Table of Contents
Exploring the Diverse Verticals of Cybersecurity- A Comprehensive Guide for Beginners
In my 15 years as a cybersecurity professional, I've often encountered enthusiastic individuals eager to embark on a career in this dynamic field. The conversation typically begins with a familiar question: "I want to start a career in cybersecurity. What should I do, and where should I start?"
If you're asking yourself these same questions, you're not alone. The world of cybersecurity is vast and constantly evolving, which can make it seem overwhelming for newcomers. But don't worry – I'm here to help guide you through this exciting landscape. My immediate response to aspiring cybersecurity professionals is always this:
Cybersecurity is a broad, collective term that encompasses several different verticals or subdomains. The key to finding your path is to first explore what cybersecurity is and understand its various components. As you delve into the fundamentals – learning about threats, risks, vulnerabilities, malware, and other core concepts – you'll naturally begin to discover areas that pique your interest.
This article aims to simplify your journey by providing a comprehensive overview of cybersecurity and its different verticals. We'll explore the various career roles within each area and discuss the certifications that can help you break into your chosen specialization. Whether you're a complete beginner or someone looking to switch careers, this guide will give you a solid foundation to start your cybersecurity journey.
So, let's dive in and unravel the multifaceted world of cybersecurity, helping you find your niche in this crucial and rewarding field.
What is Cybersecurity?
As I've interacted with students and newcomers to the field, I've noticed a common misconception: many believe that cybersecurity is primarily about hacking. There's often an assumption that cybersecurity professionals spend most of their time working on hacking techniques. Let me clarify this misconception right away - hacking, even ethical hacking, is just one small part of the vast field of cybersecurity.
While it's true that understanding hacking techniques can be valuable in cybersecurity, it's crucial to recognize that cybersecurity is a much broader and more diverse field. Ethical hacking, or penetration testing, is indeed one aspect of cybersecurity, but it's far from the whole picture.
So, what exactly is cybersecurity?
Cybersecurity refers to the practice of protecting systems, networks, devices, and data from digital attacks, theft, damage, or unauthorized access. It encompasses a wide range of technologies, processes, and practices designed to secure information from various cyber threats. The core goal of cybersecurity is to ensure the confidentiality, integrity, and availability of information - a concept often referred to as the CIA triad.
Confidentiality: Ensuring that sensitive information is accessible only to authorized users.
Integrity: Guaranteeing that data remains accurate, complete, and unaltered from its original state.
Availability: Making sure that systems and data are accessible to authorized users when needed.
Cybersecurity professionals work to protect against a variety of threats, including:
Ransomware
Denial-of-Service (DoS) attacks
Data breaches
Insider threats
To combat these diverse threats, cybersecurity covers multiple layers of defense:
Endpoint Security: Securing individual devices like computers, smartphones, and tablets.
Network Security: Protecting the communication between devices.
Cloud Security: Safeguarding data and applications in cloud environments.
Application Security: Ensuring software applications are free from vulnerabilities.
Data Security: Protecting sensitive information through encryption and access controls.
Cybersecurity isn't just about technical solutions. It also involves developing policies and procedures, conducting risk assessments, creating incident response plans, and educating users about security best practices. It's a field that requires a mix of technical skills, analytical thinking, and often, good communication abilities.
As we delve deeper into the various verticals of cybersecurity, you'll see that while offensive security (which includes ethical hacking) is one important aspect, there are many other crucial areas where cybersecurity professionals make significant contributions to protecting our digital world.
Understanding this broad scope of cybersecurity is essential for anyone looking to enter the field. It opens up a wide range of career possibilities beyond just hacking or penetration testing. Whether you're interested in threat analysis, security architecture, compliance, or any other specialization, there's likely a cybersecurity role that aligns with your interests and skills.
The Two Main Sub-Domains of Cybersecurity
When we dive deeper into the world of cybersecurity, we can broadly categorize most roles and responsibilities into two main sub-domains: Offensive Security and Defensive Security. Understanding these two areas can help you better navigate your career options and choose a path that aligns with your interests and strengths.
