Table of Contents
Detailed Anatomy of the Tor Network | Structure of the Tor Network
Tor is the backbone of the dark web. If you want to know about the technology behind the dark web, you should understand the tor network. This article will be the most interesting for those who want to know the anatomy or the structure of the tor network.
Elements of the Tor Network:
Tor nodes:
Nodes are the heart of the tor network. They have scattered all over the internet covering all geo-locations. These nodes take part in anonymizing the tor connection by maintaining the Perfect Forward Secrecy. Many individuals and organizations set up and configured these nodes to accept the tor connection and relay the connection to the next destination in the forward chain.
Elements of the Tor network
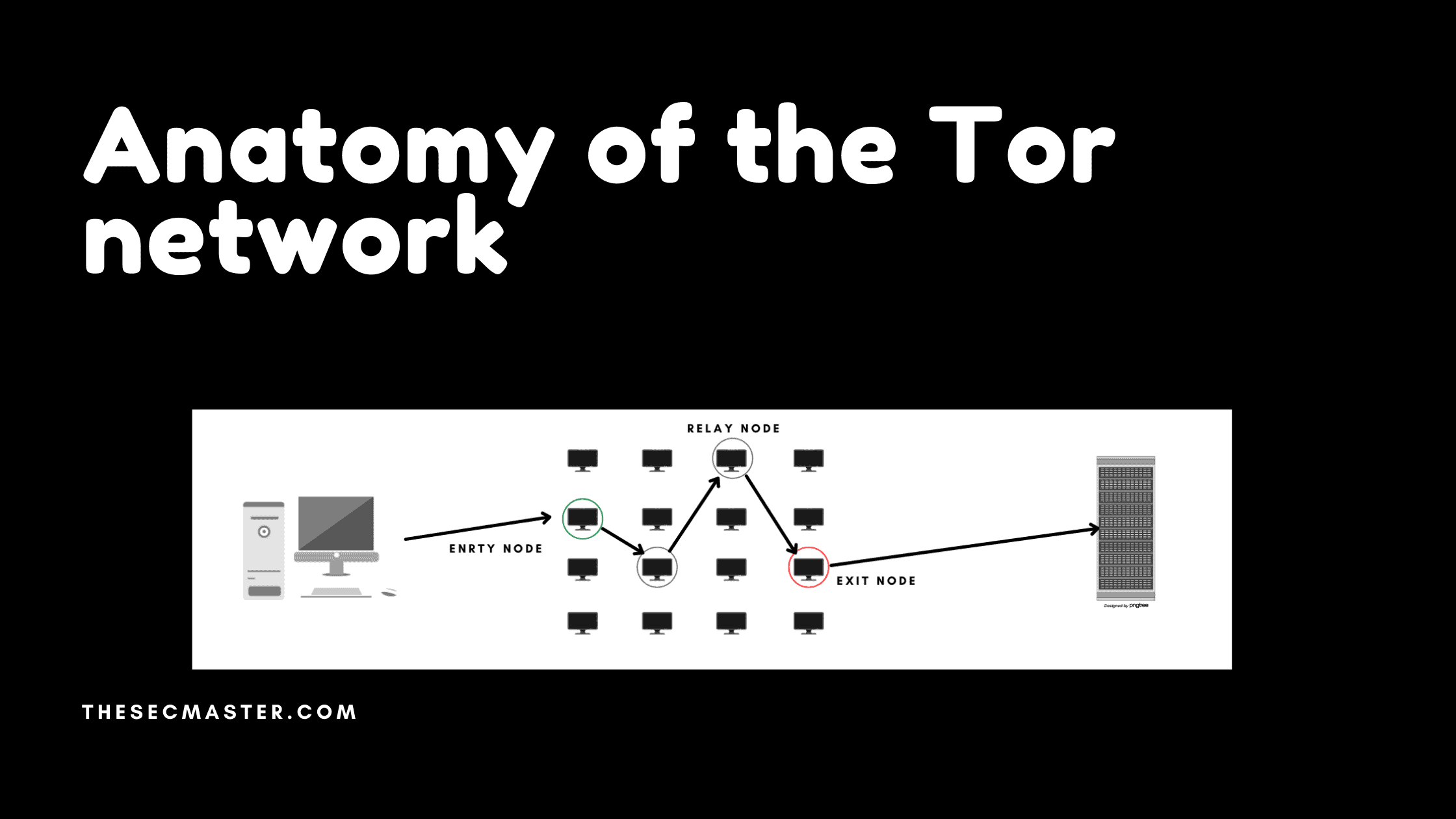
Each connection in the tor network consists of a minimum of three types of nodes:
Entry node: It is the first node where the traffic enters the tor network. Any relay node can act as an entry node. There is no difference in the function of the entry and relay nodes. But, there is a difference from the user’s point of view. The entry node is the node that has the real identity of the user. This is the extent of the knowledge the entry node has. The entry node only knows the identity of the user and the following node information. It doesn’t know about the destination because of the Perfect Forward Secrecy.
