Table of Contents
How To Fix The Microsoft Exchange Autodiscover Flaw?
Guardicore Team has uncovered a design-level flaw in Microsoft Exchange Autodiscover, which could result in the leak of millions of usernames and passwords across the globe. In the report, Guardicore Team said that it acquired multiple Autodiscover domains with a TLD suffix, and they have set them up to reach a web server that they control. They also added that they had detected a massive leak of Windows domain credentials that reached their server. According to the report, they have captured 372,072 Windows domain credentials in total. Out of which, 96,671 were unique credentials captured from the applications connected to the Microsoft Exchange, such as Microsoft Outlook, mobile email clients, and other applications from April 16th, 2021 to August 25th, 2021. These numbers are really terrific. The flaw can cause massive damage to the business. It is highly important to address this issue. Let’s see how to fix the Microsoft Exchange Autodiscover flaw.
Data gathered by Guardicore
What Is Microsoft Exchange Autodiscover?
Normally, users will have to configure multiple settings to configure a mail client such as Microsoft Outlook, ActiveSync, and mobile email clients. Users may need this information to configure their email clients:
Username and password.
The IP addresses or hostname of the Exchange server.
In some cases, additional settings such as Miscellaneous LDAP settings, WebDAV calendars, etc, are required to configure mail clients.
Microsoft Exchange Autodiscover assists users in configuring their email clients with Exchange Servers. Technically, the autodiscover is a protocol used by Microsoft Exchange for the automatic configuration of clients. You can learn more information about the autodiscover from Microsoft’s website.
How Does Microsoft Exchange Autodiscover Work?
For the first time, when a user adds his account on his Outlook. Outlook will display a prompt to the user to supply his user name and password.
After the user fills all the required details, In the background, Outlook will then parses the email address supplied by the user and then builds an autodiscover URL in the below format based on the email address of the user.
https://Autodiscover.example.com/Autodiscover/Autodiscover.xml
http://Autodiscover.example.com/Autodiscover/Autodiscover.xml
https://example.com/Autodiscover/Autodiscover.xml
http://example.com/Autodiscover/Autodiscover.xml
3. Then Outlook sends the URLs to the autodiscover and configure the user account on Outlook.
How Attackers Exploit Microsoft Exchange Autodiscover Flaw To Capture User Credentials?
To know where the flaw exists in autodiscover, let’s continue with the previous process. Let’s presume non of the URLs are responding. Autodiscover will start its “back-off” algorithm. Actual flaws exist in the back-of algorithm.
By Guardicore
When autodiscover see no response from any of the URLs, its back-off algorithm always keep try resolving the the ‘Autodiscover’ portion of the domain.
When the request fails, autodiscover sends the subsequent request to http://Autodiscover.com/Autodiscover/Autodiscover.xml.This means all the requests will go to Autodiscover.com instead of the original domain. Click here if you want to know more information about the autodiscover.
The Attacker will make use of this flaw to capture the information sent by Outlook. The Attacker will set up a web server with the domain ‘Autodiscover.com‘ and start receiving web requests from various Autodiscover endpoints.
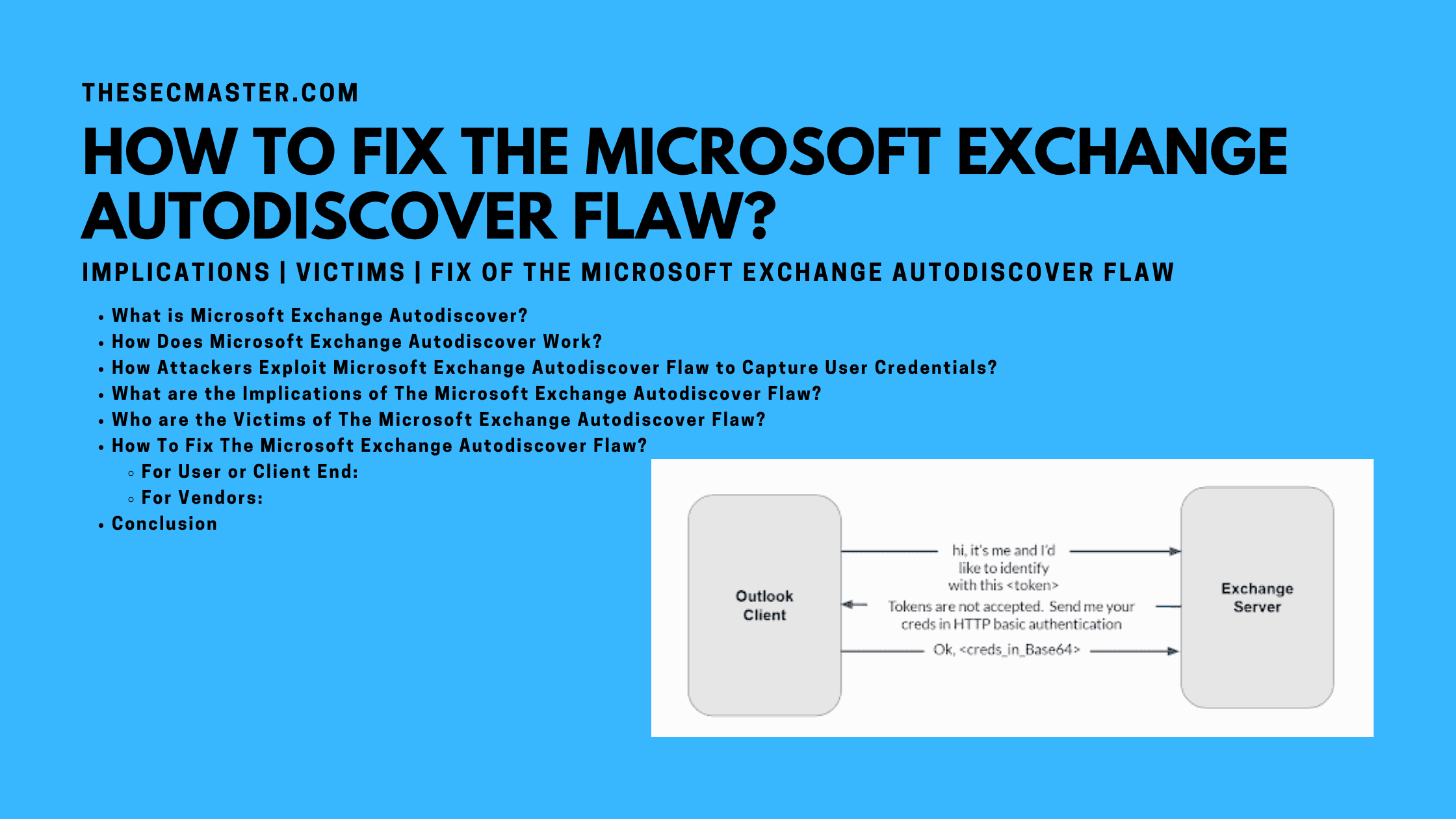
The most concerning about the request is, the request will have the relative path of /Autodiscover/Autodiscover.xml with the Authorization header and credentials in HTTP basic authentication.
