Table of Contents
What is Browser Isolation? How Do QR-Codes Could Help Attackers Bypass Browser Isolation Defence?
In today's evolving cybersecurity landscape, attackers continuously devise innovative methods to bypass security controls. As browser-based attacks become more sophisticated, organizations have implemented Browser Isolation technology as a critical defense mechanism. However, recent research by Mandiant has uncovered how threat actors can leverage QR codes to establish covert command-and-control channels, effectively circumventing browser isolation defenses.
Browser Isolation technology aims to protect users by separating web browsing activity from local endpoints, creating a secure barrier between potentially malicious web content and user devices. While this approach effectively counters many web-based threats, attackers have discovered creative ways to bypass these protections using QR codes - an increasingly ubiquitous technology in our smartphone-centric world.
In this blog post, we'll examine Browser Isolation technology, its various implementations, and how attackers leverage QR codes to establish command-and-control communications in isolated browser environments. We'll also explore the technical aspects of this novel attack technique and discuss potential mitigations that organizations can implement to protect against these threats.
What is Browser Isolation?
Browser Isolation is a cybersecurity technology that creates a secure barrier between users' web browsing activities and their local devices. This technology runs web browsers in a protected environment while only streaming visual content back to the user's device, effectively neutralizing web-based threats before they can reach the endpoint.There are three main types of Browser Isolation implementations:
Remote Browser Isolation (RBI): The most secure and widely adopted variant that executes browsers in a cloud environment. All web code and content processing happens on remote servers, completely isolated from end-user devices. Users receive only a secure pixel stream of the rendered content, ensuring no malicious code reaches their local machine.
On-premises Browser Isolation: Similar to RBI but operates within the organization's infrastructure. While offering better control over sensitive data, this approach requires careful configuration to prevent unauthorized access to internal network resources. It's particularly useful for organizations that need to access internal web applications without complex cloud-to-premises connectivity.
Local Browser Isolation: Utilizes containerization or virtualization technologies (like Docker or Windows Sandbox) to create an isolated browser environment on the local device. Though more resource-intensive than cloud-based solutions, it provides isolation without requiring external infrastructure.
Browser Isolation helps secure end-user browsers by:
Preventing malware and drive-by downloads from reaching endpoints
Protecting against zero-day exploits and browser vulnerabilities
Blocking credential theft attempts by isolating login sessions
Neutralizing malicious scripts and browser-based attacks
Creating an "air gap" between internet content and corporate infrastructure
How Does Browser Isolation Work?
Browser Isolation operates by creating a secure boundary between web browsing activities and the endpoint device. When a user requests a webpage, the request gets forwarded to a secure isolated environment - either in the cloud, on-premises, or locally virtualized. The isolated browser then handles all webpage rendering and code execution, ensuring that potentially malicious content remains contained.
Instead of directly loading web content on the user's device, Browser Isolation streams only the visual representation of the webpage back to the local browser. This secure pixel streaming technology means the user sees and interacts with websites normally, but no actual web code reaches their device. When users interact with the page through clicks or keystrokes, these actions are forwarded to the isolated browser which processes them and updates the visual stream accordingly.
Any file transfers, like downloads or uploads, go through rigorous security scanning before reaching the endpoint. This comprehensive isolation approach means that even if a user visits a malicious website, any harmful code executes only within the contained environment, effectively protecting the endpoint from web-based attacks. The isolated browser essentially acts as an "air gap" between potentially dangerous web content and the organization's devices and network.
Browser Isolation operates by creating a secure boundary between web browsing activities and the endpoint device. When a user requests a webpage, the request gets forwarded to a secure isolated environment - either in the cloud, on-premises, or locally virtualized. The isolated browser then handles all webpage rendering and code execution, ensuring that potentially malicious content remains contained.
Instead of directly loading web content on the user's device, Browser Isolation streams only the visual representation of the webpage back to the local browser. This secure pixel streaming technology means the user sees and interacts with websites normally, but no actual web code reaches their device. When users interact with the page through clicks or keystrokes, these actions are forwarded to the isolated browser which processes them and updates the visual stream accordingly.