1. Offensive Security
Offensive Security, often referred to as "Red Team" activities, focuses on proactively identifying and exploiting vulnerabilities in systems, networks, and applications. The goal is to think and act like a potential attacker to uncover weaknesses before malicious actors can exploit them.
Key aspects of Offensive Security include:
Penetration Testing: Also known as "ethical hacking," this involves simulating cyberattacks to test the effectiveness of an organization's security measures.
Vulnerability Assessment: Systematically reviewing systems and applications to identify potential security flaws.
Red Team Operations: Conducting comprehensive, multi-layered simulated attacks to test an organization's detection and response capabilities.
Social Engineering: Testing human vulnerabilities through techniques like phishing simulations.
Professionals in Offensive Security often have job titles such as Penetration Tester, Ethical Hacker, or Red Team Specialist. They need a deep understanding of systems, networks, and common vulnerabilities, as well as creative problem-solving skills.
[For more information on ethical hacking as a career, check out our article on what you can do as an ethical hacker.]
2. Defensive Security
Defensive Security, sometimes called "Blue Team" activities, is focused on protecting systems, networks, and data from cyber threats. This sub-domain is about building robust defenses, detecting threats, and responding to incidents.
Key aspects of Defensive Security include:
Security Architecture: Designing and implementing secure IT infrastructures.
Security Operations: Monitoring systems for threats and responding to security incidents.
Incident Response: Developing and executing plans to address security breaches.
Threat Intelligence: Gathering and analyzing information about current and potential threats.
Security Engineering: Implementing and maintaining security tools and technologies.
Compliance and Risk Management: Ensuring adherence to security standards and regulations.
Professionals in Defensive Security may have titles like Security Analyst, Incident Response Specialist, or Security Operations Center (SOC) Analyst. They need strong analytical skills, attention to detail, and the ability to stay calm under pressure.
It's worth noting that while we categorize these as separate sub-domains, there's often overlap between offensive and defensive security. Many cybersecurity professionals work across both areas throughout their careers, and skills from one area can be highly valuable in the other.
For example, understanding offensive techniques can help defensive teams better anticipate and prepare for potential attacks. Conversely, experience in defensive operations can give offensive security professionals insights into common security measures they may encounter during penetration tests.
As you explore career options in cybersecurity, you may find yourself drawn more to one area than the other. Some people enjoy the problem-solving and creative aspects of offensive security, while others prefer the protective and analytical nature of defensive security. Both are crucial in maintaining a strong cybersecurity posture, and both offer rewarding career paths.
In the following sections, we'll delve into more specific verticals within cybersecurity, many of which fall under these broader categories of offensive and defensive security. This will give you a more detailed view of the diverse opportunities available in the field of cybersecurity.
