Table of Contents
How Does Splunk Manages the Multiple Copies of Configuration Files?
Hey there, Splunk enthusiast! If you're reading this, chances are you've already discovered the importance of configuration files in your Splunk journey. As you dive deeper into the world of Splunk, you'll quickly realize that it's no different from any other application when it comes to relying on configuration files. But here's where things get interesting - Splunk takes a unique approach by maintaining multiple copies of the same configuration files across different locations.
Now, I know what you might be thinking: "Why would Splunk do that? Isn't it confusing?" Trust me, you're not alone in your concerns. Many administrators and architects scratch their heads when they first encounter this concept. But fear not, my friend! Understanding how Splunk manages these multiple copies of configuration files is crucial to unlocking the true potential of your Splunk environment.
In this blog post, we'll be your trusty guides as we explore the fascinating realm of Splunk configuration files. We'll answer all the burning questions you might have, such as which files take precedence, how Splunk prioritizes them, and how the context affects the precedence. By the end of this post, you'll be armed with the knowledge to confidently navigate and optimize your Splunk configuration files like a true pro. So, grab a cup of coffee, get comfortable, and let's embark on this exciting journey together!
Directory Structure in Splunk
Before jaunting into the actual potato, let's explore a bit about the directory structure in Splunk. When you install Splunk, you'll find several important directories that store various components, including configuration files. Here's a breakdown of the key directories you should be familiar with:
1. $SPLUNK_HOME/etc/system: This directory contains system-wide configuration files that apply to all apps and users. It has two subdirectories:
- default: Houses the default configuration files provided by Splunk. These files serve as a fallback for settings not explicitly defined elsewhere.
- local: Used to store custom configuration files that override the default settings. Files placed here take precedence over the default files.
2. $SPLUNK_HOME/etc/apps: This directory is where you'll find all your Splunk apps. Each app has its own subdirectory, and within each app directory, you'll find:
- default: Contains the default configuration files specific to that app.
- local: Used to store custom configuration files that override the app's default settings.
3. $SPLUNK_HOME/etc/users: This directory is used to store user-specific configuration files. Each user has their own subdirectory, and within each user directory, you'll find:
- default: Contains the default configuration files specific to that user.
- local: Used to store custom configuration files that override the user's default settings.
You will see the same copies of configuration files in all these locations. For example, you will see inputs.conf, outputs.conf, and server.conf on $SPLUNK_HOME/etc/system, $SPLUNK_HOME/etc/apps, $SPLUNK_HOME/etc/users, and even other locations too.
Why Does Splunk Has Multiple Copies of Configuration Files?
Now, you might be wondering, "Why does Splunk has multiple copies of the same configuration files?" Great question! The answer lies in Splunk's flexibility and its ability to cater to different contexts and requirements.
Imagine you have multiple Splunk apps installed, each with its own set of configuration files. Splunk maintains separate copies of these files for each app, allowing you to have app-specific configurations. This way, you can tailor the behavior of each app without affecting the others.
But that's not all! Splunk takes it a step further by providing a layered approach to configuration files. You'll find default configuration files in the $SPLUNK_HOME/etc/system/default directory, which serve as a fallback for any settings not explicitly defined elsewhere. However, you can override these default settings by creating copies of the configuration files in the $SPLUNK_HOME/etc/system/local directory or within specific app directories.
This layered approach allows you to have granular control over your Splunk environment. You can define global settings that apply to all apps and users in the $SPLUNK_HOME/etc/system directory, while still having the flexibility to override these settings at the app or user level.
Understanding the Context in Splunk
Now that you have a good understanding of Splunk's directory structure and why it maintains multiple copies of configuration files, let's dive into the crucial question: how does Splunk determine which configuration file to use when there are multiple copies present?
Splunk follows a specific order of precedence when deciding which configuration file to use. Before we go to precedence rule, it's mandatory to understand the context in Splunk.
Splunk operates in two main contexts: the global context and the app/user context. Let's explore each of these contexts in more detail.