Any file transfers, like downloads or uploads, go through rigorous security scanning before reaching the endpoint. This comprehensive isolation approach means that even if a user visits a malicious website, any harmful code executes only within the contained environment, effectively protecting the endpoint from web-based attacks. The isolated browser essentially acts as an "air gap" between potentially dangerous web content and the organization's devices and network.
Rise of QR-Code Popularity
Quick Response (QR) codes have become an integral part of our digital interactions since their invention in 1994 by Denso Wave, initially developed for tracking vehicles during manufacturing. These two-dimensional barcodes remained relatively niche until the smartphone revolution transformed them into a ubiquitous technology. The turning point came in 2017 when Apple integrated native QR code scanning capabilities into iPhone cameras, with other smartphone manufacturers quickly following suit.
Today, with over 6.8 billion smartphone users worldwide (representing 86% of the global population), QR codes have evolved from industrial tracking tools to essential components of daily digital interactions. The COVID-19 pandemic particularly accelerated their adoption, as businesses sought contactless solutions for sharing information, from restaurant menus to payment systems. This surge in smartphone adoption, especially in developing nations, has directly contributed to the widespread implementation of QR codes across various sectors.
How Do QR-Codes Work?
QR codes employ a sophisticated matrix structure that enables them to store significantly more data than traditional barcodes. The code's architecture consists of several key components working together to ensure reliable data transmission. Three large squares positioned in the corners serve as position detection patterns, helping scanners quickly identify and orient the code. Smaller alignment patterns scattered throughout help correct distortion, while timing patterns ensure accurate data grid alignment.
The actual data storage occurs in the black and white squares (modules) that make up the code's interior. Using Reed-Solomon error correction algorithms, QR codes can maintain data integrity even when partially damaged or obscured. This robust error correction capability allows successful scanning even if up to 30% of the code is damaged.
QR codes can store various types of data - from simple text and URLs to complex information like vCard data or even small applications. A single QR code can hold up to 2,953 bytes of data, making them versatile tools for information sharing. The code uses different encoding modes (numeric, alphanumeric, binary, and Kanji) to optimize data storage based on the content type, ensuring efficient use of available space while maintaining quick readability.
How Do QR-Codes Could Help Attackers Bypass Browser Isolation Defence?
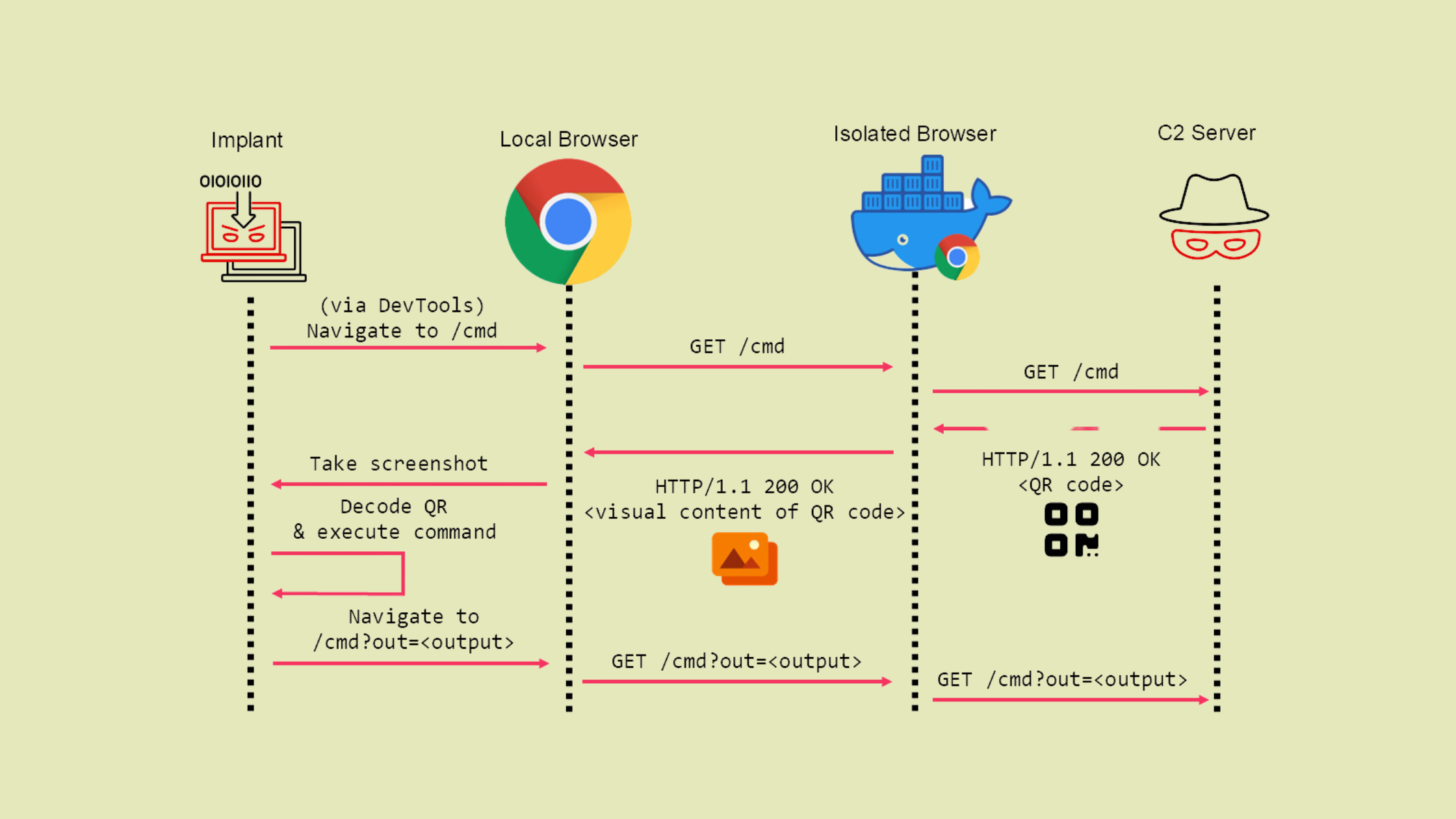
