Table of Contents
What is Kerberos? Comprehensive Step-by-Step Guide to Understanding How Kerberos Authentication Works?
In the realm of network security, Kerberos stands as a stalwart guardian, providing a robust framework for authentication and secure communication in distributed environments that keep your information safe when you’re using different programs or services. It was developed at MIT. Kerberos makes sure that only the right people or programs can access sensitive data by giving out special “tickets.” These tickets are like secret passes that allow users and services to communicate securely.
In this comprehensive guide, we’ll delve into the intricate details of what Kerberos is, providing a step-by-step Guide to Understanding How Kerberos Authentication Works.
What is Single Sign-On (SSO)?
Before we go into the details of Kerberos, we should be aware of single sign-on or in short SSO. SSO is a smart solution that allows users to access multiple applications and services with just one set of credentials, eliminating the need for repeated logins.
Every one of us would have used SSO knowingly or unknowingly. Remember while you browse some websites, it will give you the option to log in directly via your Gmail account or Facebook account, etc. This means you can use your default Gmail credentials to log in to multiple different unrelated accounts without remembering loads of passwords.
SSO streamlines the user experience, fostering efficiency and reducing the risk of password-related issues. As businesses and individuals navigate the complexities of a digital landscape, SSO emerges as a pivotal tool, enhancing both user convenience and overall security.
Key SSO benefits include:
Enhanced user experience – Less time spent managing credentials with a single sign-in.
Increased security – Only one master password instead of multiple credentials vulnerable to password attacks.
Higher productivity – Easy access to apps needed for work.
As digital ecosystems grow more complex with users needing access to many applications, SSO emerges as a pivotal tool improving both convenience and security.
Kerberos essentially provides single sign-on capabilities tailored for authentication across networked applications and services.
What is Kerberos? What are the Key Components of Kerberos?
Kerberos is like a digital key that helps you access different computer systems without needing separate passwords for each one. It’s an early form of Single Sign-On (SSO), making it easier for you to use various systems without remembering lots of different login details. Imagine having one key that opens the door to multiple rooms. In a Kerberos system, once you log in, you get a special ticket that lets you go into different places without entering your password each time. This is widely used, especially in systems like Microsoft Active Directory. In simple terms, Kerberos makes your online life simpler by managing your access to different places securely with just one digital key.
Now let’s breakdown how this works:
Components of a Kerberos Authentication System
Key Distribution Center (KDC): The KDC acts as a trusted third party, managing authentication services using symmetric-key cryptography. All network members, including clients and servers, are registered with the KDC, which securely maintains their secret keys.
Kerberos Authentication Server: The authentication server encompasses the functions of the KDC, housing both a ticket-granting service (TGS) and an authentication service (AS).
Although it’s typical for the ticket-granting service to be located on a different server, the authentication service is responsible for confirming the legitimacy and timeliness of tickets, often identified as the Key Distribution Center (KDC).
Ticket: A ticket serves as an encrypted message providing evidence that a subject is authorized to access a specific object. Also known as a service ticket (ST), users request tickets to access files or other objects. Tickets have set lifetimes and usage parameters, requiring renewal or reissuing once expired.
Ticket-Granting Ticket (TGT): The TGT offers proof that a subject has authenticated through the KDC and is authorized to request tickets for accessing various objects. Encrypted and containing a symmetric key, expiration time, and user’s IP address, the TGT is presented when requesting tickets for object access.
Kerberos Principal: Kerberos issues tickets to Kerberos principals, typically users but can be any entity eligible to request a ticket.
Kerberos Realm: In Kerberos terminology, a realm is a logically controlled area, like a domain or network, governed by Kerberos. Principals within the realm can request tickets from Kerberos, and the system can issue tickets to these principals within the defined realm.
With these elements in place, clients and servers can securely authenticate each other’s identities before communicating over the network.
Step-by-step guide on how Kerberos works.
Kerberos relies on an account database, commonly housed in a directory service like Microsoft’s Active Directory (AD). The system facilitates identity verification and mutual authentication by exchanging tickets among clients, network servers, and the Key Distribution Center (KDC). This process enables clients to request resources from servers, establishing mutual confidence in each other’s identities. The use of encrypted tickets ensures that login credentials, session keys, and authentication messages are never transmitted in cleartext, adding an extra layer of security to the authentication process.
Now, let’s dive into how the authentication works.
Initially, the user (client) has to verify their identity with the Kerberos, below are the steps followed.
