Table of Contents
8 Most Powerful SIEM Solutions That Organizations Should Consider
As enterprises strive to become more digital, they face an ever-growing number of cybersecurity threats. To combat these threats, organizations are turning to security information and event management (SIEM) solutions. In this blog post, we will discuss some of the most powerful SIEM solutions that organizations should consider when selecstandaloneting a SIEM solution.
Disclaimer: The list presented here is not based on any rank criteria. Listed as First could not be the best or listed as Last in the list is not the worst by any means. This is not a complete product review. Please don’t go with the order of the tools. We clarify that the order doesn’t carry any rank. We are not here to judge the rank of the tools. We created this post to share the best options available in the market. Let’s get started.
About SIEM:
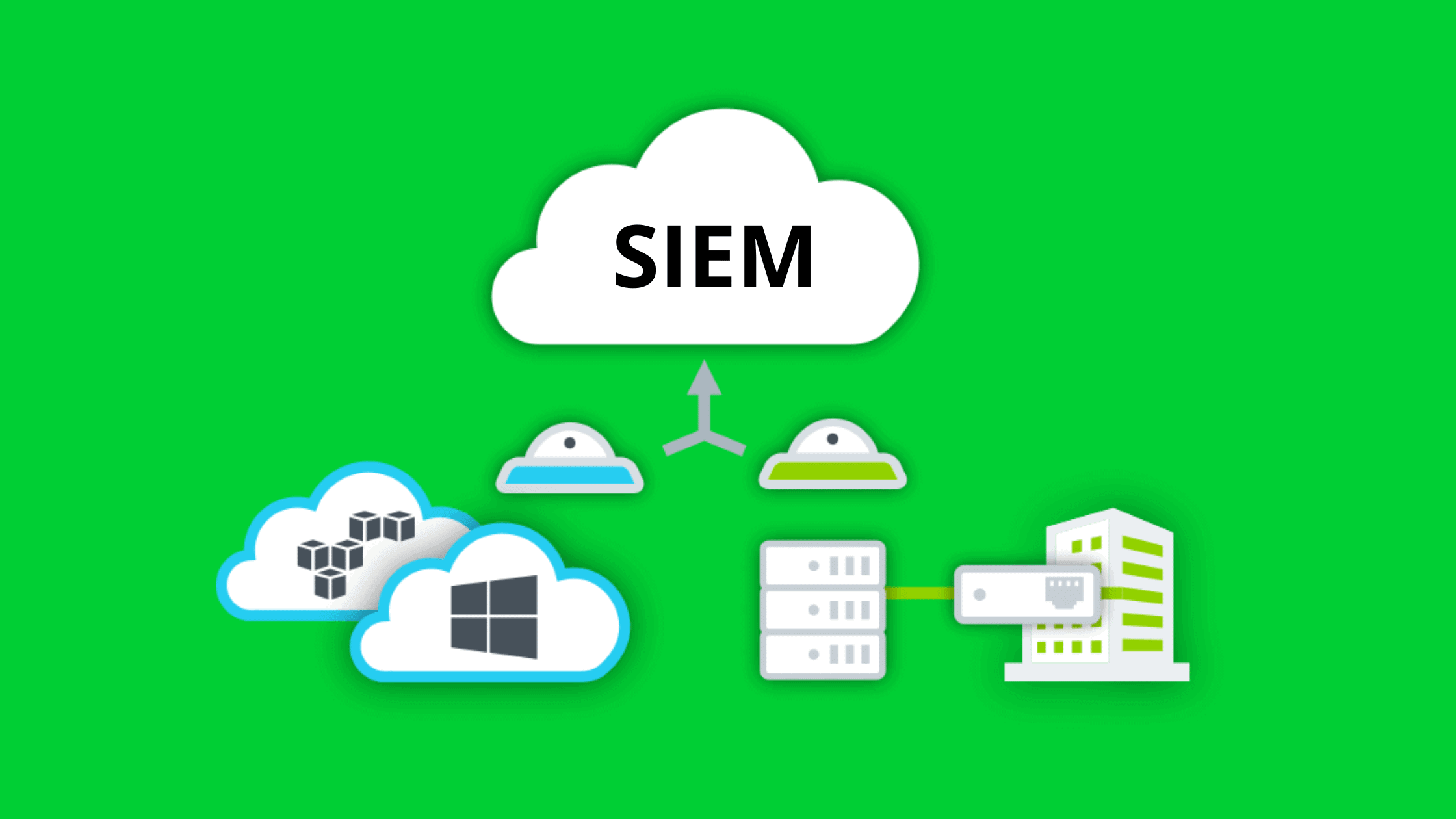
SIEM solutions are designed to provide visibility into an organization’s entire IT environment in order to help identify security threats. SIEM solutions typically collect data from a variety of sources, including network devices, applications, endpoints, and user activity. This data is then analyzed in real-time to detect suspicious activity that could indicate a security threat. SIEM solutions can also be used to comply with various regulatory requirements, such as the Sarbanes-Oxley Act (SOX) and the Payment Card Industry Data Security Standard (PCI DSS).
