inevitably occur, following CIRP guidance can drive effective decision-making amid chaos to accelerate the return of normal operations.
Purpose and Objectives of a Cyber Incident Response Plan
The overarching purpose of developing a cyber incident response plan (CIRP) is to institute preparedness that enables rapid detection of and coordinated response to cyberattacks. This accelerates recovery efforts to restore normal business operations.
Every organization needs a plan ready to activate when a cybersecurity incident occurs. Without established protocols and procedures guiding response, organizations can experience paralysis in decision-making or ineffective, disjointed efforts that prolong resolution.
Specific objectives for organizations to meet through cyber incident response plans include:
Providing well-defined, step-by-step guidance that teams can immediately execute when discovering a cyberattack
Clarifying roles and responsibilities for personnel across technical and leadership positions engaged in incident response
Detailing communication workflows for internal stakeholders and external entities based on incident type and severity
Identifying legal compliance requirements for external breach notification and reporting obligations
Promoting continuous review and enhancement of incident response capabilities by evaluating execution during cyber crises
What Should a Cyber Incident Response Plan Have?
An effective CIRP has several key components:
Authority and review process: Details the document owner, reviewers, approval authority, and review frequency to keep it updated.
Purpose and objectives: Outlines the goals of the CIRP, like swift response aligned to security and business needs.
Standards and frameworks: Lists relevant cybersecurity standards and frameworks that inform the plan.
Incident response process overview: Summarizes the high-level steps in responding to a cyber incident.
Common cyber threats and incidents: Describes typical threats like phishing and expected incident responses.
Roles and responsibilities: Defines key teams like the Cyber Incident Response Team (CIRT) and executives overseeing strategic response.
Communications plan: Covers internal, public relations, and media communications strategies.
Supporting procedures and playbooks: Lists standard operating procedures and incident response playbooks that complement the CIRP.
External reporting obligations: Includes requirements to report incidents to sector organizations, law enforcement, regulators, and insurers.
The CIRP also outlines the step-by-step cybersecurity incident response process, covering detection, analysis, containment, recovery, and review.
The Need for All Organizations to Have a Cyber Incident Response Plan
The increasing magnitude and impact of cyberattacks have made having a cyber incident response plan an essential component of any organization’s security program. Regardless of an organization’s size, industry, or IT budget, cyberattacks pose a real threat, making incident response preparedness mandatory.
With nearly two-thirds of data breaches caused by phishing and hacking in 2021, cyber risk is ubiquitous across sectors. Government agencies, small businesses, healthcare providers, schools, and non-profits have all fallen victim just in the last year, suffering business disruption, data loss, regulatory non-compliance penalties, and financial damages. As cybercrime tools and services become more sophisticated and inexpensive on dark web markets, all organizations are vulnerable targets.
However, many wrongly assume that fully outsourcing IT services and security needs negates the necessity of an internal cyber incident response plan. But even organizations relying completely on managed service providers (MSPs) for systems management require their own CIRP tailored to their operating environment. Without documented protocols customized to internal resources, policies, regulations, supply chain relationships, and communications needs, organizations invite disarray.
Creating a CIRP enables an organization to assess its unique cyber risk exposures given systems and data assets. This further allows the evaluation of detection and mitigation controls in place. With a plan guiding decisions during high-severity incidents, organizations can respond quickly and appropriately.
An organization’s leaders also benefit greatly from understanding incident response roles and obligations. Confusion over legal or compliance reporting responsibilities, media engagement protocols, and customer notifications often compounds disruption during cyber events. A CIRP gives executives clarity on stakeholder communications needs, empowering leaders to confidently make difficult strategic calls.
Finally, continually reviewing and updating cyber response plans allows enhancing responsiveness over time. Running tabletop simulations of potential breach scenarios assesses readiness across technical, communications, and senior leadership dimensions. Identifying plan gaps informs areas needing investment and process refinements to harden defenses. This mitigatesOperational disruption when real attacks later strike.
