Table of Contents
What is Symmetric and Asymmetric Encryption?
Cryptography was introduced to the world because, throughout history, there has always been a need to keep information confidential and secure. Imagine ancient generals wanting to send battle plans without enemies figuring them out or individuals wanting to share personal messages without the fear of someone eavesdropping. As societies evolved, so did the methods of communication, and with it, the need for more sophisticated ways to protect sensitive data. Cryptography became a crucial tool, providing a shield against prying eyes and unauthorized access. Governments, businesses, and individuals began employing cryptographic techniques to encode their messages and information, ensuring that only those with the right keys could unlock and understand the content.
In today’s article, we will discuss the goals of cryptography, what is symmetric and asymmetric cryptography, And the difference between symmetric and asymmetric encryption.
What Are the Goals of Cryptography?
In the domain of cybersecurity, several fundamental principles play a crucial role in safeguarding information.
Confidentiality acts as a guardian, ensuring that data remains private whether it’s stored, in transit, or actively being used.
Integrity serves as a watchdog against unauthorized alterations, providing checks to confirm that stored data retains its original state from creation to access.
Authentication takes center stage in verifying the identities of system users, a crucial function within cryptosystems.
Nonrepudiation serves as both a reassurance and a deterrent. It assures the recipient that the message indeed originated from the claimed sender, preventing any mischievous claims from the sender that they never dispatched the message in the first place.
Together, these principles form the bedrock of a robust cryptographic framework, fortifying the security of digital communication and data exchange.
General Terminologies for Encryption
Before we dive into the world of cryptography, you must be aware of a few terminologies associated.
Plain Text: Plain text is the easily readable and unencrypted form of human-readable data.
Cipher text: Cipher text is the transformed or encoded version of data, intended to be unreadable without the appropriate decryption key.
Keys: Cryptographic algorithms depend on keys for their security, and essentially, a key is a numerical value, often a large binary number, serving as a fundamental component in the encryption process. Cryptographic keys are sometimes referred to as crypto variables.
Cryptography: It involves the creation and application of secret codes and ciphers.
Cryptanalysis: This is the exploration of techniques to overcome codes and ciphers.
The collective term for cryptography and cryptanalysis is commonly known as cryptology.
Cryptosystems: Specific applications of a code or cipher in hardware and software are termed cryptosystems.
What Is Symmetric Encryption?
Symmetric encryption is a type of encryption where the encryption and decryption of a message happens using the same key. For symmetric encryption to happen both the sender and receiver should have or agree upon the same key.
Symmetric encryption jumbles up data using a secret key, making it unreadable without that key. The recipient, who has the key, can then unscramble the message, and read it. The key can be a shared password, or a random string of letters or numbers created by a secure system. It’s like a secret code that only the sender and receiver know.
Symmetric encryption algorithms come in two types:
Block algorithms: These encrypt fixed lengths of bits in electronic data using a specific secret key. The data is held in the system’s memory, waiting for complete blocks as it gets encrypted.
Stream algorithms: Instead of holding data in memory, this type encrypts data on the go as it streams through the system.