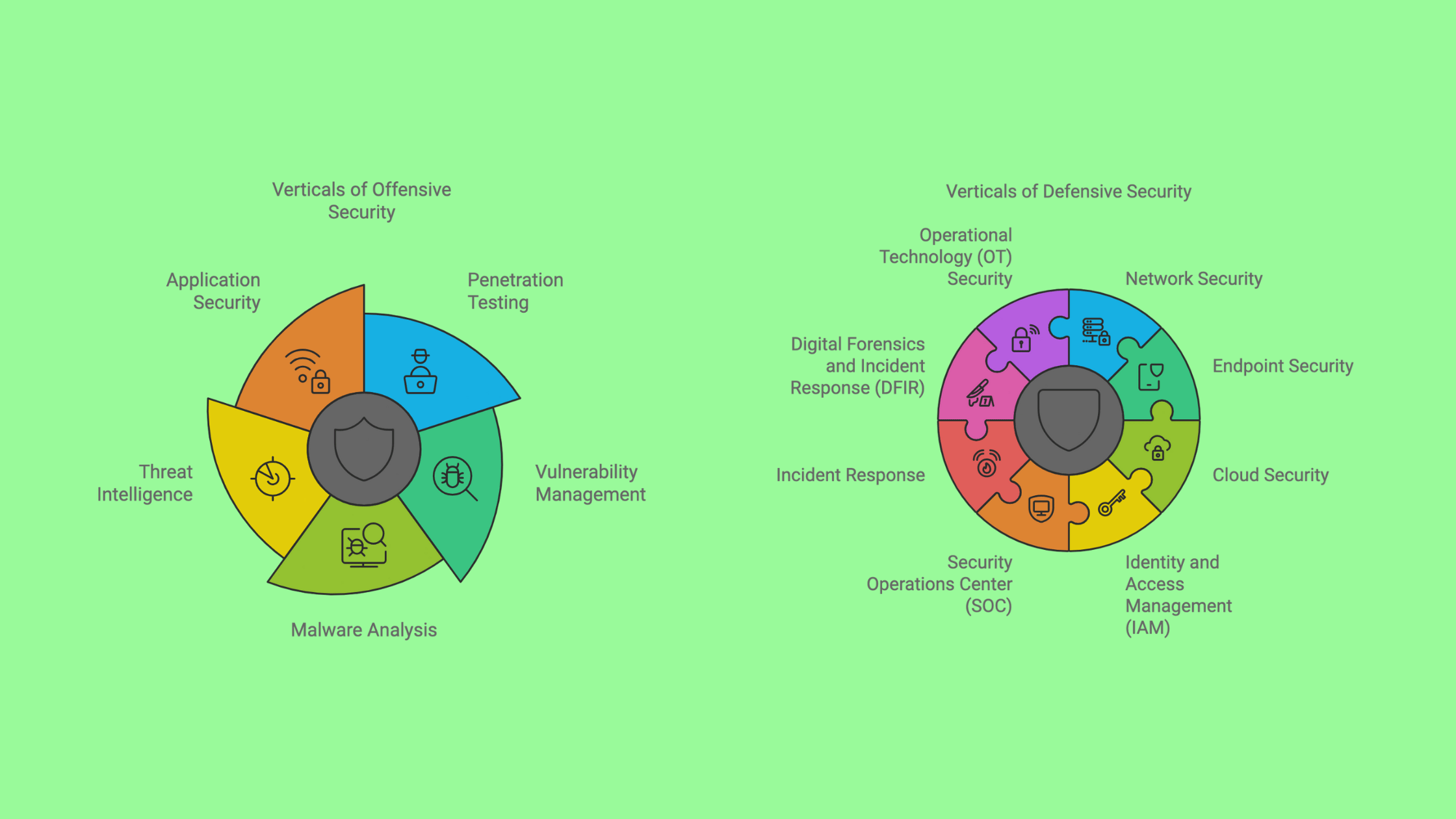
Common Verticals of Offensive Security
As I said in the previous section, offensive security focuses on proactively identifying and addressing vulnerabilities before malicious actors can exploit them. If you want to get into it, You should expolre more about these main verticals within offensive security:
1. Penetration Testing (Red Teaming)
Penetration Testing, often referred to as "pen testing" or "red teaming," involves simulating cyberattacks to test and identify vulnerabilities in organizational defenses. This practice helps organizations understand their security weaknesses from an attacker's perspective.
Expertise Required:
In-depth knowledge of various attack techniques and tools
Understanding of network protocols and system architectures
Strong problem-solving and analytical skills
Ability to think creatively and "outside the box"
Career Roles:
Penetration Tester
Red Team Operator
Ethical Hacker
Certifications:
Offensive Security Certified Professional (OSCP)
GIAC Penetration Tester (GPEN)
EC-Council Certified Ethical Hacker (CEH)
2. Vulnerability Management
Vulnerability Management focuses on identifying, classifying, and addressing security vulnerabilities in systems, networks, and applications. This vertical is crucial for maintaining a strong security posture.