The server will respond to the client with an HTTP 401 response.
Upon receiving the HTTP 401 response from the server, the client will downgrade, telling the server to use HTTP Basic Authentication.
The Victim will see a Certificate Invalid error dialog box, which could be fixed just by deploying any valid SSL certificate.
The Victim will see a legitimate authentication prompt after a secure session has been established with a valid certificate.
This is the critical and last step. When the Victim enters the credentials on the authentication prompt and sends, the Attacker’s web server will receive the credentials. The attacker can see the username and password in the server’s logs.
In this way, attackers can exploit Microsoft Exchange Autodiscover flaw and capture user authentication details. This is a high severity security issue. It can cause massive damage to the business. It is highly important to fix this flaw. Let’s read the coming section to see how to Fix The Microsoft Exchange Autodiscover Flaw.
What Are The Implications Of The Microsoft Exchange Autodiscover Flaw?
Implications are quite dangerous. By exploiting this flaw, attackers can:
Sniff the Exchange server’s, domain controller, or network traffic of the Victim from remote.
Capture user’s domain credentials in plain text over HTTP basic authentication.
Have DNS-poisoning capabilities on a large scale.
Who Are The Victims Of The Microsoft Exchange Autodiscover Flaw?
Any users who will use email clients like Outlook, ActiveSync, mobile email client, and any other client applications connect with Microsoft Exchange server. The users who connect Exchange server over the internet are more vulnerable to the attack.
How To Fix The Microsoft Exchange Autodiscover Flaw?
Looking at the implications, we can say that it is a critical flaw that should be fixed or mitigated to avert the damage. Let’s see how to fix The Microsoft Exchange Autodiscover flaw.
You can fix the Microsoft Exchange Autodiscover flaw in two different levels:
The user or the client who uses email clients over the public network.
Vendors who will implement the Autodiscover protocol in their mail client applications.
For User or Client:
On the client-side, this flaw can be mitigated by blocking Autodiscover domains in your firewall. Block all the below domains in your Firewall, Web Proxy, EndPoint solution, NIDS, HIDS, and where ever you have blocking controls.
Autodiscover.com.br – Brazil
Autodiscover.com.cn – China
Autodiscover.com.co – Columbia
Autodiscover.es – Spain
Autodiscover.fr – France
Autodiscover.in – India
Autodiscover.it – Italy
Autodiscover.sg – Singapore
Autodiscover.uk – United Kingdom
Autodiscover.xyz
Autodiscover.online
We can mitigate the flaw just by disabling the HTTP basic authentication when setting up an exchange server. This will stop sending credentials in plain text over the wire.
Block the domains listed in the txt file on your network block controls: https://data.iana.org/TLD/tlds-alpha-by-domain.txt.
The file has the list of all possible autodiscover.[tld] domain combinations. Just map loopback IP address 127.0.0.1 to all the domains listed in the txt file in the host file. Visit here for more information.
Host file location in Windows: %windir%\System32\drivers\etc\hosts
Host file location in Linux and macOS: etc/hosts
For Vendors:
In the development or implementation phase, Design the ‘back-off algorithm of the product in such a way that it never constructs URLs with domains like ‘Autodiscover.’
Conclusion
In the post, we have covered most of the things which are required to know about the Autodiscover service. We have started the post from what is Autodiscover, then we have explained its working and the flaw with the ‘back-off’ algorithm. Then its implications, victims, and at last the most important how to fix the Microsoft Exchange Autodiscover flaw.
We hope this post will help you fix the flaw and help protect your employees, customers, and partners in protecting their credentials from threat actors. Thanks for reading this threat post. Please share this post and help to secure the digital world. Please visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive updates like this.
You may also like these articles:
How To Mitigate CVE-2022-41040- A 0-Day SSRF Vulnerability in Microsoft Exchange Server
New Workaround to Mitigate the ProxyNotShell, Two 0-Day Vulnerabilities in Microsoft Exchange Server
How Is Microsoft Exchange Vulnerability Being Exploited by Prometei Potnet?
How To Fix CVE-2022-26809- A Critical RCE Vulnerability In Windows RPC Runtime
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.