Table of Contents
How I Detected Vulnerabilities on Client’s Network?
As a security analyst, one of my key responsibilities is to detect vulnerabilities on my clients’ networks. This allows me to identify security flaws or misconfigurations that could be exploited by attackers. Recently, I was brought in to assess the security posture of a new client’s infrastructure.
Why Vulnerability Scanning is Critical?
Before diving into the details of how I conducted vulnerability scanning for this client, it’s important to understand why this process is so critical. At a basic level, vulnerabilities exist in every system, and there’s not always an obvious fix. Attackers are constantly probing networks for flaws that they can leverage to breach defenses. Some key reasons why vigilance around vulnerability management is essential:
Prevent Data Breaches: Vulnerabilities left unaddressed can enable attackers to access sensitive data. Identifying and remediating these security gaps is key to avoiding costly data breaches.
Meet Compliance Requirements: Many industry regulations and standards like HIPAA and PCI DSS require conducting vulnerability scans and addressing findings.
Reduce Risk: Proactively detecting and resolving vulnerabilities reduces the overall risk exposure for an organization.
Improve Security Posture: Regularly scanning for vulnerabilities provides visibility into the current security state and where improvements need to be made.
Neglecting vulnerability management can leave organizations wide open to cyber threats. Now let’s look at how I conducted vulnerability scanning for my latest client.
Choosing the Right Vulnerability Scanning Solution
There are many vulnerability scanning tools on the market, both open source and commercial. For this engagement, I selected Rapid7 InsightVM as my scanning solution. Some key reasons this was the right choice:
Comprehensive coverage: InsightVM checks for 8,000+ CVEs out of the box for a very complete view of vulnerabilities.
User-friendly interface: The dashboard provides an intuitive way to analyze, prioritize and track vulnerabilities.
Custom reporting: Flexible reporting options allow me to tailor reports to the client’s needs.
Risk scoring: InsightVM applies predictive scoring to accurately reflect vulnerability exploitability and business impact.
Integrations: Integration with tools like Slack, Jira, and metasploit allows me to push findings to my clients’ existing workflows.
With InsightVM as my scanning engine, I was equipped to thoroughly detect vulnerabilities across my client’s environment.
Planning the Vulnerability Scan
The first step was to strategically plan my vulnerability scanning approach. This involved gathering key details from the client:
Business applications: I needed visibility into their most critical apps and databases to ensure sufficient scanning coverage.
Compliance needs: Understanding their regulatory landscape allows me to scan for risks associated with standards like SOC 2 or ISO 27001.
Change management: If any major changes were planned on the network, I could schedule scanning before and after to gauge any impact.
Maintenance windows: There are best times to run scans to not disrupt productivity, so aligning with their change/release cycles is ideal.
With this context, I was able to define the optimal scanning scope, frequency, and other parameters aligning to the client’s needs.
Configuring and Executing the Vulnerability Scan
Next, I configured my InsightVM scanner appliance integrated with Nexpose, installed safely outside the client’s network perimeter. This provides the visibility needed to perform scans without directly accessing their systems. Some key aspects configured:
Asset discovery: Identified all devices through host discovery, port scanning, and other methods.
Authentication: For more comprehensive results, provided admin credentials to deeply inspect configurations.
Scan scope: Specified IP address ranges, domains, network segments, and assets groups in scope.
Scan settings: Tuned checks for specific vulnerabilities based on the client’s tech stack.
Risk factors: Configured definitions for relevance and impact to accurately calculate risk scores.
Scan schedules: Set recurring weekly scans during pre-defined maintenance windows.
With scanning fully configured, I executed the first complete baseline vulnerability scan across the client’s infrastructure. This would reveal the breadth of security gaps to be addressed as part of our engagement.