Expertise Required:
Proficiency in vulnerability scanning tools and techniques
Understanding of risk assessment and prioritization
Knowledge of various types of vulnerabilities and their potential impacts
Familiarity with patch management processes
Career Roles:
Vulnerability Analyst
Security Assessor
Vulnerability Management Specialist
Certifications:
GIAC Vulnerability Assessor (GEVA)
Qualys Certified Specialist
CompTIA PenTest+
3. Malware Analysis and Reverse Engineering
This vertical involves understanding the behavior, structure, and purpose of malware to aid in detection and response. It's a critical component in developing effective defenses against evolving threats.
Expertise Required:
Strong programming skills, especially in low-level languages
Knowledge of assembly language and disassemblers
Understanding of operating system internals
Familiarity with various types of malware and their behaviors
Career Roles:
Malware Analyst
Reverse Engineer
Security Researcher
Certifications:
GIAC Reverse Engineering Malware (GREM)
EC-Council Certified Reverse Engineering Analyst (ECREA)
Certified Malware Analysis Professional (CMAP)
4. Threat Intelligence
Threat Intelligence involves gathering and analyzing data on emerging threats to help organizations defend against potential cyberattacks. While it has defensive aspects, it's also used to drive offensive strategies like preemptive strikes.
Expertise Required:
Strong analytical and research skills
Understanding of various threat actors and their tactics
Knowledge of global cybersecurity trends
Ability to synthesize information from multiple sources
Career Roles:
Threat Intelligence Analyst
Intelligence Operations Specialist
Certifications:
GIAC Cyber Threat Intelligence (GCTI)
EC-Council Certified Threat Intelligence Analyst (CTIA)
Certified Threat Intelligence Analyst (C|TIA)
5. Application Security
Application Security focuses on ensuring software applications are free from vulnerabilities. This often involves offensive tactics like penetration testing and code review to identify and address security flaws before they can be exploited.
Expertise Required:
Strong programming skills and understanding of software development lifecycles
Knowledge of common application vulnerabilities (e.g., OWASP Top 10)
Familiarity with secure coding practices
Experience with application security testing tools
Career Roles:
Application Security Engineer
Secure Code Auditor
Certifications:
GIAC Certified Web Application Defender (GWEB)
Certified Secure Software Lifecycle Professional (CSSLP)
Offensive Security Web Expert (OSWE)
|
Vertical
|
Description
|
Expertise Required
|
Career Roles
|
Certifications
|
|---|---|---|---|---|
|
1. Penetration Testing (Red Teaming)
|
Simulates cyberattacks to test and identify vulnerabilities in organizational defenses. Helps understand security weaknesses from an attacker's perspective.
|
• In-depth knowledge of attack techniques and tools
• Understanding of network protocols and system architectures
• Strong problem-solving and analytical skills
• Ability to think creatively
|
• Penetration Tester
• Red Team Operator
• Ethical Hacker
|
• Offensive Security Certified Professional (OSCP)
• GIAC Penetration Tester (GPEN)
• EC-Council Certified Ethical Hacker (CEH)
|
|
2. Vulnerability Management
|
Focuses on identifying, classifying, and addressing security vulnerabilities in systems, networks, and applications. Crucial for maintaining a strong security posture.
|
• Proficiency in vulnerability scanning tools and techniques
• Understanding of risk assessment and prioritization
• Knowledge of various types of vulnerabilities and their potential impacts
• Familiarity with patch management processes
|
• Vulnerability Analyst
• Security Assessor
• Vulnerability Management Specialist
|
• GIAC Vulnerability Assessor (GEVA)
• Qualys Certified Specialist
• CompTIA PenTest+
|
|
3. Malware Analysis and Reverse Engineering
|
Involves understanding the behavior, structure, and purpose of malware to aid in detection and response. Critical for developing effective defenses against evolving threats.
