Table of Contents
How To Secure Your PC from ‘Inno Stealer’- A Fake Windows Update Installer
A well-known threat intelligence firm CloudSEK has disclosed an active campaign running against Windows 11 PCs. CloudSEK also revealed that a fake Windows update installer, ‘Inno Stealer’, is being used in the campaign that could allow attackers to steal browser data and cryptocurrency wallets. Since this is a new strain of malware that doesn’t have any code similarities to any commodity malware or trending info stealers and found no evidence of the malware being uploaded to the Virus Total scanning platform, it is highly important to be aware and know how to secure your PC from Inno Stealer, a fake Windows update installer malware.
Let’s see more about the campaign and Inno Stealer (A fake Windows update installer) malware in this post.
About CloudSEK:
CloudSEK is a leading provider of cloud security solutions. CloudSEK’s products and solutions are designed to help organizations protect their data from loss or theft and ensure that only authorized users have access to sensitive data. CloudSEK also offers consulting services to help organizations with their cybersecurity needs.
CloudSEK offers two primary products: Xvigil and Bevigil. Xvigil is a cloud-based security monitoring and response platform. Bevigil is a cloud-based security intelligence platform. Both products are designed to help organizations secure their data and systems in the cloud.
Xvigil provides real-time visibility into an organization’s cloud environment, enabling them to quickly detect and respond to threats. Bevigil gives organizations the ability to proactively monitor for threats and vulnerabilities in their cloud environment. Both products offer a variety of features and benefits that can help organizations secure their data and systems in the cloud.
Xvigil Offers The Following Features:
Real-time visibility into an organization’s cloud environment
The ability to quickly detect and respond to threats
A variety of security policies that can be customized to fit an organization’s needs
The ability to monitor for compliance with industry regulations
A central repository for all security events
Bevigil Offers The Following Features:
Proactive monitoring for threats and vulnerabilities in an organization’s cloud environment
The ability to generate reports on potential risks and vulnerabilities
The ability to create custom dashboards for easy viewing of security data
A central repository for all security events
The ability to integrate with other security products and platforms.
A Fake Windows Update Installer Campaign:
Security researchers at CloudSEK recently revealed a fake Windows update campaign in that attackers try to steal information from the victim machines. In this campaign, attackers offer a fake Windows 11 update file which is bundled with an info stealer malware named Inno Stealer.
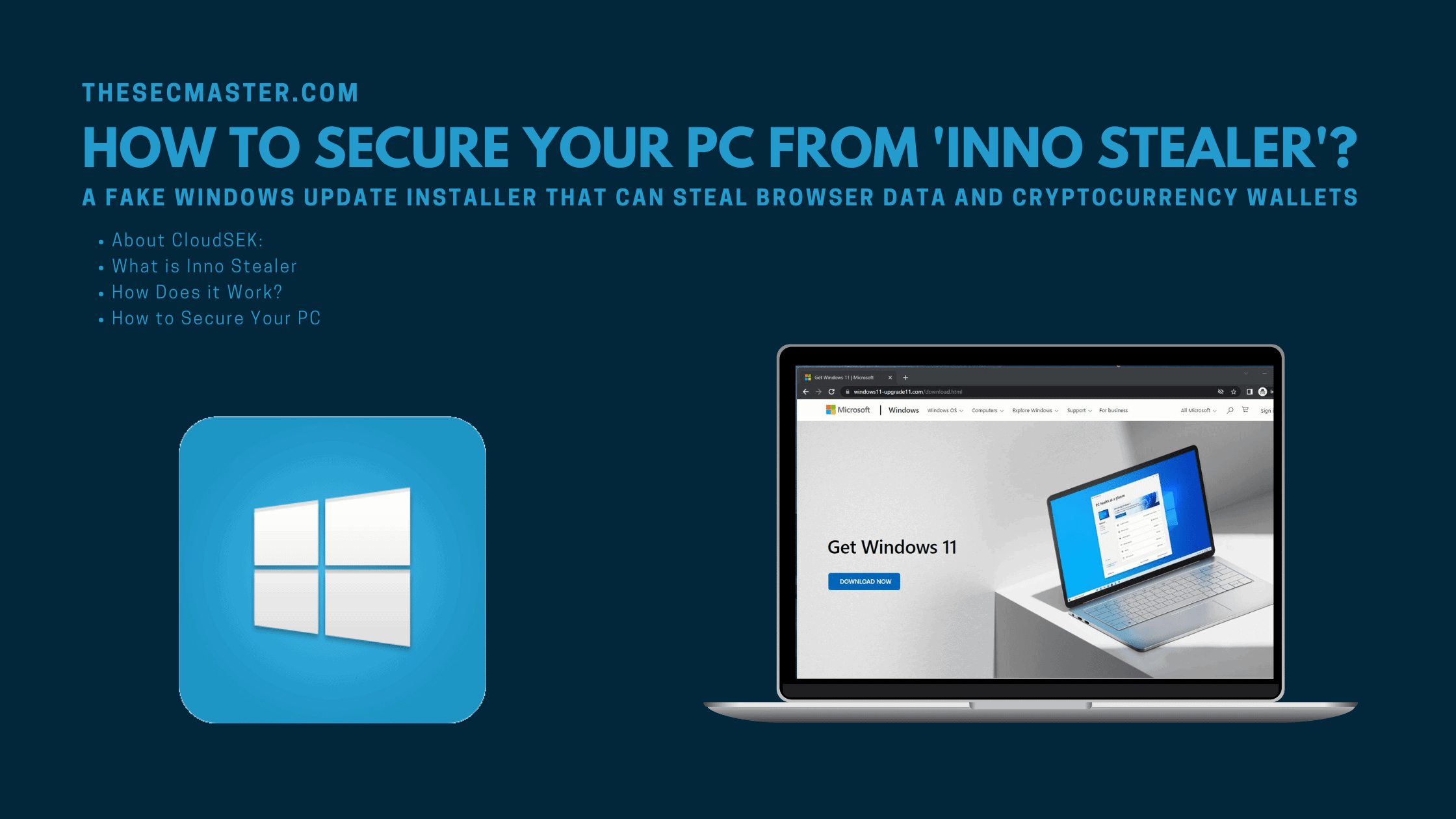
Attackers have hosted a malicious website, ‘ windows11-upgrade11[.]com’, that serves malicious Windows 11 updates. The web page has been created with official Microsoft logos, favicons, and a “Download Now” button. Once a user clicks on the Download Now button, the fake installer will start downloading the malicious ISO file. However, users are able to download only if they access the site directly on their browser. Users can’t download the ISO file over the VPN or Tor network. The site is still live at the time of publishing the post, so please don’t try accessing the site on your browser without protection.
What Is Inno Stealer Capable To Steal?
