Table of Contents
Understand The Role Of File Ownership And Permissions In Linux
For many Linux users, file ownership and permissions can be difficult to get used to. It is usually hypothesized that a command line is required to accomplish what you desire from the file system. The good news is there are other methods for dealing with the file system which offers greater strength and flexibility, that many people are unaware of. The easiest desktop interface eliminates the need for command-line usage even if you have to deal with the file ownership and permissions. Files and folders can actually be managed from the file manager. However, it is always better to understand what you are doing before accessing the graphic user interface.
The sudo Command In Linux
The sudo command is the short form of ‘superuser do’. It grants the required permissions for executing a command similar to another user, for instance, the superuser. Sudo gives authorized users the provision to execute commands as another user, – specified in the / etc/sudoers file. The effective and real GID and UID of the issuing user are matched with those of the target user as laid down in the password file. By default, sudo requires users to authenticate themselves using a password. This authentication involves the user-specific password and not the root password itself.
After user authentication, a timestamp is logged, and the user can use sudo for a short period without a password. This timestamp can be updated if the user issues sudo command using the -v tag. If an unauthorized user tries to execute a command via sudo, the attempt to breach system security will be considered unsuccessful, and an email will be sent to the appropriate authority. The default permission given for failing to execute this command lies with the root. Note that if an unauthorized user tries to run sudo using the -l or -v tags, no mail will be sent. This is so because these commands enable users to determine if they are allowed to use the sudo command.
Sudo can record successful and failed attempts (in addition to errors) in the system log (Syslog), a unique log file, or both. By default, sudo makes the entry into the Syslog, but this can be changed during configuration time or in the sudoers file. If the execution of the program is successful, the return value from sudo will be the return value of the program executed.
Otherwise, sudo exits a port value of 1 if there is a configuration/authorization problem or if it cannot execute the specified command. In the latter case, the error string is exported to ‘stderr’. If sudo cannot enter one or more entries in the user’s PATH, an error is printed to stderr. This usually does not occur under normal circumstances. The most common reason for returning the “permission denied” is when you make an automatic transition and one of your PATH directories is on a device that is currently unreachable.
Sudo strives to be safe when commands are executed. Variables that determine the mannerism of dynamic loading and binding can be utilized for subverting a program that is being run by sudo. As a resolution, it may remove Some environmental variables specific to the system, particularly from the environment that issues the commands which are to be executed. Examples:
Sudo shutdown -r now: This command will restart the system and execute the shutdown command as root
sudo -u arunkl ls /home/David/Documents: This command will list g the content of the home/David/ Documents directory as the user arunkl
sudo -u arunkl -g David mkdir /home/otheruser/Documents/newfiles:
(This command will create a new directory with the command mkdir as the user arunkl with arunkl’s current group set to David. Ma roup set to David. arunkl, however. must be a member of the David group.)
Sudo -v: It resets or extends the timeout for automated authentication all ing you to continue by using the sudo comnmands, without submitting the noeo asSword.
Sudo -k: It will terminate the sudo authentication of the existing user. Therefors the next sudo command will need password verification.
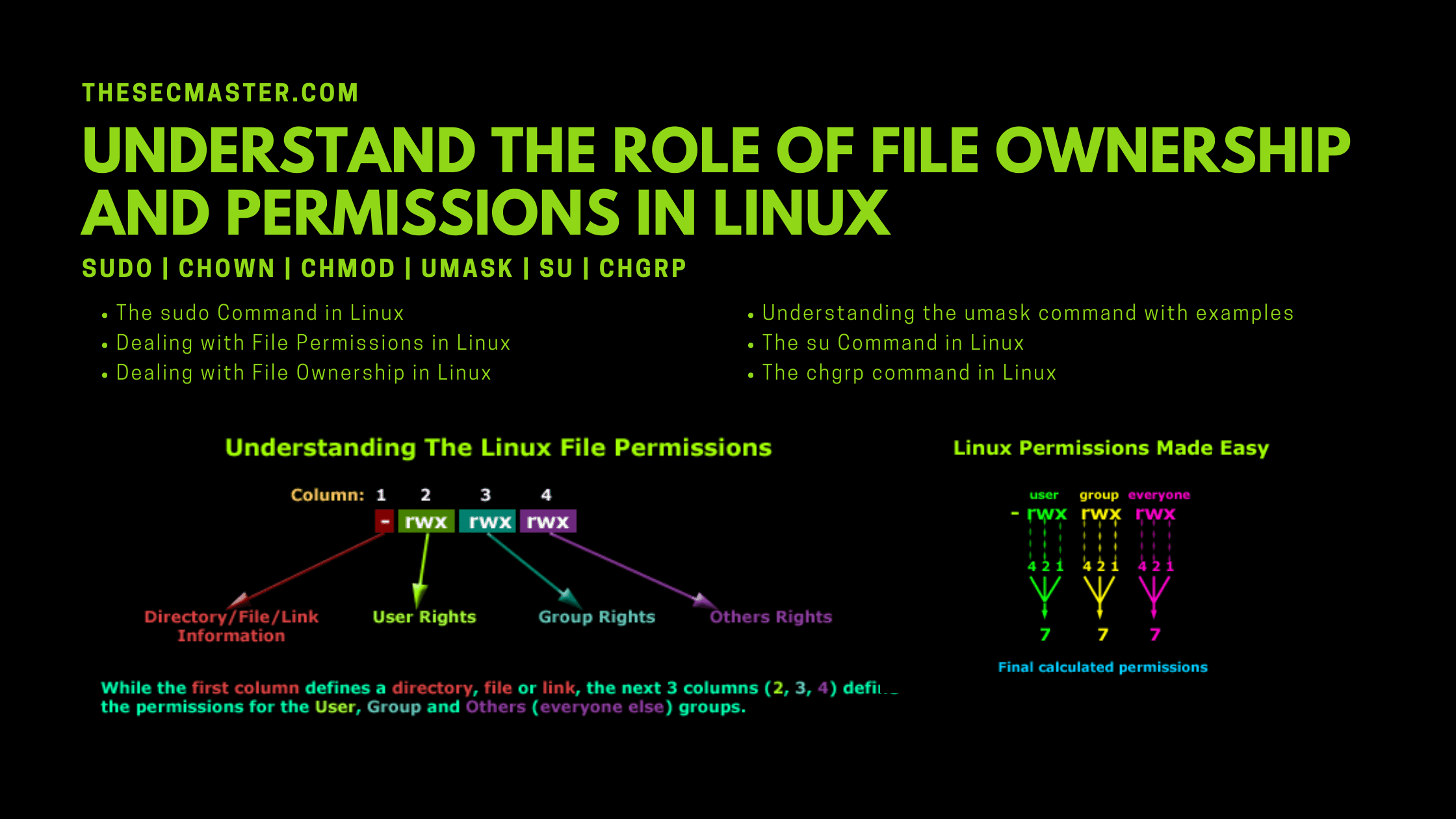
Dealing With File Permissions In Linux
There are two simple commands to manipulate the file ownership and permissions in the Linux file system as depicted below:For changing ownerships, you can use the command: chown Likewise, to change the permission of a file, you can use the command: chmod It is not difficult to use either of these two commands. However, note that only the root user or the current owner can change permissions or file ownership. For example, a new folder has been created with the name /DAT/SHA in the data partition. Users arunkl and David need to read and write access to this folder. There are several ways to do this. If Bethany and Jacob are the only users of the system (and the network is known to be very safe)., you can change the folder permissions to allow access. One way to do this is to issue the command:
sudo chmod -R ugo+rw /DAT/SHA
This command is explained in detail as follows-