|
• Strong programming skills, especially in low-level languages
• Knowledge of assembly language and disassemblers
• Understanding of operating system internals
• Familiarity with various types of malware and their behaviors
|
• Malware Analyst
• Reverse Engineer
• Security Researcher
|
• GIAC Reverse Engineering Malware (GREM)
• EC-Council Certified Reverse Engineering Analyst (ECREA)
• Certified Malware Analysis Professional (CMAP)
|
|
4. Threat Intelligence
|
Involves gathering and analyzing data on emerging threats to help organizations defend against potential cyberattacks. Used to drive both defensive and offensive strategies.
|
• Strong analytical and research skills
• Understanding of various threat actors and their tactics
• Knowledge of global cybersecurity trends
• Ability to synthesize information from multiple sources
|
• Threat Intelligence Analyst
• Cyber Threat Hunter
• Intelligence Operations Specialist
|
• GIAC Cyber Threat Intelligence (GCTI)
• EC-Council Certified Threat Intelligence Analyst (CTIA)
• Certified Threat Intelligence Analyst (C|TIA)
|
|
5. Application Security
|
Focuses on ensuring software applications are free from vulnerabilities. Involves offensive tactics like penetration testing and code review to identify and address security flaws.
|
• Strong programming skills and understanding of software development lifecycles
• Knowledge of common application vulnerabilities (e.g., OWASP Top 10)
• Familiarity with secure coding practices
• Experience with application security testing tools
|
• Application Security Engineer
• Secure Code Auditor
• AppSec Penetration Tester
|
• GIAC Certified Web Application Defender (GWEB)
• Certified Secure Software Lifecycle Professional (CSSLP)
• Offensive Security Web Expert (OSWE)
|
Verticals of Defensive Security
As I said in the previous section, defensive security focus more on protecting organizations from cyber threats. Here are the main verticals within this domain:
1. Network Security
Network Security focuses on protecting the integrity, confidentiality, and availability of networks, including securing firewalls, routers, and intrusion detection systems.
Expertise Required:
In-depth understanding of network protocols and architectures
Knowledge of firewall configurations and network segmentation
Familiarity with intrusion detection/prevention systems (IDS/IPS)
Experience with VPNs and secure remote access solutions
Career Roles:
Network Security Engineer
Firewall Administrator
Certifications:
Cisco Certified Network Professional Security (CCNP Security)
CompTIA Security+
2. Endpoint Security
Endpoint Security involves protecting end-user devices such as desktops, laptops, and mobile devices from malware, phishing, and other attacks.
Expertise Required:
Knowledge of various endpoint protection solutions
Understanding of malware behavior and detection techniques
Familiarity with mobile device management (MDM) solutions
Experience with endpoint detection and response (EDR) tools
Career Roles:
Endpoint Security Specialist
Information Security Analyst
Certifications:
CompTIA Security+
GIAC Certified Endpoint Defender (GCED)
Certified Information Security Manager (CISM)
3. Cloud Security
Cloud Security focuses on safeguarding data, applications, and services hosted in cloud environments.
Expertise Required:
Understanding of cloud service models (IaaS, PaaS, SaaS)
Knowledge of cloud-specific security controls and best practices
Familiarity with major cloud platforms (AWS, Azure, Google Cloud)
Experience with cloud security posture management (CSPM) tools
Career Roles:
Cloud Security Architect
Cloud Security Engineer
Cloud Compliance Specialist
Certifications:
(ISC)² Certified Cloud Security Professional (CCSP)
AWS Certified Security - Specialty
4. Identity and Access Management (IAM)
IAM involves controlling access to systems and data by managing user identities, roles, and permissions.
Expertise Required:
Understanding of authentication and authorization protocols
Knowledge of single sign-on (SSO) and multi-factor authentication (MFA)
Familiarity with directory services (e.g., Active Directory)
Experience with IAM tools and frameworks
Career Roles:
IAM Specialist
Access Management Engineer
Identity Security Architect
Certifications:
GIAC Identity & Access Management Essentials (GIME)
Certified Identity and Access Manager (CIAM)
IDPro Certified Identity Professional (CIDPRO)
5. Security Operations Center (SOC)
SOC focuses on monitoring, detecting, and responding to security incidents in real-time using tools like SIEM systems.
