Table of Contents
What Is A Buffer Overflow Attack And How To Prevent It?
A buffer overflow happens when data exceeds the memory’s buffer capacity. During a buffer flow, a program throws data outside the buffer. This process crashes the program and corrupts data. Attackers know it, and the buffer overflow exploits techniques an intruder uses depending on the operating system and architecture being used by their target. However, the overloaded data in a program will likely contain malicious code allowing hackers to trigger actions and send instructions to applications. Criminals use a buffer overflow to execute arbitrary code, corrupt a web application’s execution stack, and take over a machine.
In this article, we will discuss buffer overflow attack, how it works, the types and impacts of buffer overflow attacks, and learn the ways to prevent them. Let’s get started.
What Is A Buffer Overflow?
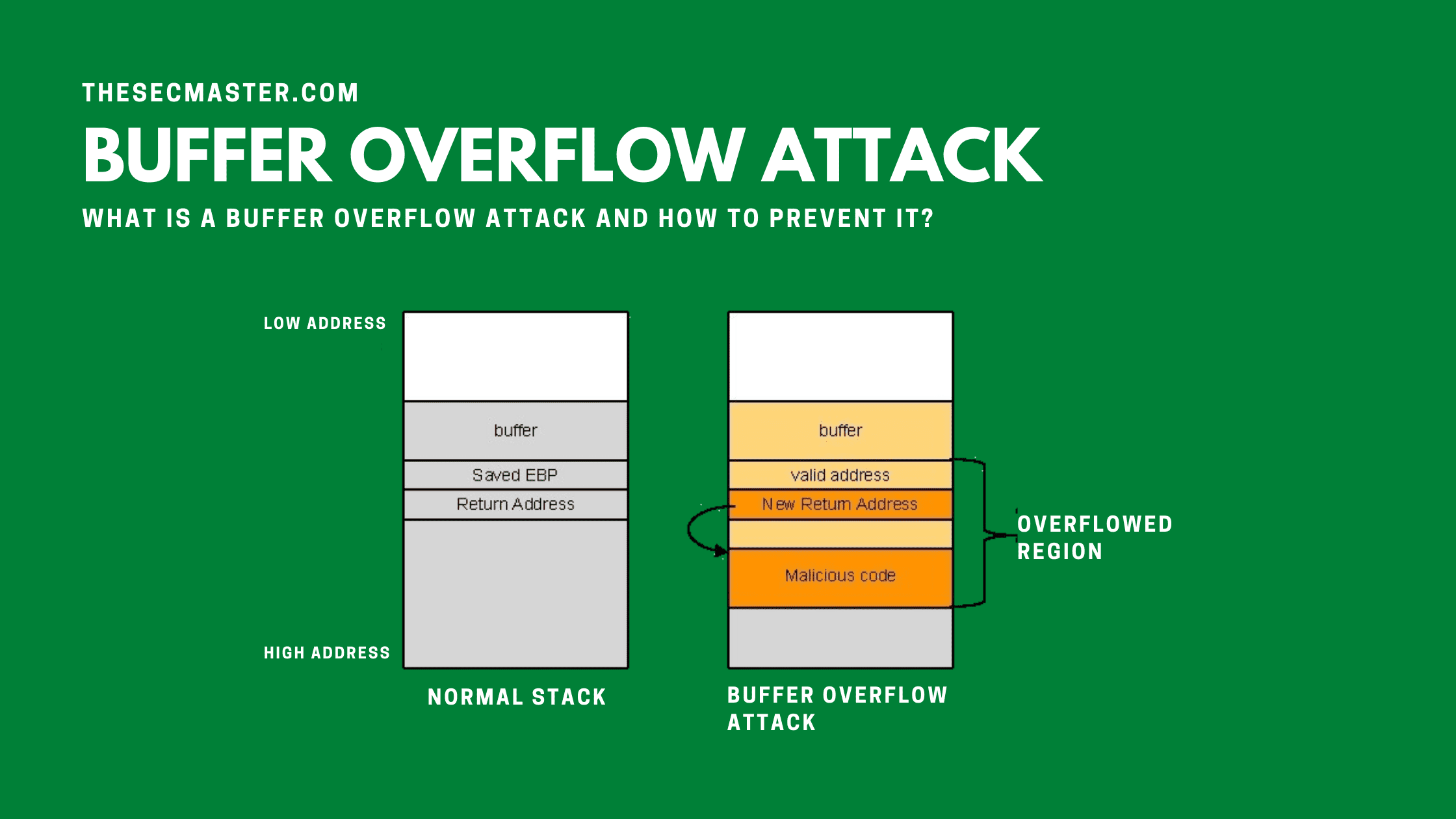
A buffer is a sequential area of memory allocated to contain data. A buffer overflow occurs when more data is put into the buffer than its capacity. This extra data or information can overflow into the adjacent memory space, overwriting or corrupting the data held in that section. This overflow can result in a system crash, creating opportunities for attackers to manipulate coding errors or execute arbitrary code to promote malicious actions.