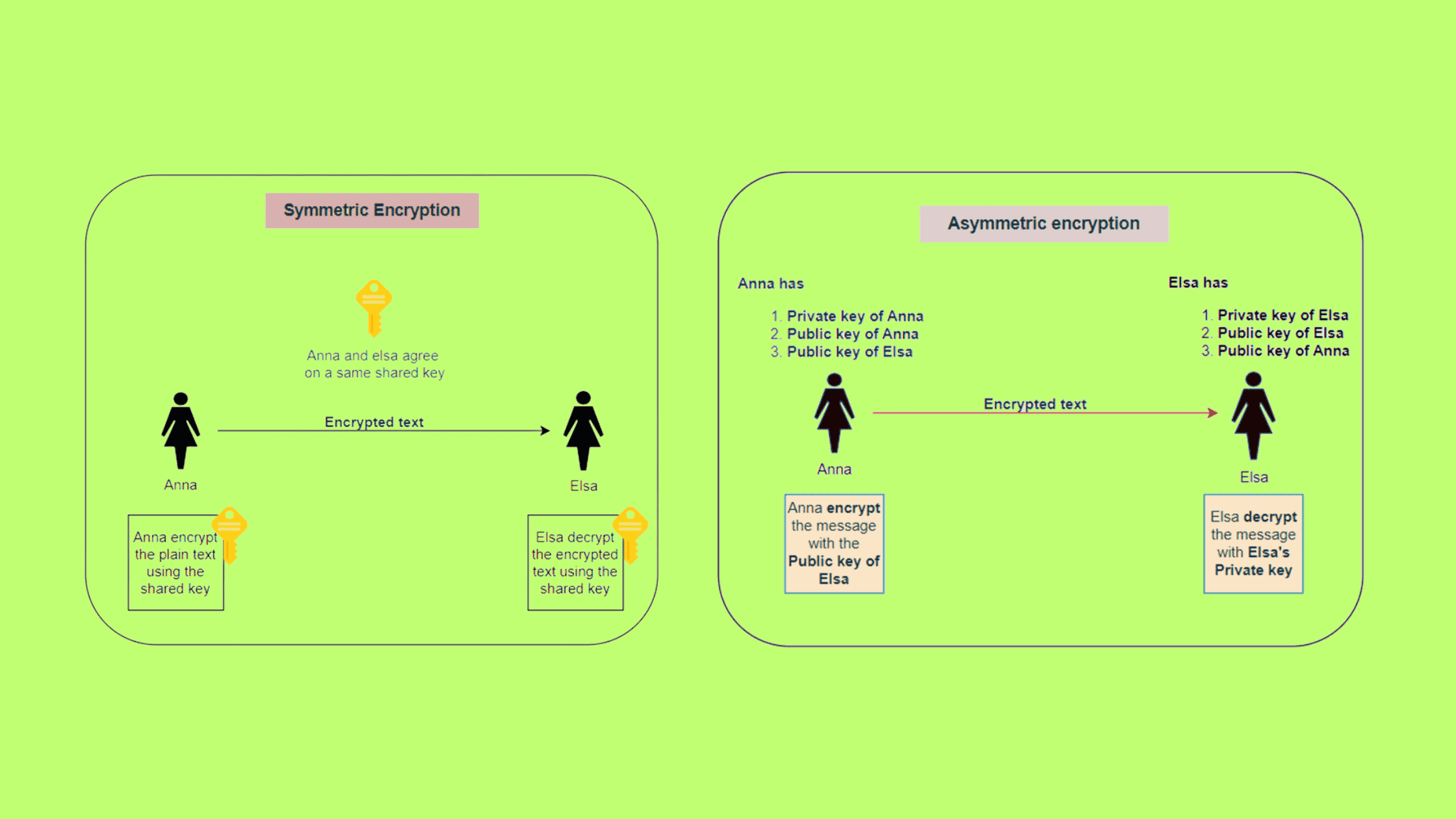
In the below example, we can see Anna wants to share a message secretly with Elsa using symmetric encryption. Here we can see both Anna and Elsa agree upon a shared key, which is the symmetric key. The message is encrypted with the secret key and can only be decrypted with the same key.
So before sharing the sensitive information, Anna encrypts the message with the shared key and then sends it to Elsa. For Elsa to read the message she will be decrypted with the agreed-upon shared key. This ensures the confidentiality of the message but we cannot guarantee nonrepudiation since there is no proof to verify the authenticity of the sender.
Various symmetric encryption algorithms are employed for securing electronic data, and notable examples include.
AES (Advanced Encryption Standard), DES (Data Encryption Standard), IDEA (International Data Encryption Algorithm), Blowfish (a viable replacement for DES or IDEA), RC4 (Rivest Cipher 4), RC5 (Rivest Cipher 5), and RC6 (Rivest Cipher 6). These algorithms use a shared secret key to both encrypt and decrypt information, ensuring the confidentiality of the data. Each algorithm has its unique approach to scrambling and unscrambling the information, contributing to the diversity of options available for secure communication and data protection.