Expertise Required:
Proficiency in SIEM tools and log analysis
Understanding of various attack vectors and indicators of compromise
Knowledge of incident response procedures
Familiarity with threat intelligence feeds
Career Roles:
SOC Analyst
Security Operations Manager
Threat Hunter
Certifications:
GIAC Certified Detection Analyst (GCDA)
EC-Council Certified SOC Analyst (CSA)
CompTIA Cybersecurity Analyst (CySA+)
6. Incident Response
Incident Response involves preparing for and responding to cybersecurity incidents such as breaches or malware outbreaks.
Expertise Required:
Knowledge of incident response frameworks and procedures
Understanding of digital forensics techniques
Familiarity with various types of cyber attacks and their indicators
Strong problem-solving and communication skills
Career Roles:
Incident Response Specialist
Cyber Incident Manager
Security Incident Handler
Certifications:
GIAC Certified Incident Handler (GCIH)
EC-Council Certified Incident Handler (ECIH)
7. Digital Forensics and Incident Response (DFIR)
DFIR focuses on investigating cyber incidents by collecting and analyzing digital evidence.
Expertise Required:
Proficiency in forensic tools and techniques
Understanding of various operating systems and file systems
Knowledge of legal and regulatory requirements for digital evidence
Experience with malware analysis and reverse engineering
Career Roles:
Digital Forensics Investigator
DFIR Consultant
Forensic Analyst
Certifications:
GIAC Certified Forensic Examiner (GCFE)
EnCase Certified Examiner (EnCE)
Certified Computer Forensics Examiner (CCFE)
[For more information on digital forensics, check out our introduction to digital forensics and its importance in cybersecurity.]
8. Operational Technology (OT) Security
OT Security involves securing critical infrastructure and industrial control systems (ICS) used in sectors like manufacturing and energy.
Expertise Required:
Understanding of industrial control systems and SCADA
Knowledge of OT-specific protocols and vulnerabilities
Familiarity with ICS security frameworks and standards
Experience with OT/IT convergence security challenges
Career Roles:
OT Security Specialist
ICS Security Engineer
SCADA Security Analyst
Certifications:
Global Industrial Cyber Security Professional (GICSP)
Certified SCADA Security Architect (CSSA)
ISA/IEC 62443 Cybersecurity Certificate Program
9. DevSecOps
DevSecOps integrates security practices into the software development lifecycle (SDLC) to ensure security across development, deployment, and operations.
Expertise Required:
Understanding of software development processes and tools
Knowledge of secure coding practices and application security testing
Familiarity with CI/CD pipelines and automation tools
Experience with containerization and orchestration technologies
Career Roles:
DevSecOps Engineer
Application Security Engineer
Secure Software Developer
Certifications:
Certified DevSecOps Professional (CDP)
AWS Certified DevOps Engineer - Professional
Docker Certified Associate
10. Governance, Risk, and Compliance (GRC)
GRC ensures organizations meet regulatory obligations while managing security risks.
Expertise Required:
Understanding of various compliance frameworks (e.g., ISO 27001, NIST, HIPAA)
Knowledge of risk assessment and management methodologies
Familiarity with security policies and procedures development
Experience with GRC tools and platforms
Career Roles:
Information Security Officer
Compliance Manager
IT Risk Analyst
Certifications:
Certified in Risk and Information Systems Control (CRISC)
Certified Information Systems Auditor (CISA)
GIAC Governance, Risk, and Compliance Analyst (GRCA)
11. Privacy and Data Protection
This vertical focuses on ensuring compliance with privacy laws like GDPR or CCPA and protecting personally identifiable information (PII) through security controls.