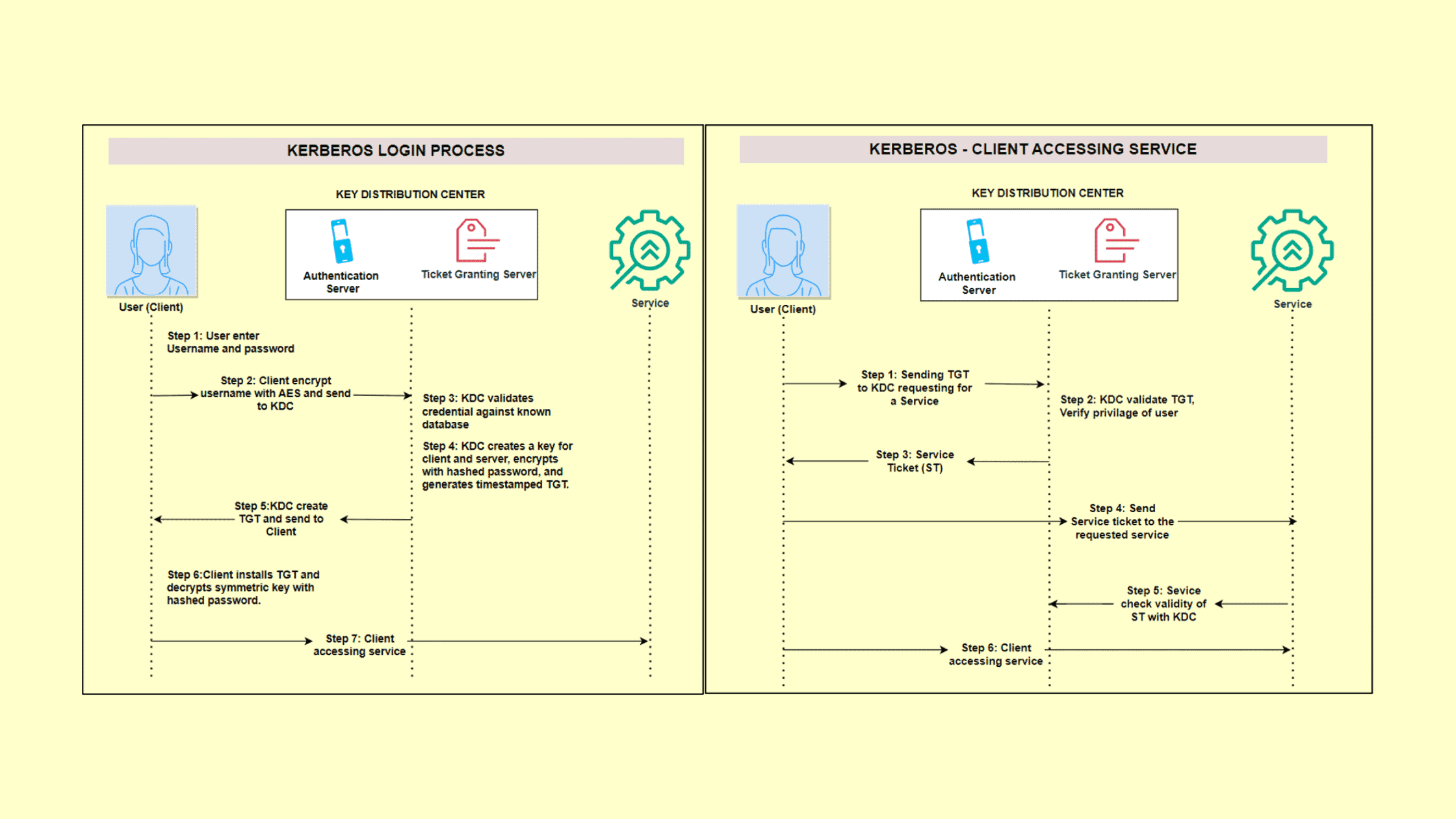
Kerberos Login:
The user initiates the authentication process by entering a username and password into the client interface.
The client employs the Advanced Encryption Standard (AES) to encrypt the username,(not password) preparing it for secure transmission to the Key Distribution Center (KDC).
The KDC conducts a verification check, confirming the provided username against a database of established credentials.
Upon successful verification, the KDC generates a symmetric key for use by both the client and the Kerberos server. This key is encrypted using a hash derived from the user’s password. Additionally, the KDC produces an encrypted timestamped Ticket Granting Ticket (TGT).
The KDC securely transmits both the encrypted symmetric key and the timestamped TGT to the client.
Subsequently, the client installs the TGT, utilizing it for authentication until its expiration.