Inno Stealer is an info stealer malware that can be used to steal sensitive information from your computer. It can be used to access your personal information, such as your passwords and credit card numbers, as well as to install malicious software on your computer without your knowledge or consent. Inno Stealer is also capable of stealing cookies from your web browser, which can be used to track your online activity and gather sensitive information about you. It stores all the stolen data in the user’s temporary directory, encrypts them, and eventually delivers them to the operator’s command and control server.
Data It collects:
Web browser cookies
Stored credentials
Data in cryptocurrency wallets
Data from the filesystem.
Clipboard information
List Of Web Browsers Targeted By Inno Stealer:
List Of crypto Wallets Targeted By Inno Stealer:
Looking at all the capabilities of Inno Stealer, it can harm your privacy and secrecy, and sometimes it may lead to financial losses. We urge you to learnto secure your PC from Inno Stealer, a fake Windows update installer malware.
How Does Inno Stealer Work?
The infection process starts when a user opens up the web page’ windows11-upgrade11[.]com’ and clicks on the “Download Now” button. As soon as the user clicks on Download Now, a malicious ISO file will get downloaded.
The ISO file consists of ‘Windows 11 setup’ executable file. When the user launches the Windows 11 setup file, the loader file (Delphi-based) inside the Windows 11 setup file gets launched and dumps a temporary file named is-PN131.tmp. The loader then spawns a new process using the CreateProcess Windows API feature to establish persistence and covertly work under the radar.
Then the loader drops four files that are capable of disabling Registry security, adding Defender exceptions, uninstalling security products, and deleting the shadow volume. These capabilities made it more difficult to detect. More technical details are available here.
How To Secure Your PC from ‘Inno Stealer’- A Fake Windows Update Installer?
We have all seen the fake windows update messages. They look very convincing and can trick even the savviest computer user. These updates are not from Microsoft and often contain malicious code that can harm your computer. So how can you secure your PC from fake Windows updates like Inno stealer malware?
Avoid clicking on links in email messages or on websites that purport to be from Microsoft or another trusted source offering a windows update. These are often fake updates that contain malware.
Go directly to the Microsoft website to download windows updates.
Be cautious of any unsolicited emails or pop-ups offering windows updates, even if they appear to be from Microsoft. These may also be attempts to install malware on your PC.
Keep your antivirus software up to date and run regular scans of your computer to detect and remove any malicious software that may have been installed without your knowledge.
Keep your operating system and software up to date with the latest security patches. These can help to protect your computer from new threats.
Use a firewall to block IoCs and help protect your computer from unauthorized access and malicious software.
Use caution when downloading files from the internet, especially executables (.exe) or scripts (.bat). These may contain malware that can infect your computer. If you’re unsure about a file, scan it with antivirus software before opening it.
By following these simple tips, you can protect your computer from fake windows updates and other malicious software. Stay safe online!
We hope this post would help you know How to Secure Your PC from ‘Inno Stealer’- A Fake Windows Update Installer. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium & Instagram, and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.