What Is A Buffer Overflow Attack?
A buffer overflow attack occurs when an intruder manipulates the system coding error to execute malicious actions compromising the affected system. The attacker modifies the execution path of the application and overwrites memory elements, amending the program’s execution path to expose data or damage existing files. A buffer overflow attack generally involves overwriting the buffer bounds and violating programming languages. This attack usually takes place when the code is
reliant on external data for controlling the behavior.
so complex that developers can’t even predict its behavior accurately.
dependent of data properties enforced beyond its immediate scope
How Does Buffer Overflow Attack Work?
A buffer overflow attack occurs when a program tries to fill a memory section with more data than the buffer capacity. Attackers can force the application to run arbitrary code by sending a perfectly crafted user input to a vulnerable application. This arbitrary code execution can crash the system or take control of the machine. The attacker knowingly overwrites memory sections identified to hold executable code, modifies it, and significantly changes the way a program works.
Buffer overflow attacks can take place in web application servers providing static and dynamic web structures. Users of these products or services are considered to be at high risks because of extensive knowledge of buffer overflows. Moreover, the use of archives in web applications, such as graphics, for generating images can potentially increase the risks of buffers overflowing.
Heap Overflow Vulnerability CVE-2021-22045 in VMWare Products could be a good example for buffer overflow attacks. Successful exploitation of the vulnerability will let an attacker to escalate privileges and execute arbitrary code on Hypervisor from a virtual machine.
Different buffer overflow attacks target different pieces of code and use different strategies. Here are some common buffer overflow attacks.
1. Stack Overflow Attack
If the data kept on the stack is corrupted, attackers will overwrite the adjacent memory locations affecting the pointer or data stored by the other program. Steel overflow vulnerability uses stacked memory that exists during runtime. This vulnerability is found in C or C++ due to pointers. An intruder can take advantage of this vulnerability for exploiting a system by creating a pointer to execute malicious code or manipulating data.
2. Heap Overflow Attack
A heap overflow attack occurs when a memory section is assigned to the heap and data is written there without being checked. It may result in some critical data structures in heap, including heap headers, or heap-based data, such as dynamic object pointers, overwriting the virtual function table.
3. Integer Overflow Attack
An integer overflow attack occurs due to the arithmetic overflow error, in which the result of an integer function does not lie in the allocated area in the memory. Rather than a program error, it generally results in an unexpected result. In several programming languages, integer values typically have a specific number of bits in memory. Most integer overflow conditions can lead to inaccurate program behavior without causing any vulnerabilities. However, in some scenarios, an integer overflow can cause severe consequences, such as manipulating financial calculations.
4. Unicode Overflow
Unicode strings are created to ensure that all languages from each country can be used without transcription issues. For instance, Arabic characters are different from English characters. Such characters could not be converted based on the ASCII codes. However, these can be used with Unicode strings that allow users to take advantage of programs by typing Unicode characters in inputs expecting ASCII characters. The format string attack occurs when an application does not validate input data efficiently. It allows hackers to execute code and cause segmentation faults in an application.
Impact Of Buffer Overflow Attack
After a buffer overflow exploitation, your application can become unstable or return with error information. In some cases, data outside the buffer section may contain malicious commands bringing a multitude of problems to the application’s security. Let’s see what happens when a buffer overflow occurs.
An attacker takes control of the application by executing commands, known as arbitrary code execution, and happens when code executed in the buffer is executed.
When the application is executing on an operating system with system privileges, the arbitrary code execution vulnerability could be exploited by a hacker to perform an action called elevation of privileges.
The hackers can leverage a Denial of Service attack through Buffer Overflow. It can be an incredible source of equipment to execute other attacks, where millions of vulnerable tools are used to perform DDoS attacks.
How To Prevent Buffer Overflow Attack?
Here are some ways to prevent buffer overflow attacks.
The data execution prevention method prevents an attacker from being able to execute code in non-executable areas by flagging memory sections as executable or non-executable.
Buffer overflow attacks generally need to know where the executable code is located. Address space layout randomization (ASLR) moves at random around data region locations to randomize address space, making overflow attacks impossible.
Attackers look to overwrite the structured exception handling, which is a built-in system managing software, and hardware exceptions. They perform this operation using a stack-based overflow attack to overwrite the exception record. Structured exception handling overwrite protection (SEHOP) prevents hackers’ malicious code to attack the SEH and use it to overwrite the exploitation technique.
We hope this post would help you know What is a Buffer Overflow Attack and How to Prevent It. Thanks for reading this threat post. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive updates like this.
You may also like these articles:
What is Remote Code Execution? How To Prevent Remote Code Execution?
What Is Arbitrary Code Execution? How To Prevent Arbitrary Code Execution?
What Is Command Injection Vulnerability? And How To Prevent It?
What is a Privilege Escalation Attack? How To Prevent Privilege Escalation Attacks?
How To Fix CVE-2022-0778- A Denial-Of-Service Vulnerability In OpenSSL
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.