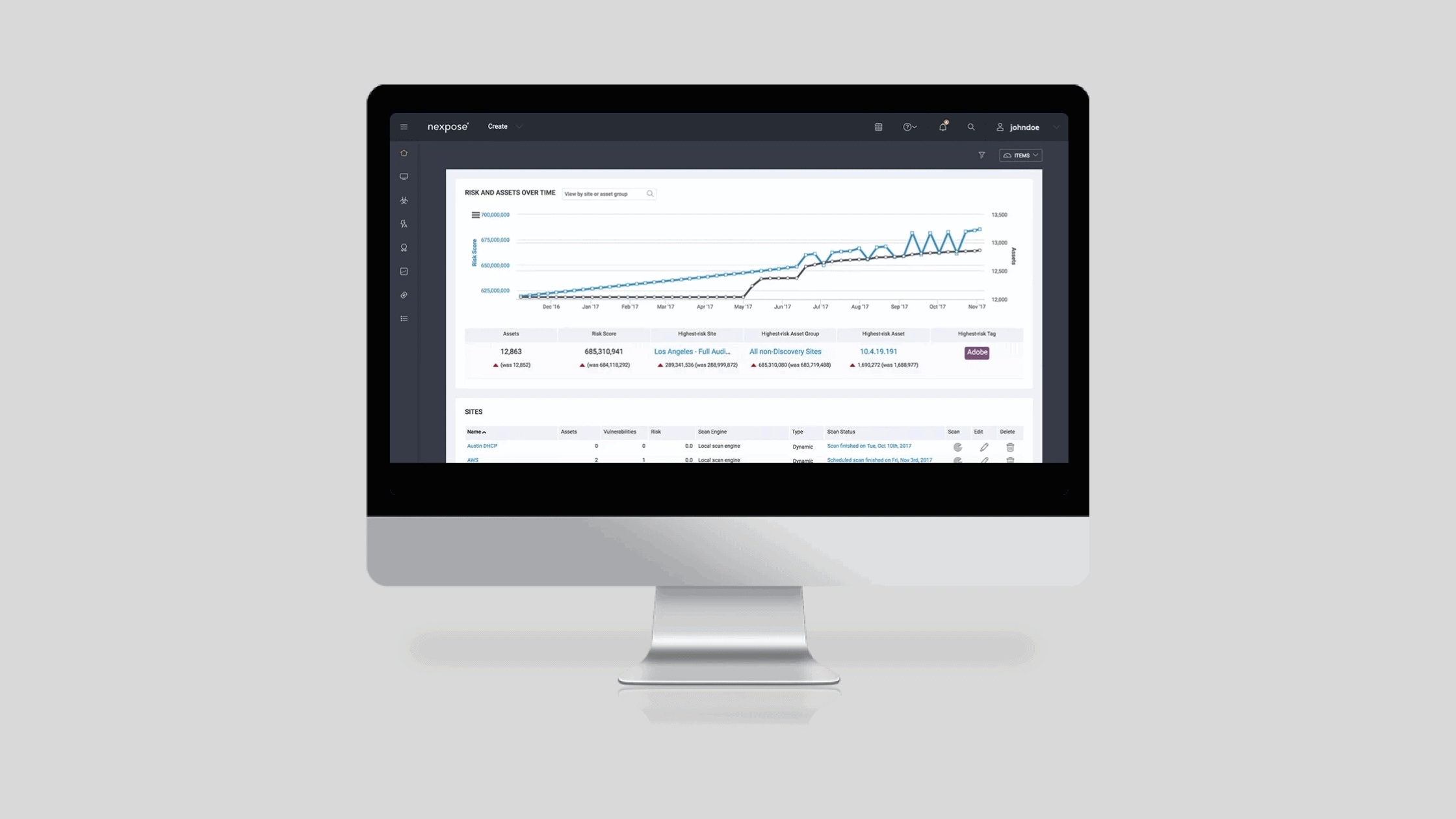
Interpreting the Vulnerability Scan Results
In less than 2 days, InsightVM completed its automated scan covering hundreds of nodes across dozens of network segments and subnets. The easy-to-navigate graphical dashboard provided full visibility into my findings:
With a few clicks, I was able to analyze results from multiple perspectives:
Exposure Coverage: What percentage of assets were scanned? Were any gaps or blind spots?
Total Risk Posture: How does the current vulnerability exposure compare historically?
Top Vulnerabilities: Which specific CVEs pose the most substantial risk?
Risk Trends: Are critical vulnerabilities increasing or decreasing over time?
These insights allowed me to quickly create a risk profile for the CISO highlighting areas needing improvement. From here, I could also drill down to see technical details on specific gaps for remediation.
Generating & Delivering Vulnerability Reports
The InsightVM reporting engine allowed me to customize reports catered to various audiences. A few that I created for this client:
Executive Summary: High-level overview of the organization’s vulnerability risk posture tailored for C-level executives.
Technical Asset Summary: Machine-readable JSON export detailing all vulnerabilities found for the ops team’s remediation ticketing/workflow.
Compliance Audit: Full listing of all vulnerabilities not yet passing regulations like SOC 2 to prepare for upcoming audits.
Trend Analysis: Historical charts on vulnerability risk trends to showcase progress over time to leadership.
These reports gave actionable insights customized for technical and leadership audiences. I delivered them securely via InsightVM’s web portal where only authorized users have access. This protects the highly sensitive data included from getting into the wrong hands.
Tracking Vulnerability Remediation Progress
My responsibility does not stop once I’ve delivered vulnerability scanning insights. I also closely track remediation progress working with the client’s technology teams. InsightVM allows me to assign vulnerabilities to specific asset owners and track lifecycle status via integrations with platforms like Jira.
I help apply context around resource constraints, change freezes, and other barriers hampering remediation progress. My goal is to enable practical prioritization so the most dangerous gaps get addressed immediately, while creating reasonable remediation timelines.
Regular vulnerability scanning cadences ensure any reappearances get flagged. Over several months working with this client, we’ve driven an over 30% decrease in severe vulnerabilities, improving their security posture substantially. But constant vigilance is key for sustained management.
The Importance of Vulnerability Management
By leveraging the powerful vulnerability scanning and reporting capabilities of Rapid7 InsightVM, I was able to provide immense value to this client by detecting vulnerabilities across their environment. This enables them to continuously monitor their attack surface, understand current risk levels, and improve security controls before attackers exploit any gaps.
What differentiates me as a security analyst is establishing trusted partnerships with clients via transparent assessments and recommendations. Never pointing fingers, only aiming to meaningfully reduce business risk. There are always more vulnerabilities, but staying committed to sustained remediation based on impact ensures steady enhancement of cyber resilience.
We hope this post helped in learning about how i detected vulnerabilities on client’s network. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.