Global Context
The global context refers to activities and configurations that are independent of any specific app or user. These are system-wide settings that affect the overall functioning of Splunk. Examples of activities that take place in the global context include:
Indexing
Input data collection
Parsing
Licensing
Configuration files that operate in the global context are typically located in the $SPLUNK_HOME/etc/system directory and its subdirectories. These files are used to configure system-wide settings, such as data inputs, indexes, and licensing.
Some common configuration files that operate in the global context include:
inputs.conf: Configures data inputs and their settings.indexes.conf: Defines indexes and their properties.server.conf: Contains general Splunk server configuration settings.outputs.conf: Configures data forwarding and other output settings.
App/User Context
The app/user context, on the other hand, refers to activities and configurations that are specific to a particular app or user. These settings are relevant to search-time processing and are used to customize the behavior and appearance of Splunk for specific apps or users.
Examples of activities that take place in the app/user context include:
Searching
Reporting
Dashboarding
Alerting
Configuration files that operate in the app/user context are typically located in the $SPLUNK_HOME/etc/apps/<app-name> and $SPLUNK_HOME/etc/users/<username> directories and their subdirectories. These files are used to configure app-specific or user-specific settings, such as saved searches, dashboards, and field extractions.
Some common configuration files that operate in the app/user context include:
savedsearches.conf: Defines saved searches and their properties.props.conf: Configures data transformations and field extractions.transforms.conf: Defines search-time transformations.macros.conf: Contains search macros.
It's important to note that some configuration files, such as props.conf and transforms.conf, can operate in both the global and app/user context, depending on their location and the specific settings they contain.
How Does Splunk Determine Which Configuration File to Use?
Now that you have a solid understanding of the global and app/user contexts in Splunk, let's explore how Splunk determines which configuration file to use when there are multiple copies present.
Splunk follows a specific order of precedence when deciding which configuration file to use. This precedence rule ensures that the most relevant and specific configuration settings are applied, allowing you to customize and override settings at different levels.
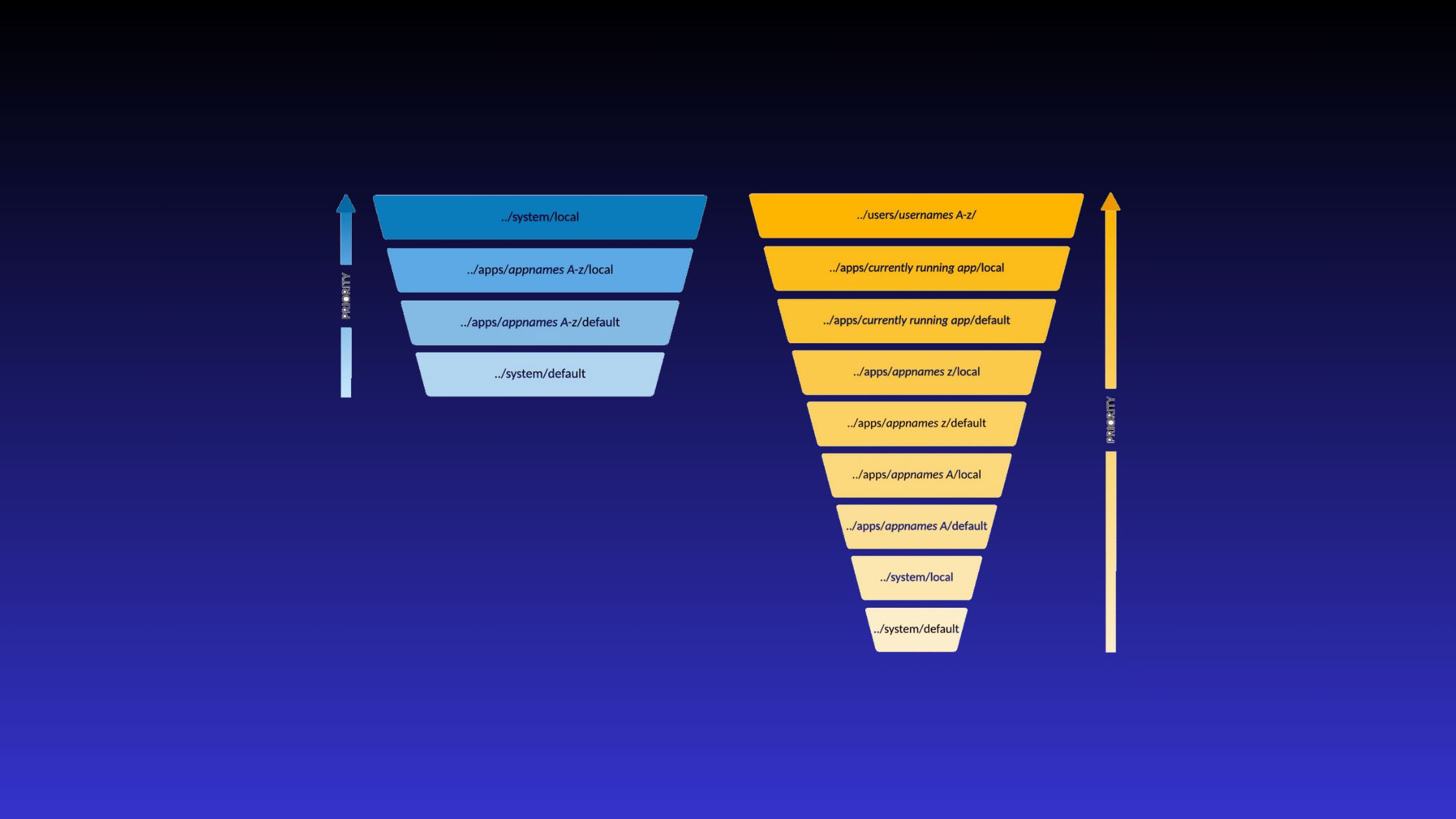
Precedence Order in the Global Context