Mandiant recently uncovered a sophisticated technique that leverages QR codes to establish command-and-control (C2) channels in browser isolation environments. This novel approach exploits the fact that while browser isolation prevents direct code execution on endpoints, it must still transmit visual content to enable normal browsing.
The attack begins when a malicious implant on the victim's device controls a local headless browser through the DevTools protocol. Rather than using traditional HTTP responses for C2 communication, which browser isolation would block, the attacker's server returns webpages containing QR codes. The implant captures screenshots of these rendered pages and scans the QR codes to extract command data. After executing the commands, the implant sends results back to the C2 server.
What makes this technique particularly effective is its ability to work across all browser isolation implementations - remote, on-premises, and local. Since the C2 channel operates through the essential visual streaming component of browser isolation, it remains functional even when direct HTTP communication is restricted. The attack effectively turns the intended security barrier into a covert communication channel.
However, this technique does face some practical limitations. During testing, Mandiant found that QR codes were limited to 2,189 bytes of data due to visual quality constraints in the browser streaming. Additionally, each request cycle takes approximately 5 seconds due to browser rendering and QR code scanning overhead. These factors result in significantly lower bandwidth compared to traditional C2 channels - transferring a typical 323 KiB BEACON payload takes about 12 minutes and 20 seconds.
This discovery highlights how attackers can creatively repurpose legitimate technologies to bypass security controls. While browser isolation remains an effective defense against many web-based threats, organizations need to be aware of and monitor for these emerging bypass techniques.
Bottom Line
The discovery of QR code-based C2 communication highlights the ongoing evolution of attack techniques. While Browser Isolation remains a valuable security control, organizations must implement a defense-in-depth strategy.To protect against such attacks, organizations should:
Monitor for anomalous network traffic patterns
Watch for browsers running in automation mode
Implement comprehensive endpoint security
Regularly update security controls
Remember, no single security solution is perfect. Continuous monitoring, regular security assessments, and staying informed about emerging threats are crucial for maintaining a robust security posture.We hope this comprehensive analysis of Browser Isolation technology and the novel QR code-based bypass technique helps organizations better understand and defend against emerging threats. While Browser Isolation remains a valuable security control, security teams must stay vigilant against creative bypass methods that exploit legitimate features.Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.