Table of Contents
How I Built Vulnerability Management Program for Our Client?
Implementing an effective vulnerability management program is critical for organizations that want to improve their security posture and reduce risk. As a security analyst, I recently had the opportunity to build out such a program for one of our clients. In this post, I’ll walk you through the key elements and steps I followed to make it a success.
Why Vulnerability Management Program is Critical?
Like many organizations, my client struggled to get a handle on vulnerabilities across their environment. With thousands of devices on the network and no centralized way to identify, track and remediate vulnerabilities, they were leaving themselves exposed. Attackers are always looking for ways to exploit common software flaws and misconfigurations to breach environments. And without visibility, organizations can’t adequately assess where they are most exposed.
Some of the core challenges my client faced that a vulnerability management program needed to help resolve included:
No centralized inventory of devices and software across their environment. New devices and apps could be added without security’s knowledge.
Limited visibility into what vulnerabilities existed. Scans only happened periodically rather than continuously.
Difficulty prioritizing remediation based on risk levels. Lacked context to understand vulnerability criticality.
Poor collaboration between security and IT teams responsible for remediation. Manual and fragmented processes to assign and track remediation work.
No validation vulnerabilities were fully resolved after remediations applied. Couldn’t confirm proper fix.
By implementing a comprehensive vulnerability management program focused on finding, prioritizing and resolving vulnerabilities, I aimed to help them tackle each of these challenges.
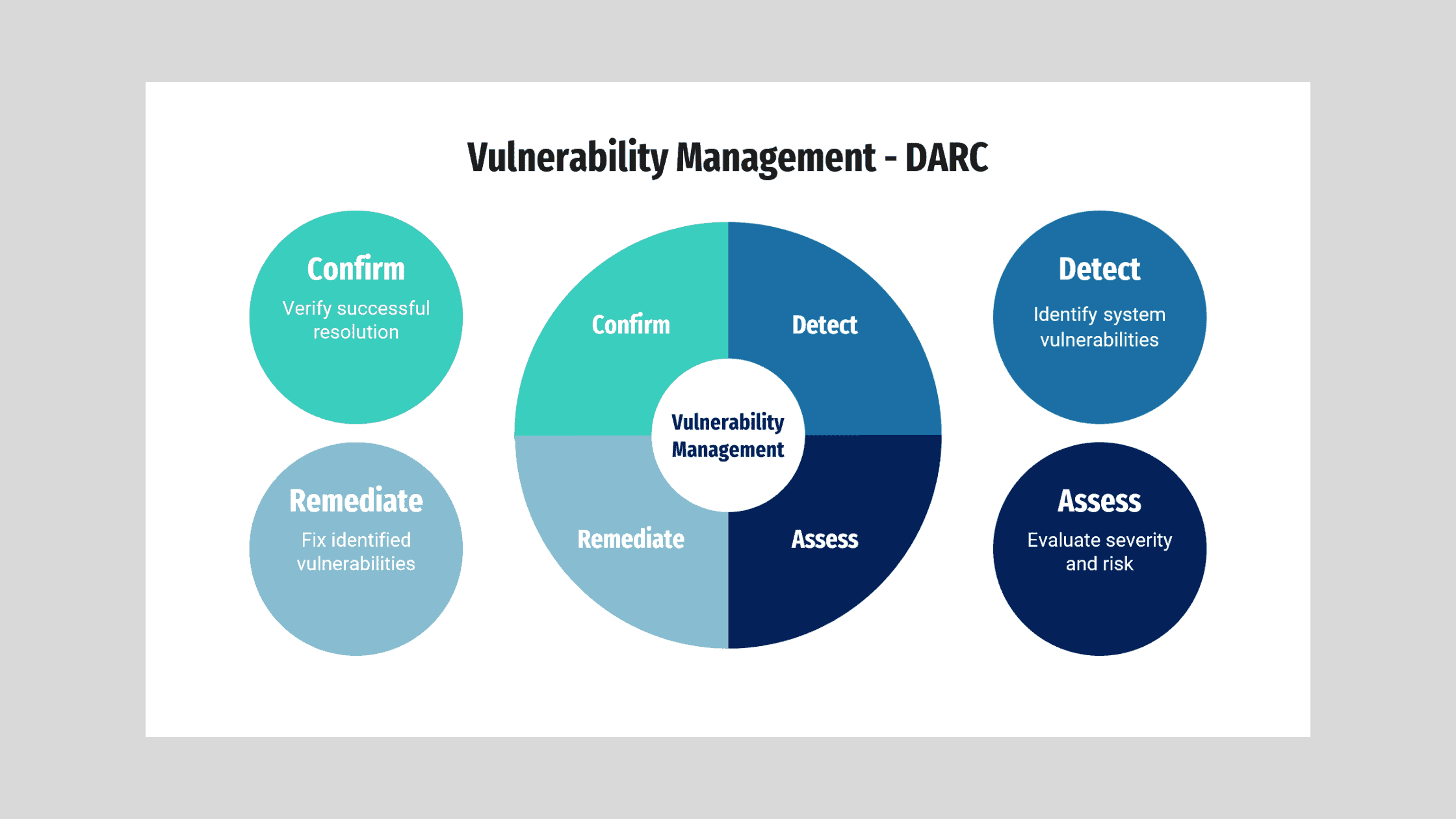
Guiding Principles for an Effective Vulnerability Management Program – DARC
When designing their program, I made sure to focus on the key tenants of effective vulnerability management. I used the DARC approach as a guiding framework:
D – Detect vulnerabilities across their infrastructure through periodic vulnerability scanning.
