Table of Contents
How I Calculated CVSS Environmental Metrics for a Vulnerability?
The Common Vulnerability Scoring System (CVSS) is an industry standard methodology for assessing the severity and risk potential of software vulnerabilities. As a security analyst, understanding how to properly calculate and apply CVSS scores is crucial for prioritizing vulnerabilities within an organization. In this blog post, I will walk through a real-world example of using CVSS Environmental Metrics to customize vulnerability risk for a specific situation.
A Recap of CVSS Basics
But before we dive into Environmental Metrics, let’s do a quick recap of CVSS basics. The CVSS risk rating formula consists of three main components:
Base Metrics – inherent characteristics of a vulnerability that do not change, such as attack vector and privileges required.
Temporal Metrics – characteristics that change over time, such as exploit code maturity and remediation level.
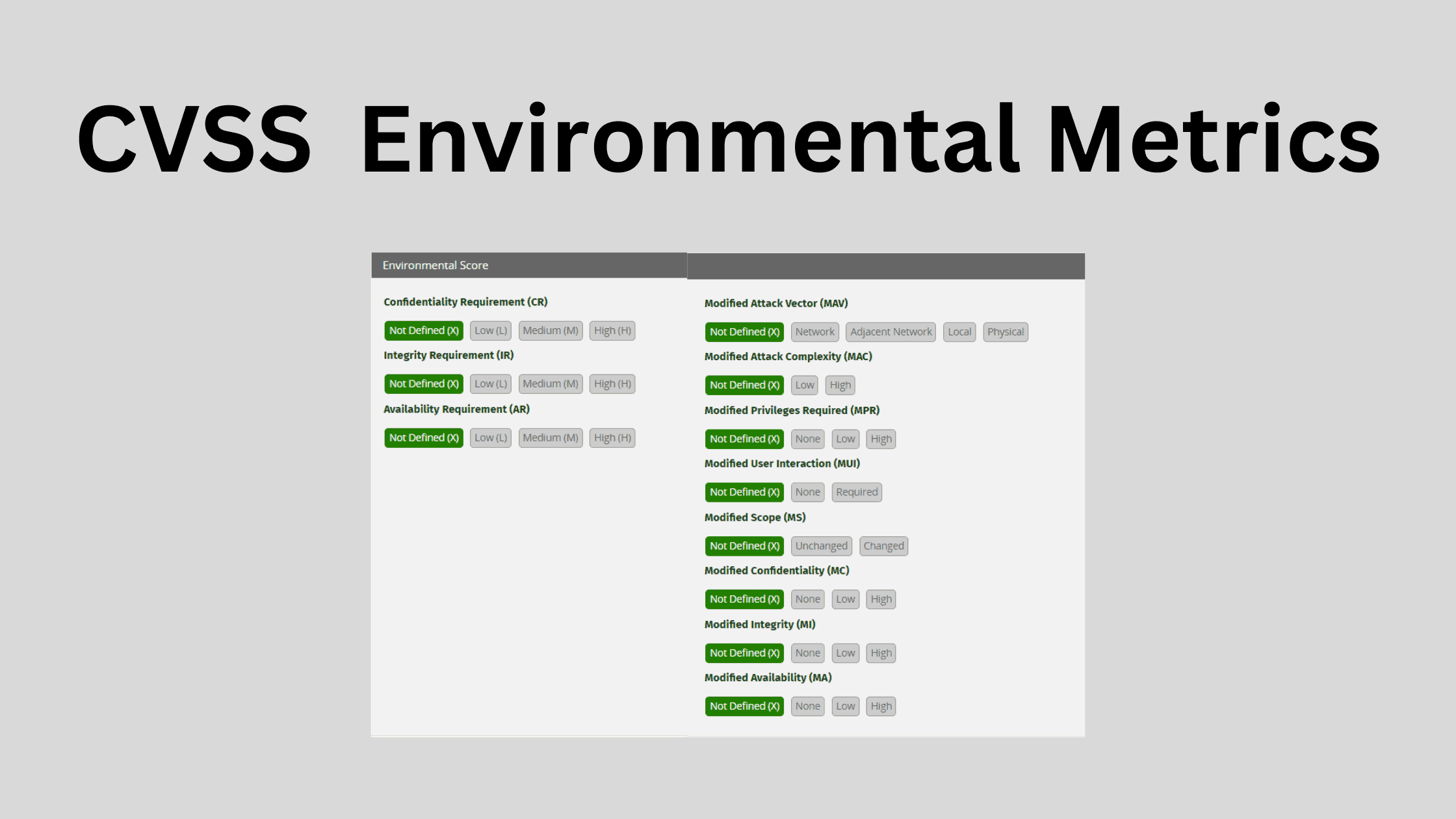
Environmental Metrics – relates to a vulnerability’s risk within your unique environment.