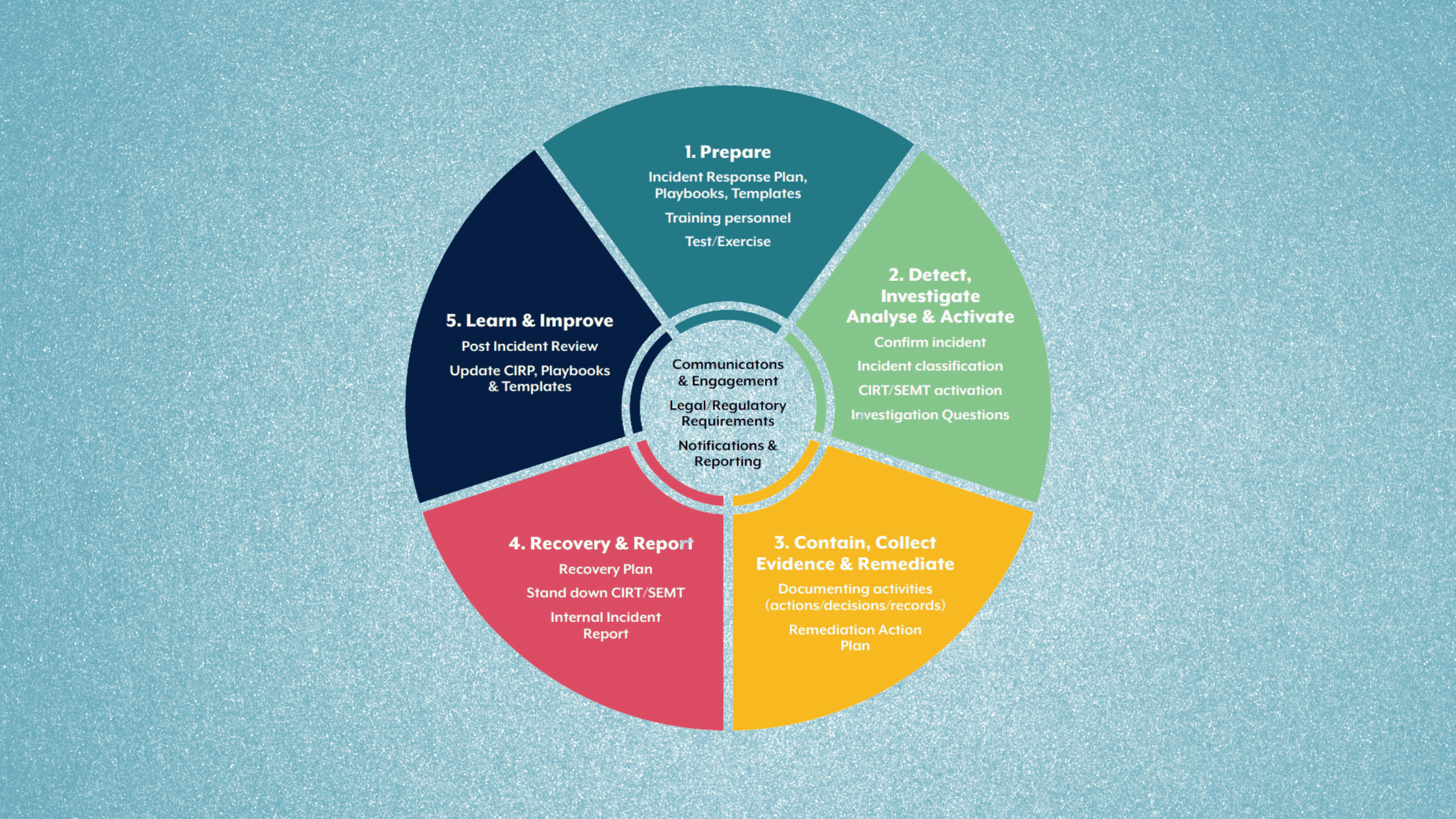
An Overview of the Incident Response Process
Image Source: https://www.cyber.gov.au/sites/default/files/2023-03/ACSC%20Cyber%20Incident%20Response%20Plan%20Guidance_A4.pdf
The first step entails detecting anomalous activity through an organization’s security tools, third-party notifications, or user reports. Triaging and investigating any event determines if it meets the threshold to classify as an incident based on potential impact.
If the event constitutes an incident, response teams activate according to predefined severity escalation triggers. The Cyber Incident Response Team (CIRT) is formed to manage operational aspects of analysis and resolution. The Senior Executive Management Team (SEMT) provides strategic guidance aligned to business objectives.
After notifying insurers and appropriate regulatory authorities per compliance requirements, the investigation into root causes begins by gathering event forensic data. Understanding the attack vector and compromised systems guides appropriate containment responses to isolate threats and prevent incident expansion.
Responders must balance business continuity needs regarding affected systems when evaluating temporary shutdowns or quarantines. They execute the optimal solutions after exploring technical and operational tradeoffs of isolation options.
With threats cordoned off, attention shifts to eradicating footholds like malware installation points and purging attacker lateral movement pathways within systems. This Freedom of Maneuver Process concentrates on meticulously removing advanced persistent threat (APT) presence.
Finally, the organization shifts into recovery by restoring business capability across impacted infrastructure and services. This requires verifying system integrity to confirm threat elimination and prevent adversary persistence. With a return to operations, formal incident documentation concludes the overall process.
Applying this rigorous response framework outlined in the CIRP guidelines enables organizations to coordinate resources for efficient cyberattack disruption. Prior planning and testing proves essential though for successful incident navigation.
The Key Role of Cyber Incident Response Plans in Cybersecurity Preparedness
As cyber threats continue to increase in frequency, scale, and sophistication, having a tested cyber incident response plan forms a critical component of defense for organizations. Without the protocols and procedures codified in a CIRP to guide the swift discovery and coordinated response, organizations inevitably struggle to contain the fallout from successful attacks.
Establishing incident classification frameworks, detailing containment strategies, formalizing communications workflows, outlining regulatory reporting obligations, and documenting evidentiary standards are just a few areas where upfront CIRP development pays dividends during turbulent incidents involving stressed responders.
Equally importantly, conducting cyber crisis simulation exercises that pressure test CIRP effectiveness can reveal plan gaps and opportunities for hardening defenses even further. While cyber incident occurrence represents an inevitability, long-lasting business disruption does not have to be if organization preparation matches adversary persistence.
With risks exponentially increasing as more business functions digitally transform, every organization must prioritize tailored cyber incident response planning today to meet the threats already lying in wait for operational environments tomorrow.
We hope this post helped in learn what is cyber incident response plan? what should a CIRP have?. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.