SIEM solutions can be deployed as a standalone software solution or as a cloud-based service. Standalone SIEM solutions are typically installed on-premises and require organizations to have their own hardware, storage, and networking infrastructure. Cloud-based SIEM solutions are delivered as a service and are typically less expensive to deploy and manage than standalone SIEM solutions.
List of the Most Powerful SIEM Solutions:
There is no one-size-fits-all solution when it comes to SIEM, as the needs of each organization differ. However, there are a few vendors that stand out from the rest in terms of features and capabilities. Here are 8 of the most powerful SIEM solutions on the market today:
Note: This is neither a comparation nor a review of products. The main purpose of writing this post is only to introduce you the best options available in the market. Each product is better then other in its own way.
#1. AlienVault USM Anywhere
Comprehensive Security in the Cloud
If you’re looking for a comprehensive security solution that can be deployed in the cloud, AlienVault USM Anywhere is the answer. This all-in-one platform provides you with everything you need to secure your hybrid IT environments, including asset discovery, intrusion detection, vulnerability management, and incident response.
With AlienVault USM Anywhere, you can get started quickly and be up and running in no time. The platform is easy to use and comes with a wide range of features that will help you keep your hybrid IT environment secure.
Some of the key features of AlienVault USM Anywhere include:
Asset Discovery – Identify all assets in your environment, both on-premises and in the cloud.
Intrusion Detection – detect and respond to threats in real time with comprehensive detection capabilities.
Vulnerability Management – Stay on top of vulnerabilities and reduce your exposure to risk.
Incident Response – quickly and efficiently respond to incidents with pre-built workflows.
AlienVault USM Anywhere is the perfect security solution for businesses of all sizes that are looking to secure their hybrid IT environments. Contact support today to find out more or get started with a free trial.
#2. Splunk Enterprise Security
Analyze and visualize security data to improve your organization’s security posture.
The Splunk Enterprise Security (ES) app analyzes data from a variety of data sources to give you visibility into your organization’s security posture. The app uses the Splunk Machine Learning Toolkit to detect anomalies and build models that identify suspicious behavior. With the ES app, you can investigate incidents, monitor for threats, and respond quickly to emerging threats.
The ES app is built on the powerful Splunk platform, which gives you the flexibility to collect data from any source and analyze it in any way you want. The Splunk platform also provides robust search and visualization capabilities, so you can quickly find the information you need.
To get started with the ES app, download it from Splunkbase.
The ES app is just one of many apps that are available for the Splunk platform. To see a complete list of apps, visit Splunkbase.
If you have any questions about the ES app or Splunk platform, please contact . Thanks for using Splunk!
#3. IBM QRadar SIEM
The Future of Security.
The IBM QRadar SIEM is the next generation of security intelligence and event management. It provides real-time visibility into your network to help you identify and respond to threats faster. The QRadar SIEM also includes a powerful analytics engine that can detect both known and unknown threats. With the QRadar SIEM, you can be confident that your organization is better protected against today’s sophisticated cyber attacks.
