Table of Contents
What Is A Denial Of Service Attack? How To Prevent Denial Of Service Attacks?
Denial of service (DoS) attacks can disrupt organizations’ networks and websites, resulting in the loss of businesses. These attacks can be catastrophic for any organization, business, or institution. DoS attacks can force a business into downtime for long time, resulting in immense loss of revenue. The Information Technology (IT) industry has seen a rapid increase in denial of service attacks. Years ago, these attacks were perceived as minor attacks by novice hackers who did it for fun, and it was not so difficult to mitigate them. But now, the DoS attack is a sophisticated activity cybercriminals use to target businesses.
In this article, we will discuss the denial of service attacks in detail, how it works, the types and impacts of DoS attacks, and how to prevent them. Let’s get started.
What Is a Denial Of Service (DoS) Attack?
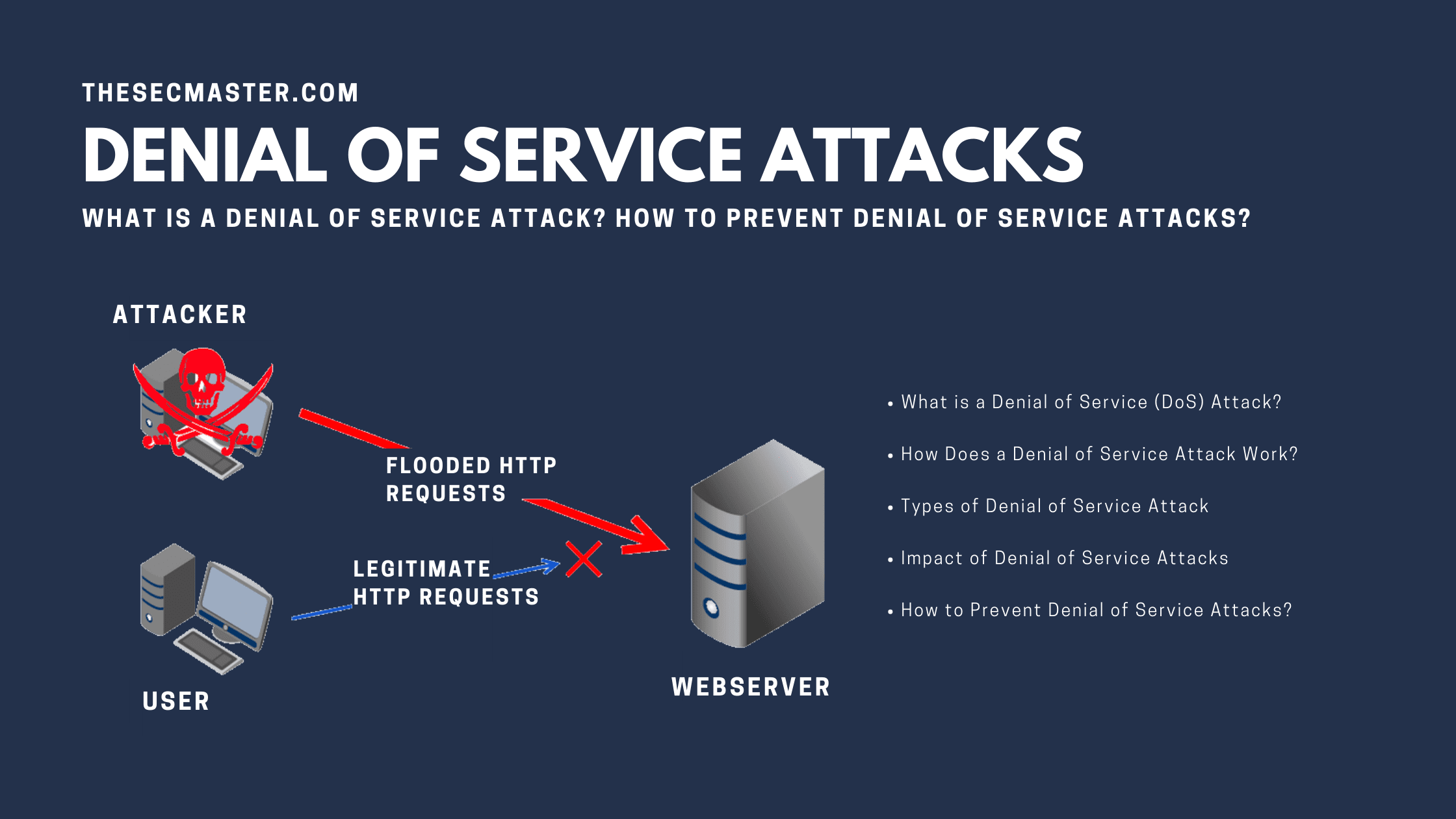
A denial of service (DoS) attack is designed to slow down networks or systems, making them inaccessible to users. Devices, information systems, or other resources on a machine or network, such as online accounts, email, e-commerce websites, and more, become unusable during a denial of service attack. Data loss or direct theft may not be the primary goal of a DoS attack. However, it can potentially damage the targeted organization financially because it spends a lot of time and money to get back to its position. Loss of business, reputational harm, and frustrated customers are additional costs to a targeted organization.
