Table of Contents
How Do (ALPACA ) TLS Cross-Protocol Attacks Lets Attackers Redirect HTTPS Traffic
A group of researchers from Ruhr University has disclosed a new type of TLS Cross-Protocol Attacks that exploits misconfigurations in transport layer security (TLS) service to redirect application layer protocol traffic from a victim’s web browser to another TLS service located on a different IP address to steal sensitive information. The attack is coined as
attack “Application Layer Protocol Confusion — Analyzing and mitigating Cracks in TLS Authentication”. Let’s see how this attack works in theory.
What Is TLS?
TLS — Transport Layer Security is a protocol standard that provides secure communication between clients and servers over the internet. A very good example is HTTPS communication. Most of you know that HTTP is an application layer plane text protocol used to transfer HTML files from web servers to web browsers. After adding the TLS authentication layer to HTTP, it becomes HTTPS which is secured.
TLS adds an additional layer of authentication to several application layers of protocols like HTTPS, SMTP, IMAP, POP3, and FTP to secure communications over the network. The ultimate goal of the TLS protocol is not just encryption, it is designed to provide Integrity, Confidentiality, Availability, and nonrepudiation to the communication between the source and the destination. We recommend reading this post if you want to know more information about SSL/TLS.
What Is (ALPACA ) TLS Cross-Protocol Attacks?
Research says, “ALPACA is an application layer protocol content confusion attack, exploiting TLS servers implementing different protocols but using compatible certificates, such as multi-domain or wildcard certificates. Attackers can redirect traffic from one subdomain to another, resulting in a valid TLS session. This breaks the authentication of TLS, and cross-protocol attacks may be possible where the behavior of one protocol service may compromise the other at the application layer.“
TLS is designed to function independently with the TCP connection of the application layer protocol. In other words, TLS does not bind a TCP connection to the intended application layer protocol. This has created a gap that makes the (ALPACA ) TLS Cross-Protocol Attack pragmatic. Attackers could leverage this flaw to redirect TLS traffic to the substitute TLS service located on another IP address of the subdomain covered under the same wildcard or multi-domain PKI certificate.
How Do Attackers Redirect HTTPS Traffic Using (ALPACA ) TLS Cross-Protocol Attacks?
Let’s assume a client and two servers: 1. Intended server running HTTP services, 2. Substitute server running FTP services. The same wildcard or multi-domain certificates should be deployed on both servers. At first, the Client will request an HTTPS request to the intended server over port 80 and wait for the response. At that movement, the attacker will capture the TLS session ID, then create a custom payload using that session ID. The attacker uses the custom payload to redirect the TCP connection from intended server:80 to substitute server:21 using the same TLS session ID.
Vectors of TLS Cross-Protocol Attacks:
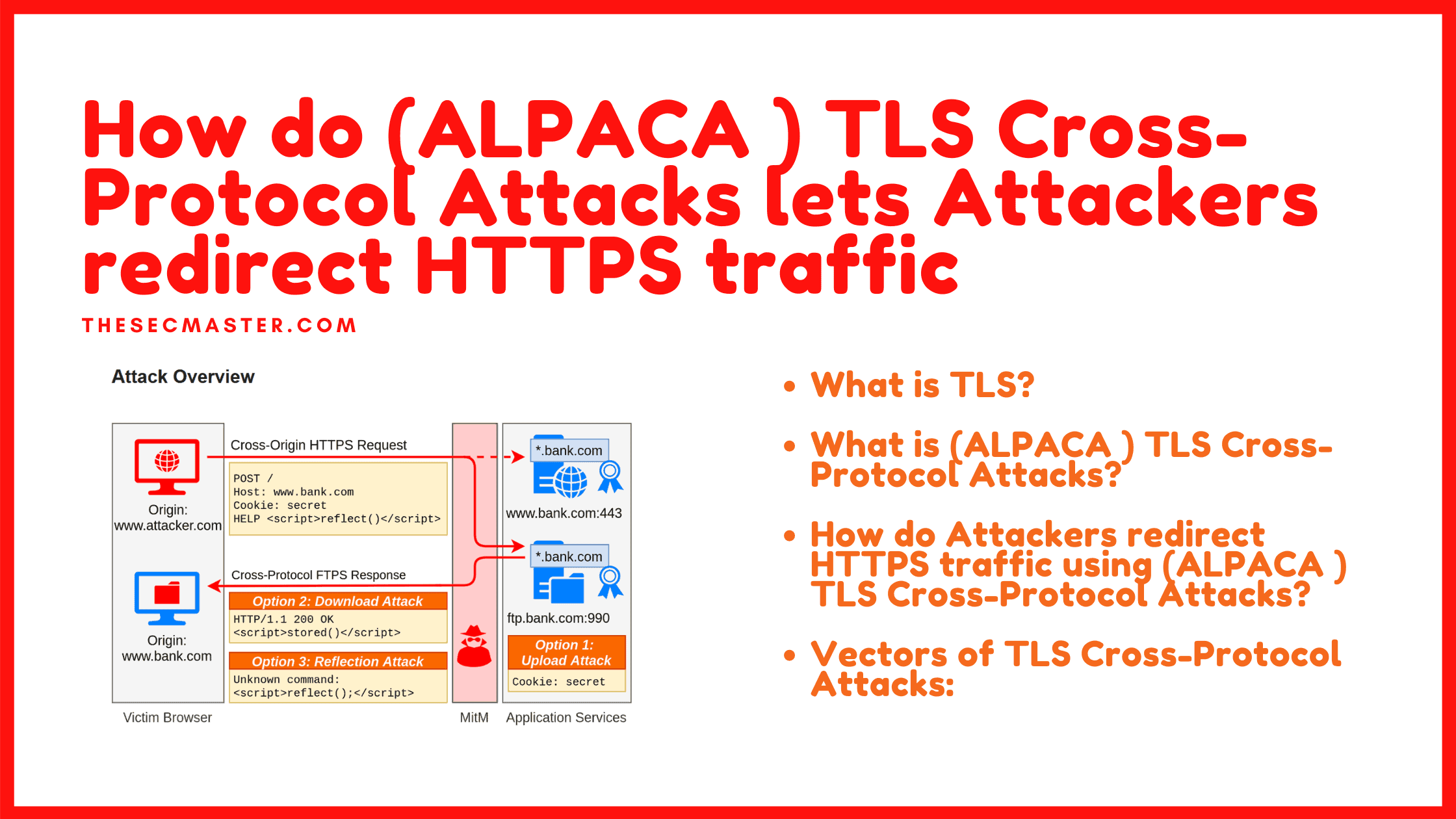
Fig #1: (ALPACA ) TLS Cross-Protocol Attacks
Researchers have presented three vectors of attacks. An attacker can leverage TLS protection to use cross-protocol attacks against webservers, vulnerable FTP, and Email servers.
#1 Option 1: Upload Attack
In the Upload Attack, the attacker exfiltrates the authentication cookies or other private data.
#2 Option 2: Download Attack
In the Download Attack, the attacker launches a stored XSS attack in the context of the victim’s website.
#3 Option 3: Reflection Attack
In the Reflection Attack, the attacker launches a reflected XSS attack in the context of the victim’s website.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.