In the global context, Splunk evaluates configuration files in the following order of precedence:
1. $SPLUNK_HOME/etc/system/local: This directory has the highest precedence in the global context. Configuration files placed here will override any settings defined in the default or app-specific directories.
2. $SPLUNK_HOME/etc/apps/<app-name>/local: Splunk looks for configuration files in the local directory of each installed app. Settings defined here will override the default settings for that specific app.
3. $SPLUNK_HOME/etc/apps/<app-name>/default: If no configuration files are found in the app's local directory, Splunk falls back to the default directory of each installed app. These files provide the default settings for the app.
4. $SPLUNK_HOME/etc/system/default: If no configuration files are found in any of the above locations, Splunk uses the files in the system/default directory. These files contain the system-wide default settings.
Precedence Order in the App/User Context
In the app/user context, Splunk evaluates configuration files in the following order of precedence:
1. $SPLUNK_HOME/etc/users/<username>/<app-name>/local: This directory has the highest precedence in the app/user context. Configuration files placed here will override any settings defined in the app or system directories for that specific user and app.
2. $SPLUNK_HOME/etc/apps/<app-name>/local: If no user-specific configuration files are found, Splunk looks for files in the local directory of the specified app. Settings defined here will override the default app settings.
3. $SPLUNK_HOME/etc/apps/<app-name>/default: If no configuration files are found in the app's local directory, Splunk falls back to the default directory of the specified app. These files provide the default settings for the app.
4. $SPLUNK_HOME/etc/system/local: If no app-specific configuration files are found, Splunk looks for files in the system/local directory. Settings defined here will override the system-wide default settings.
5. $SPLUNK_HOME/etc/system/default: If no configuration files are found in any of the above locations, Splunk uses the files in the system/default directory as a final fallback.
Precedence Order in Distributed Cluster Environment
In a distributed Splunk environment, such as an indexer cluster or search head cluster, Splunk has a different set of rules to determine the precedence of configuration files, ensuring consistent settings across all nodes.
For indexer cluster peers, Splunk looks for configuration files in the following order:
slave-apps/<app-name>/localsystem/localapps/<app-name>/localslave-apps/<app-name>/defaultapps/<app-name>/defaultsystem/default
This precedence order ensures that files in the slave-apps directory take priority over those in the regular apps directory.