QRadar SIEM is designed to give you the visibility and insights you need to defend against today’s complex threats. It collects data from across your entire IT infrastructure in real-time, including network traffic, user activity, applications, and more. This data is then analyzed by the QRadar SIEM’s powerful analytics engine to detect known and unknown threats. The QRadar SIEM also includes a built-in rules engine that can automatically take action to block or contain threats, helping you to respond faster and minimize the impact of attacks.
The QRadar SIEM is part of IBM Security’s portfolio of security intelligence and event management solutions. It is available as a standalone product or as part of the IBM Security Intelligence platform.
If you are looking for a comprehensive security solution that can help you defend against today’s sophisticated cyber attacks, then the IBM QRadar SIEM is the right choice for you.
Unique Key Features of IBM QRadar SIEM:
Real-time visibility into your network.
Analytics engine to detect known and unknown threats.
Built-in rules engine to take action against threats.
Available as a standalone product or as part of the IBM Security Intelligence platform.
For more information about the QRadar SIEM, please visit: https://www.ibm
#4. ELK Stack
When it comes to open-source SIEM solutions, ELK Stack is the most powerful SIEM solution.
In this comprehensive guide, we will discuss the ELK stack, which is a popular open-source data analysis platform. We’ll cover its history, how it works, and why it’s become so popular in recent years. We’ll also provide a detailed guide on how to set up your own ELK stack and use it to analyze data. By the end of this guide, you should have a good understanding of what the ELK stack is and how it can be used to benefit your organization. Let’s get started!
The ELK stack is a software bundle that includes Elasticsearch, Logstash, and Kibana. These three products are designed to work together to provide a powerful data analysis platform. Elasticsearch is a search engine and data store, Logstash is a data processing pipeline, and Kibana is a visualization tool. Together, these tools can be used to collect, process, and visualize data from a variety of sources.
The ELK stack was created by Elastic, a company that specializes in open-source data analysis tools. The stack is based on the popular Apache Lucene project, which provides the core search engine capabilities for Elasticsearch. Elasticsearch was originally released in 2010, followed by Logstash in 2012 and Kibana in 2013.
Elasticsearch – Elasticsearch is the heart of the ELK stack. It is a powerful search engine that can be used to index and query data from a variety of sources. Elasticsearch is designed to be scalable and easy to use. It has a simple REST API that makes it easy to integrate with other applications. Elasticsearch can be used as a standalone search engine or as part of a larger data analysis platform.
Logstash – Logstash is a data processing pipeline that can be used to collect, parse, and filter data from a variety of sources. Logstash can be used to process log files, system metrics, application monitoring data, and just about any other type of data. Logstash is highly configurable and can be used to build complex data processing pipelines.
Kibana – Kibana is a visualization tool that can be used to create beautiful dashboards and visualizations of your data. Kibana is easy to use and provides a variety of built-in visualization types. Kibana can be used to explore and visualize data from Elasticsearch, Logstash, and other data sources.
The ELK stack is a popular choice for data analysis because it is open-source, scalable, and easy to use. The stack has a large community of users and developers who contribute new features and enhancements. The ELK stack is constantly evolving and adding new features. If you’re looking for a data analysis platform that is both powerful and flexible, the ELK stack is a great option.
#5. ArcSight ESM
ArcSight ESM is another most powerful SIEM solution being used at the global level.
ArcSight SIEM is a powerful SIEM solution (security information and event management) that enables organizations to detect, investigate and respond to cyber threats in real time. ArcSight SIEM provides comprehensive visibility into all activity across the enterprise, from the network to the endpoint, so you can quickly identify and respond to threats before they cause damage.
ArcSight SIEM also offers robust analytics and reporting capabilities, so you can gain insights into trends and patterns in your environment, as well as create custom reports to support your specific needs. And with its built-in incident response workflow, you can streamline and automate your response process to ensure timely and effective action.
Key Features of ArcSight SIEM:
Comprehensive visibility: ArcSight SIEM provides comprehensive visibility into all activity across the enterprise, from the network to the endpoint. This enables you to quickly identify and respond to threats before they cause damage.