Expertise Required:
In-depth knowledge of privacy laws and regulations
Understanding of data protection techniques (e.g., encryption, anonymization)
Familiarity with privacy impact assessments and data mapping
Experience with privacy program management
Career Roles:
Data Protection Officer
Privacy Program Manager
Information Privacy Professional
Certifications:
Certified Information Privacy Professional (CIPP)
Certified Information Privacy Manager (CIPM)
GIAC Privacy and Data Protection (GPDP)
|
Specialization
|
Description
|
Expertise Required
|
Career Roles
|
Certifications
|
|---|---|---|---|---|
|
Network Security
|
Protecting integrity, confidentiality, and availability of networks
|
- Network protocols and architectures
- Firewall configurations
- Intrusion detection/prevention systems
- VPNs and secure remote access
|
- Network Security Engineer
- Firewall Administrator - Security Architect
|
- CCNP Security
- CompTIA Security+
- CISSP
|
|
Endpoint Security
|
Protecting end-user devices from malware, phishing, and other attacks
|
- Endpoint protection solutions
- Malware behavior and detection
- Mobile device management (MDM)
- Endpoint detection and response (EDR)
|
- Endpoint Security Specialist
- Information Security Analyst
- Security Operations Analyst
|
- CompTIA Security+
- GIAC Certified Endpoint Defender (GCED)
- CISM
|
|
Cloud Security
|
Safeguarding data, applications, and services in cloud environments
|
- Cloud service models - Cloud-specific security controls
- Major cloud platforms - Cloud security posture management (CSPM)
|
- Cloud Security Architect
- Cloud Security Engineer
- Cloud Compliance Specialist
|
- CCSP
- AWS Certified Security Specialty
- Azure Security Engineer Associate
|
|
Identity and Access Management (IAM)
|
Controlling access to systems and data
|
- Authentication and authorization protocols - SSO and MFA
- Directory services
- IAM tools and frameworks
|
- IAM Specialist - Access Management Engineer
- Identity Security Architect
|
- GIAC Identity & Access Management Essentials (GIME)
- Certified Identity and Access Manager (CIAM)
- CIDPRO
|
|
Security Operations Center (SOC)
|
Monitoring, detecting, and responding to security incidents in real-time
|
- SIEM tools and log analysis
- Attack vectors and IoCs
- Incident response procedures
- Threat intelligence feeds
|
- SOC Analyst
- Security Operations Manager
- Threat Hunter
|
- GIAC Certified Detection Analyst (GCDA)
- EC-Council Certified SOC Analyst (CSA)
- CompTIA CySA+
|
|
Incident Response
|
Preparing for and responding to cybersecurity incidents
|
- Incident response frameworks
- Digital forensics techniques
- Cyber attacks and indicators
- Problem-solving and communication
|
- Incident Response Specialist
- Cyber Incident Manager
- Security Incident Handler
|
- GIAC Certified Incident Handler
- EC-Council Certified Incident Handler (ECIH) - SANS Incident Response Certification
|
|
Digital Forensics and Incident Response (DFIR)
|
Investigating cyber incidents through digital evidence
|
- Forensic tools and techniques
- OS and file systems
- Legal requirements for digital evidence
- Malware analysis and reverse engineering
|
- Digital Forensics Investigator
- DFIR Consultant
- Forensic Analyst
|
- GIAC Certified Forensic Examiner (GCFE)
- EnCase Certified Examiner (EnCE)
- Certified Computer Forensics Examiner (CCFE)
|
|
Operational Technology (OT) Security
|
Securing critical infrastructure and industrial control systems
|
- Industrial control systems and SCADA
- OT-specific protocols and vulnerabilities
- ICS security frameworks and standards
- OT/IT convergence security
|
- OT Security Specialist - ICS Security Engineer - SCADA Security Analyst
|
- Global Industrial Cyber Security Professional (GICSP)
- Certified SCADA Security Architect (CSSA)
- ISA/IEC 62443 Cybersecurity Certificate Program
|
|
DevSecOps
|
Integrating security practices into the software development lifecycle
|
- Software development processes and tools
- Secure coding practices
- CI/CD pipelines and automation
- Containerization and orchestration
|
- DevSecOps Engineer - Application Security Engineer
- Secure Software Developer
|
- Certified DevSecOps Professional (CDP)
- AWS Certified DevOps Engineer
- Docker Certified Associate
|
|
Governance, Risk, and Compliance (GRC)
|
Ensuring regulatory compliance and managing security risks
|
- Compliance frameworks
- Risk assessment and management
- Security policies and procedures
- GRC tools and platforms