What Is Asymmetric Encryption?
Asymmetric encryption, also known as public-key cryptography, is a way of keeping messages safe using two keys: a public key that can be shared with everyone, and a private key that’s kept secret. When someone wants to send a secure message, they use the recipient’s public key to lock it up. The recipient, with their private key, can then unlock and read the message. This method allows for safe communication without needing both parties to share the same secret key, which is a big advantage over symmetric encryption.
Asymmetric encryption has extra perks. It gets rid of the hassle of sharing secret keys, which can be tricky, especially when talking to lots of people. It also lets us make digital signatures, like a virtual seal, to check if data is genuine. Asymmetric encryption is used in many areas, like keeping online chats safe, creating digital signatures, and making sure data is transferred securely.
Now that we have said a mouthful let’s break down how exactly asymmetric encryption works. Let us take the example where Anna wants to share some information with Elsa using asymmetric cryptography.
We already mentioned in asymmetric cryptography each user will have a public and private key pair where the private key will be kept as a secret and the public key will be available to everyone who wants to communicate to the user. In the below example, we can see Anna has access to 3 keys, which are her own public-private key pair and the public key of Elsa.
So in order to send a secret message to Elsa, Anna (sender) will encrypt the message with the public key of Elsa (receiver public key) and send it upon receiving the message Elsa will decrypt the message using her private key that is Elsa’s private key (receivers private key).
Let us take one more scenario where Elsa has to share private information with Anna, here Elsa has access to the public key of Anna since it is publicly available so Elsa will encrypt the message with annas public key unshared with Anna which will be decrypted using Anna’s private key.
Some examples of asymmetric encryption include RSA, ElGamal encryption, elliptical curve encryption etc.
What Is the Difference Between Symmetric and Asymmetric Encryption?
Key: in symmetric encryption same key is used for encryption and decryption but in asymmetric encryption, a public-private key pair is used
nonrepudiation: symmetric encryption does not provide non-repudiation while asymmetric encryption can.
Scalability: symmetric encryption is less scalable compared to asymmetric encryption.
Speed: symmetric key encryption is very fast but asymmetric encryption is complex and slower
Security: in symmetric key encryption the key has to be shared with all the participants which decreases the security whereas the public key is shared only with the message senders which is more secure.
Resource utilization: symmetric key encryption uses less resources compared to asymmetric key encryption hence the performance of symmetric key encryption is higher.
Data size: symmetric key encryption can be used to transmit huge amounts of data while asymmetric key encryption can be used for lesser amount of data.
Conclusion
Cryptography is an essential component of our daily digital interactions, playing a vital role in securing sensitive information and ensuring privacy. One prominent application is in secure communication channels, where cryptographic protocols like HTTPS safeguard online interactions, such as emails and video calls, by encrypting the exchanged data. Online banking relies on cryptography to protect financial transactions, preventing unauthorized access and fraud. Similarly, e-commerce transactions are secured through encryption, shielding credit card details and personal information during online purchases.
Beyond personal transactions, cryptography is integral to advanced technologies. Blockchain, the underlying technology for cryptocurrencies like Bitcoin, employs cryptographic algorithms to ensure the security and integrity of transactions in a decentralized environment. Digital signatures, another cryptographic application, authenticate digital documents, proving crucial in legal agreements, software distribution, and official communications. From military and government communication to the secure storage of data on personal devices, cryptography plays a multifaceted role in maintaining the confidentiality and integrity of information across diverse domains.
I hope this article helped in understanding the goals of cryptography, what is symmetric and asymmetric cryptography, And the difference between symmetric and asymmetric encryption. Please share this post if you find this interested. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive updates like this.
You may also like these articles:
Aroma Rose Reji
Aroma is a cybersecurity professional with more than four years of experience in the industry. She has a strong background in detecting and defending cyber-attacks and possesses multiple global certifications like eCTHPv2, CEH, and CTIA. She is a pet lover and, in her free time, enjoys spending time with her cat, cooking, and traveling. You can connect with her on LinkedIn.