Robust analytics and reporting: ArcSight SIEM offers robust analytics and reporting capabilities. This allows you to gain insights into trends and patterns in your environment, as well as create custom reports to support your specific needs.
Built-in incident response workflow: ArcSight SIEM comes with a built-in incident response workflow. This streamlines and automates your response process to ensure timely and effective action.
Flexible deployment options: ArcSight SIEM can be deployed on-premises or in the cloud. This gives you the flexibility to choose the deployment option that best suits your needs.
Scalable and extensible: ArcSight SIEM is a scalable and extensible solution. This means it can grow with your organization as your needs change.
To learn more about ArcSight SIEM, please visit: https://www.microfocus.com/en-us/cyberres/secops/arcsight-esm
#6. LogRhythm NextGen SIEM Platform
Complete visibility and control over your entire IT environment.
The LogRhythm NextGen SIEM Platform provides complete visibility and control over your entire IT environment. It consolidates security information and event management (SIEM), log management, network forensics, and endpoint monitoring into a single, synchronized platform that enables you to quickly detect and respond to threats. The LogRhythm platform is designed to be scalable, flexible, and extensible, so it can grow with your organization as your needs change.
LogRhythm’s comprehensive capabilities give you the power to:
Monitor all activity across your entire IT infrastructure in real-time.
Correlate events from multiple data sources to identify relationships and trends.
Generate actionable intelligence with LogRhythm’s built-in analytics.
Respond quickly and effectively to threats with LogRhythm’s integrated incident response tools.
The LogRhythm NextGen SIEM Platform is a critical part of any organization’s security posture, providing the visibility and insights you need to detect and respond to today’s sophisticated threats. All these made LogRhythm NextGen SIEM Platform a powerful SIEM solution to secure IT infrastructure. Contact support today to learn more about this powerful platform can help you secure your organization.
#7. McAfee Enterprise Security Manager (ESM) or Trellix XDR
Comprehensive Security Management.
McAfee Enterprise Security Manager (ESM) is a comprehensive security management platform that enables enterprises to centrally manage and deploy McAfee security products and technologies. ESM consolidates security information from across the enterprise into a single console, providing enterprises with greater visibility into their overall security posture. Additionally, ESM automates many of the repetitive and time-consuming tasks associated with managing security, such as deploying security updates and monitoring compliance with corporate security policies.
ESM provides enterprises with a number of benefits, including:
Centralized management of security products and technologies.
Greater visibility into the enterprise’s overall security posture.
Automation of repetitive and time-consuming tasks associated with managing security.
Enhanced compliance with corporate security policies.
To know more about this powerful SIEM solution, please visit: https://www.mcafee.com/enterprise/en-us/products/enterprise-security-manager/support.html
Note: McAffe is now Trellix.
#8. SolarWinds SIEM
A security solution from SolarWinds.
SolarWinds SIEM delivers a centralized approach to security information and event management (SIEM). It consolidates data from multiple security sources, correlates it for anomalies, and provides real-time visibility into attacks. SolarWinds SIEM also includes an integrated incident response system to help you quickly address threats.
SolarWinds SIEM is designed to be highly scalable, so it can grow with your organization as your security needs evolve. It can collect and correlate data from up to 500 devices and 10,000 users out-of-the-box and can be easily expanded to support even larger deployments.
SolarWinds SIEM is a comprehensive solution that includes everything you need to get started, including:
A central management console for easy administration.
Flexible deployment options (virtual, physical, or in the cloud).
Automatic updates to keep your system up-to-date.
Comprehensive documentation and 24/7 support.
For more information, visit: https://www.solarwinds.com/security-event-manager.
For purchase, visit: https://www.solarwinds.com/company/contact-us
Organizations need to carefully consider their specific needs when choosing a SIEM solution. However, the eight vendors listed above offer some of the most powerful and comprehensive SIEM solutions on the market today.
We hope this post would help you know some of the most powerful SIEM solutions that organizations should consider when selecting a SIEM solution. Thanks for reading this post. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.