Victims of denial of service attacks often include web servers of high-profile enterprises, such as media companies, banks, government, or trade organizations. During a DoS attack, the targeted organization experiences an interruption in one or more services because the attack has flooded their resources through HTTP traffic and requests, denying access to authorized users. It’s among the top four security threats of recent times, including ransomware, social engineering, and supply chain attacks.
How Does A Denial Of Service Attack Work?
Unlike a malware or a virus attack, a denial of service attack does not need a social program to execute. However, it takes advantage of an inherent vulnerability in the system and how a computer network communicates. In denial of service attacks, a system is triggered to send malicious code to hundreds and thousands of servers. This action is usually performed using programs, such as a botnet.
A botnet can be a network of private systems infected with the malicious code controlled as a group, without the individuals knowing it. The server that can’t tell that the requests are fake sends back its response and waits up to a minute to get a reply in each case. And after not getting any response, the server shuts down the connection, and the system executing the attack again sends a new batch of fake requests. A DoS attack mostly affects enterprises and how they run in an interconnected world. For customers, the attack hinders the ability to access information and services on their systems.
http://thesecmaster.com/what-is-a-buffer-overflow-attack-and-how-to-prevent-it/
We can take a recently disclosed vulnerability in Log4J as an example for denial of service attacks. A vulnerability CVE-2021-45105 in Apache Log4j allows attackers to craft malicious input data containing a recursive lookup that leads to StackOverflowError and process termination, which could be a denial of service.
Types Of Denial Of Service Attack
Here are some common types of denial of service (DoS) attacks.
1. Volumetric attacks
It is a type of DoS attack where the entire network bandwidth is consumed so the authorized users can’t get the resources. It is achieved by flooding the network devices, such as switches or hubs, with various ICMP echo requests or reply packets, so the complete bandwidth is utilized, and no other user can connect with the target network.
2. SYN Flooding
It’s an attack where the hacker compromises multiple zombies and floods the target through multiple SYN packets simultaneously. The target will be flooded with the SYN requests, causing the server to go down or the performance to be reduced drastically.
3. DNS amplification
In this type of DoS attack, an attacker generates DNS requests appearing to originate from an IP address in the targeted network and sends requests to misconfigured DNS servers managed by a third party. The amplification occurs as a result of intermediate servers responding to the fake requests. The responses generated from the intermediate DNS servers may contain more data, requiring more resources to process. It can result in authorized users facing denied access issues.
4. Application layer
This type of DoS attack generates fake traffic to internet application servers, particularly Hypertext Transfer Protocol (HTTP) or domain name system (DNS). Some application layer attacks flood the target server with the network data, and others target the victim’s application protocol or server, searching for vulnerabilities.
Impact Of Denial Of Service Attacks
It can be difficult to distinguish an attack from heavy bandwidth consumption or other network connectivity. However, some common effects of denial of service attacks are as follows.
Inability to load a particular website due to heavy flow of traffic.
A typically slow network performance, such as long loading time for websites or files.
A sudden connectivity loss across multiple devices on the same network.
Legitimate users can’t access resources and are not able to find the information required to perform an action.
Repairing a website being targeted to a denial of service attack takes time and money.
How To Prevent Denial Of Service Attacks?
Here are some effective ways to prevent a DoS attack.
Limit broadcasting; A DoS attack often sends requests to all devices on the network that amplify the attack. Limiting the broadcast forwarding can disrupt attacks. Moreover, users can also disable echo services where possible.
Prevent spoofing: Check that the traffic has a consistent source address with the set of addresses and use filters to stop the dial-up connection from spoofing.
Protect endpoints: Make sure that all endpoints are updated and patched to eliminate the known vulnerabilities.
Streamline incident response: Honing the incident response can help the security team respond to the denial of service attacks quickly and efficiently.
Configure firewall and routers: Routers and firewalls must be configured to reject the bogus traffic. Make sure to keep your firewalls and routers updated with the latest security patches.
Enroll in a DoS protection service: Detecting the abnormal traffic flows and redirecting them away from the network. Thus the DoS traffic is filtered out, and the clean traffic is passed on to the network.
Create a disaster recovery plan: To ensure efficient and successful communication, mitigation, and recovery if an attack occurs.
We hope this post would help you know What is a denial of service attack. And, how to prevent denial of service attacks. Thanks for reading this threat post. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive updates like this.
You may also like these articles:
Protect Your Online Business from DDoS Attacks with These DDoS Protection Tools and Techniques
How to Fix CVE-2022-0778- A Denial-Of-Service Vulnerability In OpenSSL
How to Fix CVE-2022-20624- A Denial Of Service Vulnerability In CFSoIP Service Of Cisco NX-OS
How To Fix CVE-2021-1588- A Denial of Service Vulnerability in Cisco NX-OS Software
Mitigating the HTTP/2 Rapid Reset Vulnerability- CVE-2023-44487
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.