Relay node: Relay nodes accept the tor connections, unwrap the additional layer of the Perfect Forward Secrecy and relay the connection to the next node in the forward path chain. Default configurations have set only one node in the middle of the Tor circuit. But you can increase the number if you like. Be aware that as much as you increase the number of middle nodes, it increases the delay in the connection.
Exit node: The last type of node is the exit node. It is the node that communicates to the destination. Again, this node is no different from the other two nodes. But as it communicates to the destination server and forwards the traffic out of the tor network. It serves as the source for the destination server. Because of this, exit nodes are constantly being accused of their activities in the tor network. Exit nodes are constantly targeted by investigators. Owners of the exit node have to give explanations over and over to justify their servers.
Directory Servers:
This plays a critical role in maintaining the tor network. These servers are known as the brain of the tor network as these are the servers that store the identities of the nodes on the tor network. The identities of the directory servers are hardcoded into the tor browser. Tor networks manage very few handfuls of tor directory servers for tor network operations.
The main purpose of directory servers is to maintain the updates of the tor nodes. Directory servers keep monitoring all the activities of the nodes and replace the unhealthy nodes with healthy nodes for the stability of the tor network. When you fire up the tor browser, your tor browser first connects with directory servers to have the list of active nodes. Tor browser then selects one entry node, one exit node, and one relay node to form the circuit.
List of directory servers used in the tor network
Relays And Bridges:
We already said we have relay nodes in the previous section. If we go further, there are two different categories of relay nodes.
Advertised Relay nodes: These nodes are called advertised nodes as they are listed in the directory servers. These are the real nodes that help to anonymize the tor network by maintaining the Perfect Forward Secrecy. Anyone can see the identity of these nodes by querying them like a tor browser.
Bridge nodes: Bridge nodes are like any other nodes, with one difference being that these are not advertised, which means bridge nodes are not listed in the directory servers. You might ask what is the purpose of bridge nodes if they are not listed in the directory servers. The main reason to have these servers is to cover government agencies and internet firewalls; as you might know, tor nodes are often accused by security agencies because of their activities on the tor network. And these are easy to block as the identities of the tor nodes are publicly available on the directory servers. Bridge nodes are used to bypass the blocks. If a bridge node is serving as an entry node, it is hard to find and block the traffic on the firewalls as they are not listed in the tor directory servers. But, the main challenge to using a bridge node as an entry node is someone has to learn about the active bridge server, and it has to be configured manually on the tor browser.
Suppose you see the current figures of the relay and bridge nodes. There are approximately 6000 to 7000 relay nodes and close to 2000 bridge servers.
Number of relay and bridge nodes
This completes the anatomy or the structure of the tor network.
Thanks for reading this article. Please read more such interesting articles here:
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.