The overall CVSS score is calculated by combining the Base, Temporal, and Environmental Metrics into a numerical score from 0.0 to 10.0. This allows security teams to consistently measure and communicate the severity of vulnerabilities, even as factors around them change over time.
CVSS also defines qualitative severity ratings that map to different score ranges:
Critical – 9.0 to 10.0
High – 7.0 to 8.9
Medium – 4.0 to 6.9
Low – 0.1 to 3.9
So in summary, CVSS provides a standardized and flexible framework for assessing vulnerability risk through three layers of metrics.
Introducing CVSS Environmental Metrics
The Environmental Metrics component allows us to customize CVSS scores based on the importance and uniqueness of assets in our environment. Environmental Metrics provide two main ways to tailor scores:
1. Setting CIA Requirements
| Value | Abbreviation | Score | Description |
| Not Defined | X | 1 | Insufficient information to define and has no impact on score |
| High | H | 1.5 | Loss of requirement, would have catastrophic impact |
| Medium | M | 1 | Loss of requirement, would have serious impact |
| Low | L | 0.5 | Loss of requirement, would have limited impact |
We can specify confidentiality (C), integrity (I), and availability (A) requirements for a vulnerability as High, Medium, Low, or Not Defined. For example, if confidentiality of data is critical for a system, we would set a “High” value which increases the CVSS score.
2. Modifying Base Metrics
| CVSS Base Metrics | Modified Base Metrics |
|---|---|
| AV: Attack Vector | MAV: Modified Attack Vector |
| AC: Attack Complexity | MAC: Modified Attack Complexity |
| PR: Privileges Required | MPR: Modified Privileges Required |
| UI: User Interaction | MUI: Modified User Interaction |
| S: Scope | MS: Modified Scope |
| C: Confidentiality Impact | MC: Modified Confidentiality Impact |
| I: Integrity Impact | MI: Modified Integrity Impact |
| A: Availability Impact | MA: Modified Availability Impact |
Base Metrics like attack vector and privileges required can be overridden if they do not accurately represent the situation in your environment. For example, if a vulnerability requires admin access normally but users run with admin rights by default in your organization, you may want to lower the privileges required metric.
Calculating Environmental Metrics: A Real-World Example
Let’s look at an example of using Environmental Metrics at a fictional company “Company123”.
Company123 utilizes an HR application called HRApp to store employee records, salary info, etc. This application contains highly sensitive PII data and therefore confidentiality of this system is extremely important.
A recent vulnerability scan uncovered a “medium” severity vulnerability in HRApp with the following Base CVSS v3.1 score:
5.4 AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L
This indicates that the vulnerability can be exploited remotely without user interaction (good for attackers), but does require low privileges and has limited confidentiality, integrity, and availability impact.
However, when we look at the Environmental factors for this specific HRApp server, two major differences stand out:
The confidentiality requirement for this system is “High” given the sensitive HR data it stores.
Due to legacy apps running on the server, the HRApp is actually running with admin privileges instead of low privileges.
To account for these environmental factors, we can modify the CVSS score as follows:
Set Confidentiality Requirement to “High” since PII exposure on this system is unacceptable
Change Modified Privileges Required from “Low” to “High” since the app runs as admin
Recalculate score
This results in a new CVSS v3.1 score of 8.6 (up from 5.4):
Environmental Score: 8.6 AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H/CR:H/IR:H/AR:H
By factoring in the environmental specifics, we have appropriately escalated the risk rating from a “medium” to a “high” severity vulnerability. This allows us to convey the true criticality of remediating this issue within Company123’s unique environment.
Prioritizing the fix for this higher risk vulnerability will help Company123 avoid a potential data breach or disruption of this mission critical HR system.
Key Takeaways for Using Environmental Metrics
Through this real-world example, we can see the value of properly assessing Environmental Metrics when calculating CVSS scores. Here are some of my key takeaways:
Identify critical systems – Determine systems with confidentiality, integrity, or availability requirements above the norm based on regulatory, business, or data sensitivity needs.
Know your configurations – Understand how systems are actually deployed and accessed in the environment, particularly related to privileges.
Override Base scores when needed – If Base Metrics don’t capture the real-world exposure, use modified metrics.
Re-prioritize higher risk vulnerabilities – Let customized CVSS ratings guide your vulnerability remediation strategy.
Properly utilizing Environmental Scoring ensures your security program is focused on fixing vulnerabilities that pose the greatest degree of risk specifically within your organization’s infrastructure and requirements.
I hope this glimpse into a real-world CVSS Environmental Metrics scenario gives you a better idea of its value in vulnerability management programs. As always, please share any questions below!
We hope this post helped in learning about how i calculated CVSS environmental metrics for a vulnerability. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.