A – Assess the risk and potential impact of identified vulnerabilities using an industry standard scoring system like CVSS.
R – Remediate prioritized vulnerabilities by applying patches, updating configurations and removing unnecessary services.
C – Confirm that applied remediations fully resolve vulnerabilities through follow-up scans.
Keeping DARC at the core ensured I designed a program focused on finding, understanding and resolving vulnerabilities in a methodical way.
Detecting Vulnerabilities Through Continuous Scanning
The first step was implementing periodic vulnerability scanning powered by Rapid7 InsightVM to identify security misconfigurations and software flaws across their infrastructure. Vulnerability scanning works by remotely assessing devices and applications on the network to detect CVEs and expose areas of weakness.
I helped them evaluate scanning solutions like Nessus, Qualys and Rapid7 InsightVMthat would provide broad coverage across modern environments while minimizing false positives and false negatives. We landed on Rapid7 InsightVM as the scanning engine for the program given its industry leading accuracy rates, extensive vulnerability checks and easy integration with other systems.
To start, I focused scanning on internet-facing systems and VPN endpoints to gauge exposure from external threats like hackers. Over time, we expanded scanning deeper into internal network segments reaching databases, internal apps, user devices critical for business operations.
Automating scans on a weekly basis gave us continuous visibility enabling us to detect new vulnerabilities as they emerged across the environment rather than relying on infrequent or manual assessments. New devices and software added to the network gets picked up in scans automatically.
We now have a continuously updated centralized inventory of devices, software and associated vulnerabilities fueling all downstream vulnerability management workflows.
Risk-Based Prioritization of Vulnerabilities
With thousands of vulnerabilities being detected through the scans, I needed to help them prioritize remediation efforts based on risk and potential impact. Not all vulnerabilities pose the same level of risk and they needed to be able to understand which warranted immediate attention vs lower priority queues.
I leveraged vulnerability criticality ratings like CVSS scores coupled with contextual factors like system criticality and threat exposure levels. This allowed me to categorize vulnerabilities as low, moderate, high or critical risk. Parameters included:
CVSS Score: Industry standard 0-10 rating with 10 extremely critical
Threat Exposure: External facing, internal network or restricted segment
Operational Criticality: Essential for business operations or redundant/failover
Data Sensitivity: Process PII, healthcare data or intellectual property
Critical risk vulnerabilities that could significantly disrupt operations or lead to data compromise were slated for immediate remediation. High risk issues went to front of the queue while moderate items could be bundled for periodic maintenance. Low risk items were simply tracked.
This personalized risk rubric ensured resources stayed focused on resolving the most dangerous vulnerabilities first based on potential impact.
Streamlined Remediation Workflow Between Security and IT Teams
With vulnerabilities prioritized, I next helped build out seamless collaboration between security and IT teams responsible for remediation. Scaling a vulnerability program requires breaking down siloes, increasing transparency and coordinating activity between functions.
I configured our vulnerability management platform InsightVM to automatically raise remediation tickets and send customized alerts to the relevant IT professionals as new vulnerabilities requiring action were found.
Remediation tickets included details like affected systems, precise vulnerability data (CVE ID, CVSS scores), detailed remediation steps and automated tracking mechanisms to simplify execution at scale.
Daily ticket batches delivered to each IT group gave complete transparency into current vulnerabilities falling under their domain along with an efficient vehicle to manage the remediation process end-to-end. Security team maintained oversight of all open tickets, priority levels and aging through aggregate reporting and dashboards powered by InsightVM.
Validating Remediation Success Through Follow-Up Scans
The final piece was implementing continuous post-remediation validation to confirm when vulnerabilities were successfully neutralized across the environment. Assuming vulnerabilities are fixed without validation testing often leads to holes persisting unknowingly.
Leveraging our scanning capabilities, I built in automatic verification scans powered by Rapid7 InsightVM on a weekly basis. These scans specifically test for the vulnerability on affected systems after remediations are applied to ensure they no longer present.
Only when the vulnerability is no longer detected post-remediation is the ticket cleared. Any lingering detections automatically trigger a new cycle of troubleshooting and remediation until resolved.
This confirmation process ensures vulnerabilities are completely neutralized rather than just assumed fixed as work gets handed off between teams. Ongoing scans ultimately strengthen accountability and quality assurance mechanisms.
Business Outcomes and Impact Delivered
After months collaborating across security and IT to build their program anchored in DARC principles, the outcomes have been very positive:
3x increase in vulnerability detection rates enabling proactive remediation for threats before exploitation
75% of critical severity vulnerabilities now successfully remediated within 15 days vs 60+ days historically
35% reduction in internet-facing systems operating with severe vulnerabilities
85% of manual processes around vulnerability operations now automated through InsightVM
By taking a strategic approach focused on continuous discovery, risk-based analysis and streamlined remediation tracking for vulnerabilities, they now have enhanced visibility, control and response capabilities leading to better security and lower risk. Leadership interest and investment continues to increase as the program matures and delivers tangible risk reduction quarter-over-quarter.
Looking ahead, we have plans to continue expanding vulnerability management deeper into the infrastructure, integrate threat data to boost risk scoring accuracy and ultimately enable self-remediation capabilities for simple fixes that don’t require human intervention.
If you have any other questions about building an effective vulnerability management program, I’m happy to discuss my experience and strategies in more detail!
We hope this post helped in learning about how I built vulnerability management program for our client. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.