Table of Contents
How To Mitigate DFSCoerce, A PetitPotam Like NTLM Relay Attack On Domain Controllers
A security researcher Filip Dragovic has shared about a new NTLM relay attack on Domain Controllers. The attack was dubbed DFSCoerce, which makes use of the MS-DFSNM (Distributed File System Namespace Management) Protocol to relay DC authentication to ADCS (Active Directory Certificate Services). Ignorance of this Dragovic attack could allow attackers to obtain a certificate that can be used to obtain a Ticket Granting Ticket (TGT) from the domain controller. Considering its impact, we would say that it is highly important to fix or mitigate DFSCoerce. If you skipped to applying the mitigations for PetitPotam, an NTLM relay attack was discovered in 2021. apply the required changes as soon as you can. However, we have created this post to help people in learning how to mitigate DFSCoerce, a PetitPotam like NTLM relay attack on Domain Controllers.
Before we directly jump into the actual matter, it is better to clear a few concepts. Let’s begin this post with small information about the NTLM relay attack, the significance of MS-DFSNM, and finally, how to mitigate DFSCoerce, a PetitPotam like NTLM relay attack on Domain Controllers.
What Is NTLM Relay Attack?
The NTLM Relay Attack is a type of attack that allows an attacker to gain access to a network by relaying NTLM authentication requests. This attack can be used to compromise any account on the network, including administrator accounts.
In these attacks, an attacker who can get the NTLM authentication credentials of a user while they’re being transmitted between a client and a server can reflect or forward them to another server on which the user has an account. This would allow the intruder to access these resources as if he were the client.
MS-DFSNM (Distributed File System Namespace Management) Protocol:
MS-DFSNM is the protocol specification that defines how the Distributed File System Namespace (DFSN) is managed. DFSN is a Microsoft Windows feature that allows for the creation of a virtual file system, which can be used to provide high availability and load balancing for file shares in a networked environment. MS-DFSNM defines the methods and objects used by clients and servers to manage the namespace, as well as the format of the namespace metadata. MS-DFSNM also defines how namespace changes are propagated between servers, and how clients are redirected to the appropriate server when accessing files in the namespace.
In this context, it provides an RPC interface for administering DFS configurations. The client is an application that issues method calls on the RPC interface to administer DFS. The server is a DFS service that implements support for this RPC interface for administering DFS.
Summary Of DFSCoerce:
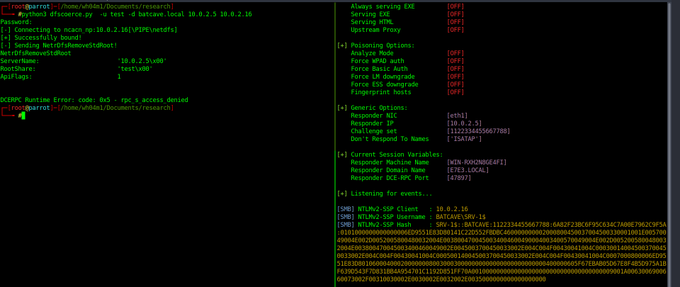
DFSCoerce is a newly discovered NTLM relay attack that could allow adversaries to relay DC authentication to ADCS using MS-DFSNM protocol. The flaw has no identifier assigned, and no CVSS score has been calculated yet.
A security researcher Filip Dragovic wrote “Spooler service disabled, RPC filters installed to prevent PetitPotam and File Server VSS Agent Service not installed but you still want to relay DC authentication to ADCS?
Don’t worry MS-DFSNM have your back ;)” in his tweet and shared the proof-of-concept for DFSCoerce .
In support of this, Will Dormann confirmed on Twitter that the PoC shared Filip Dragovic is working.
How To Mitigate DFSCoerce, A PetitPotam Like NTLM Relay Attack On Domain Controllers?
Since DFSCoerce is also an NTLM relay attack like PetitPotam, we could say that you are vulnerable to the flaw if you use any of these ADCS services in your environment.
Certificate Authority Web Enrollment
Certificate Enrollment Web Service
So we recommend implementing all the mitigations suggested for mitigating the PetitPotam attack.
Apply the Patches Released for CVE-2021-36942
“This update blocks the unauthenticated EfsRpcOpenFileRaw API call that is exposed through the LSARPC interface. Note that the EFSRPC interface for accessing EfsRpcOpenFileRaw is still reachable to authenticated users after installing this update. In addition, other EFSRPC functions that require authentication to exploit are still exposed to users via LSARPC after this update is installed. This required authentication may take place silently via SSO on domain-joined systems. Please see KB5005413 for several additional workarounds that can help mitigate other techniques for relaying NTLM credentials using an AD CS server.”
Enable EPA (Extended Protection for Authentication) and Disable HTTP on AD CS Servers
Please read this post for more details: https://support.microsoft.com/en-us/topic/kb5005413-mitigating-ntlm-relay-attacks-on-active-directory-certificate-services-ad-cs-3612b773-4043-4aa9-b23d-b87910cd3429
Disable NTLM on Domain Controllers, IIS, and AD CS servers
Disable the incoming NTLM authentication on wherever possible. Follow these documentations to disable the NTLM on:
Active Directory Certificate Service: To configure this GPO, open Group Policy and go to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options and set Network security: Restrict NTLM: Incoming NTLM traffic to Deny All Accounts or Deny All domain accounts.
Internet Information Services: Disable NTLM on the IIS servers on which “Certificate Authority Web Enrollment” or “Certificate Enrollment Web Service” services are running, Open IIS Manager, Select Sites -> Default Web Site (or another name if it was manually reconfigured) -> *-CA_CES_Kerberos and CertSrv, Select Windows Authentication, , ick the Providers… link on the right side, Select NTLM, Click the Remove Button, Restart IIS from an Administrator CMD prompt: iisreset /restart.
Block [MS-ESFR] (EFSRPC) using RPC filters
This can be done by blocking the RPC interface UUIDs for EFSRPC. Refer this post for more information.
We hope this post would help you know how to mitigate DFSCoerce, a PetitPotam like NTLM relay attack on Domain Controllers. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium & Instagram, and subscribe to receive updates like this.
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.