In search head clusters, Splunk follows a similar precedence order:
shcluster/apps/<app-name>/localapps/<app-name>/localshcluster/apps/<app-name>/defaultapps/<app-name>/defaultsystem/localsystem/default
Files in the shcluster directory have the highest precedence, allowing for consistent configuration across search head cluster members.
What Happens In Case of Conflict?
When there is a multiple copies of configuration files, there could be same attributes present in the configuration files. In such cases, it's essential to understand how Splunk handles conflicts between settings. Conflicts can arise when different copies of the same configuration file have conflicting attribute values. In such cases, Splunk follows a specific merging process to determine which values should take precedence.
When Splunk encounters multiple copies of a configuration file, it merges the settings from all the copies based on the precedence order. The merging process follows these rules:
Splunk starts by loading the configuration file with the lowest precedence, typically the one in the
`$SPLUNK_HOME/etc/system/default`directory.It then moves up the precedence order, loading configuration files from the
`apps`and`system`directories, as well as any relevant`slave-apps`or`shcluster`directories in a distributed environment.As Splunk encounters each configuration file, it merges the settings with the previously loaded settings. If a setting is not present in a higher-precedence file, the value from the lower-precedence file is retained.
If a higher-precedence file contains a setting that conflicts with a lower-precedence file, the value from the higher-precedence file overwrites the value from the lower-precedence file.
Splunk continues this merging process until it has processed all relevant configuration files in the precedence order.
By following this merging process, Splunk ensures that the final configuration is a combination of settings from all the configuration files, with higher-precedence files taking priority over lower-precedence files.
Handling Attribute Conflict
When different copies of a configuration file have conflicting attribute values, Splunk resolves the conflict by using the value from the file with the highest precedence. This means that if a higher-precedence file sets an attribute to a different value than a lower-precedence file, the value from the higher-precedence file will be used. For example, let's say you have an `inputs.conf` file in both the `$SPLUNK_HOME/etc/system/local` directory and the `$SPLUNK_HOME/etc/apps/my_app/default` directory. If the `system/local` file contains an attribute like this:
[monitor:///var/log/]
disabled = falseAnd the `apps/my_app/default` file contains the same attribute with a different value:
[monitor:///var/log/]
disabled = trueIn this case, Splunk will use the value `disabled = false` from the `system/local` file because it has a higher precedence than the `apps/my_app/default` file.
It's important to note that Splunk merges configuration files at a stanza level. If a higher-precedence file contains a stanza that is not present in a lower-precedence file, the entire stanza from the higher-precedence file is used. If a lower-precedence file contains a stanza that is not present in a higher-precedence file, that stanza is retained in the final configuration.
Example:
In this example, we have three copies of the inputs.conf file in different directories:
1. $SPLUNK_HOME/etc/system/default/inputs.conf:
- Contains the [monitor:///var/log/] stanza with disabled = true and index = main.
2. $SPLUNK_HOME/etc/apps/my_app/local/inputs.conf:
- Contains the [monitor:///var/log/] stanza with disabled = false and sourcetype = my_type.
3. $SPLUNK_HOME/etc/system/local/inputs.conf:
- Contains the [monitor:///var/log/] stanza with disabled = true and index = custom.
When Splunk merges these configuration files, it follows the precedence order:
Splunk starts with the
system/defaultfile, which setsdisabled = trueandindex = main.It then moves to the
apps/my_app/localfile. This file setsdisabled = falseand introduces a new attributesourcetype = my_type. Thedisabledattribute value from this file overwrites the value from thesystem/defaultfile.Finally, Splunk processes the
system/localfile. This file setsdisabled = trueandindex = custom. Thedisabledattribute value from this file overwrites the value from theapps/my_app/localfile. Theindexattribute value overwrites the value from thesystem/defaultfile.
The resulting final configuration combines the attribute values based on the precedence order:
disabled = true(from thesystem/localfile)index = custom(from thesystem/localfile)sourcetype = my_type(from theapps/my_app/localfile)
We hope this article helps understanding how does Splunk manages the multiple copies of configuration Files. We are going to end this article for now, we will cover more information about the Splunk in the up coming articles. Please keep visiting thesecmaster.com for more such technical information. Visit our social media page on Facebook, Instagram, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive information like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.