Furthermore, the client decrypts the symmetric key by applying a hash function to the user’s password, ensuring access to the shared key for secure communication between the client and the Kerberos server. That is, if the user entered the wrong password the client will not be able to decrypt the symmetric key, since it is encrypted with the user’s original hashed password. Hence the login will not be successful.
With the TGT client can now access the required service, we will look into that section next.
Kerberos – Client accessing a service after successful authentication.
When a client seeks access to a network resource, it initiates the process by forwarding its Ticket Granting Ticket (TGT) back to the Key Distribution Center (KDC), accompanied by a request for access to the specific resource.
The KDC, in turn, undertakes the verification of the TGT’s validity and consults its access control matrix to confirm that the user possesses adequate privileges to access the requested resource.
Following successful verification, the KDC generates a service ticket tailored for the requested resource and dispatches it to the client.
The client then forwards this service ticket to the server or service responsible for hosting the desired resource.
The server or service hosting the resource conducts an authentication check by verifying the ticket’s validity with the KDC, ensuring that it is still legitimate.
Once the identity and authorization of the client are confirmed, the Kerberos activity concludes, and the client gains access to the requested resource.
From the above steps, it is very clear how important a role KDC plays in authentication, as much as it is useful it creates one major disadvantage to the system. KDC is a single point of failure, if KDC stops working or is compromised the whole system fails.In the event of a compromise to the KDC, the security of the entire network is jeopardized, as the secret key for every system is compromised. Moreover, should a KDC experience an outage, subject authentication becomes impossible.
Kerberos operates within stringent time constraints, requiring all systems to be time-synchronized within a 5-minute window. Failure to maintain synchronization renders previously issued Ticket Granting Tickets (TGTs) invalid, preventing the issuance of new tickets and denying the client access to protected network resources. To address this, network administrators often implement time synchronization systems, with one domain controller (DC) in an Active Directory domain syncing its time with an external Network Time Protocol (NTP) server. Subsequently, all other DCs synchronize their time with this primary DC, and other systems align their time with one of the DCs during logon processes. This intricate synchronization ensures the consistent and secure functioning of the Kerberos authentication system.
Why Kerberos Matters: Key Advantages
What makes this ticket-driven approach so useful?
Notable benefits include:
No passwords transmitted – Ticket exchange replaces passwords.
Mutual authentication – Both user and service validate each other.
Secure encrypted channel – Symmetric keys protect exchanges.
Single sign-on access – One TGT allows access to multiple services.
Centralized access control – Permissions managed on the KDC.
However, concentration of control on the KDC also introduces risks:
Compromise of the KDC compromises all authentication metadata.
Outages of the KDC server disrupt access to all services.
Use Cases: Where Kerberos Protects Access
The unique capabilities of Kerberos make it well suited for specific applications:
Enterprise authentication – Kerberos is deeply integrated in Microsoft Active Directory which underpins authentication across Windows Servers and corporate networks. The domain controller acts as the Key Distribution Center in this ecosystem.
Cloud access controls – Cloud infrastructure like Azure also integrate Kerberos authentication to manage access to resources.
Securing services – Open source distributions like Linux and Apache HTTP tap into Kerberos for user authentication and enabling encrypted communication.
Cross-domain single sign-on (SSO) – Kerberos’ ticket exchange protocols enables single sign-on across networks of services and Windows Server domains through trust relationships.
Conclusion
Kerberos was developed in the mid-1980. Since the introduction of Windows 2000, Microsoft has adopted the Kerberos protocol as the primary authentication method within the Windows operating system. This protocol has become an essential component of the Windows Active Directory (AD) service. This itself indicates the effectiveness of the protocol.
In conclusion, Kerberos stands as a cornerstone in the realm of network security, providing a robust and trusted framework for authentication. As Kerberos continues to be a default authentication method in major operating systems, including Microsoft Windows, its impact on ensuring secure and efficient user interactions in networked environments remains undeniable. Its continued importance highlights how Kerberos helps keep digital interactions safe and strengthens network security by preventing unauthorized access.
This comprehensive guide covered the step-by-step authentication flows, components and advantages of Kerberos network authentication. Its ticket-granting approach upholds both security and simplicity across single sign-on for distributed services.
Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
Aroma Rose Reji
Aroma is a cybersecurity professional with more than four years of experience in the industry. She has a strong background in detecting and defending cyber-attacks and possesses multiple global certifications like eCTHPv2, CEH, and CTIA. She is a pet lover and, in her free time, enjoys spending time with her cat, cooking, and traveling. You can connect with her on LinkedIn.