|
- Information Security Officer
- Compliance Manager - IT Risk Analyst
|
- Certified in Risk and Information Systems Control (CRISC)
- Certified Information Systems Auditor (CISA) - GIAC Governance, Risk, and Compliance Analyst (GRCA)
|
Verticals Bridging Offensive and Defensive Security
Some areas of cybersecurity don't fit neatly into either offensive or defensive categories. Instead, they play crucial roles in both aspects, demonstrating the interconnected nature of cybersecurity. Those who are interested in making career in both offensive and defensive security they should pay more attention in these verticals. Be remember, working in these verticals need deep technical, analytical, logical, and creative knowledge. Let's see the list of these hybrid verticals:
Application Security
DevSecOps
Threat Intelligence
Operational Technology (OT) Security
Product Security
Security Researcher or Bug Hunter
These hybrid verticals demonstrate the interconnected nature of cybersecurity, where offensive and defensive strategies often inform and complement each other. Professionals working in these areas often develop a well-rounded skill set that allows them to approach security challenges from multiple perspectives.
By understanding these diverse verticals, you can better appreciate the complexity of the cybersecurity field and identify areas that align with your interests and career goals. Remember, many cybersecurity professionals find their careers evolving across multiple verticals, gaining valuable experience and insights along the way.
Each of these verticals plays a crucial role in maintaining a robust defensive security posture. Many cybersecurity professionals find their careers spanning multiple verticals, as the skills and knowledge gained in one area often complement and enhance capabilities in others. As you explore these areas, you may discover that your interests and aptitudes align with one or more of these specializations, guiding your path in the dynamic field of defensive security.
[For more information on starting a career in cybersecurity, check out our comprehensive guide on how to begin your journey in this exciting field.]
Beyond Offense and Defense Security
While many cybersecurity roles can be categorized as either offensive or defensive, there is a unique field that doesn't fit neatly into either category. One such role is that of the Security Trainer or Cybersecurity Educator. This position plays a vital part in shaping the future of cybersecurity and organizations and individuals alike.
The Security Trainer: Bridging Knowledge Gaps
Security Trainers are responsible for educating individuals and organizations about various aspects of cybersecurity. Their role is neither offensive nor defensive in the traditional sense, but rather foundational and cross-cutting. They equip people with the knowledge and skills necessary to implement both offensive and defensive security measures effectively.
Conclusion
The world of cybersecurity is vast and multifaceted, offering a wide array of career paths for those interested in protecting our digital landscape. From the proactive approach of offensive security to the vigilant stance of defensive security, and the crucial bridging roles that span both domains, there's a place for diverse skills and interests within this field.
As we've explored the various verticals, it's clear that cybersecurity is not just about technical prowess. It requires a blend of analytical thinking, continuous learning, and often, strong communication skills. Whether you're drawn to the challenge of ethical hacking, the complexity of cloud security, or the importance of security education, the cybersecurity field offers rewarding careers with significant impact.
Remember, the journey into cybersecurity is ongoing. As threats evolve, so must our defenses and our skills. By understanding these diverse verticals, you're taking the first step towards finding your niche in this critical and dynamic field. The digital world needs dedicated professionals like you to keep it secure.
I hope, I this article answered your questions and helps you learn overview of cybersecurity and its different verticals in detail, including the expertise required to get into the specific verticals, different career roles, and certifications to learn and begin the career in the specific domain. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive tips like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.