sudo: It renders admin privileges to the executed command (otherws the command given above must be rooted and run without “sudo )
chmod: command to change permissions
-R: It changes the permissions of the parent folder and its dependent objects
ugo + rw: Here users, group, and others are granted read-write permissions
/DAT/SHA: indicates the modified directory.
As you can see, this command opens the SHARE folder and makes it accessible to anyone in the system. It must be remembered that this is purely for demonstration. As far as, the permission part is concerned, it is explained below.
u for user
g for group
o for others
You need to use ‘o’ prudently since it gives everyone read and writes access. The permitted permissions that you can give to a file are explained below:
r for read
w for write
e for execute
The use of the -R key is important. If there are many subfolders and files in the SHA directory and you wish to apply for the permissions from the parent folder to all the dependent subfolders then you need to use the-R(recursion) key.
Dealing With File Ownership In Linux
Changing the ownership of a file or folder is easy. Let’s say David transited a folder for arunkl in the SHARE library – but David still has ownership. This can be changed with simple commands like:
sudo chown-R arunkl /DATA/SHARE
Understanding The Umask Command With Examples
In GNU / Linux systems, each file or folder has permissions. There are three types of permissions (those allowed for each file type, including directories).
(R) Read access
(W) Write permission
(E) Execute
Permissions are defined for three types of users.
(U) file owner
(G) A group to which the owner belongs
(0) All other users
umask (User Mask) is a POSIX environment command and function that defines the file creation mask for the current process, which determines the permissions of files and directories created by the process. The process may change the file status creation mask using umask, and the subsystem will obtain the new value. You can use umask to set new file permissions that the process creates.
The user mask contains octal permission values that are assigned to all new files. To calculate the umask value, the authorization value from which you have to subtract is 666 for files and 777 for directories. The value you get then has to be used with the umask command.
For instance, there is a need for changing the default file mode to 664 (rw-wr-). On subtracting between 666 and 664, you get 002. This is the value that will be used as an argument to the umask command, as shown below:
Umask 002
You can also check the permissions through unmask command. For example, when we create a file in the temp directory
cd/ temp
touch newfile
ls -1 newfile
We get an output like this one:
-rw -r—r-
Here the user who has created the file can read and write, the group to which the user belongs can only read, and accordingly, all others can read-only. The octal value for this umask is 0x022. To check this value using umask command.
Umask
You will get the output 0022Moreover, you may have file processes and daemons, and you may want to manage the permissions on those files. In this case the question is who shares the same Apache group? In general, you should place the umask command in the script used to run the daemon or in the first included file. So for Apache this is environment includes ///apache2/envvars. You can now execute the command-
Umask 002
And restart your apache.
The su Command In Linux
In Linux, the command ‘su’ is used to switch over from one user account to another. When you enter the su command, you will be prompted to enter the password for the user to whose account you want to switch. For instance, you want to switch over to the user account, arunkl. Then use this command-
su arunkl
The su command can also be used to switch over to the root account. Here, you have to enter the su command without any parameters or arguments:
Su
You will be prompted to enter the password for the root user. The arguments, which are commonly used while invoking the su command are -, -S, and -login. For instance, if you desire to run a login shell similar to the real login and simultaneously change the current directory, enter this command
su –
You can use the”–” argument to separate su option from other arguuments that are present in the shell. If necessary, the user is asked to enter a password. An invalid password generates an error message. All valid and invalid attempts are recorded for detecting system abuse. Likewise, if you desire to run another shell, you can use the -s option. For example, if you want to switch to the root and run the shell called zsh then you need to type:
su -s /usr/bin/zsh
On the other hand, if you are desirous of preserving the whole environment of the calling user, then you can use the -p option.
su -p
Additional arguments can be provided after the username. In this case, it will be provided in the user login shell. In particular, if you specify the argument, most command interpreters refer to the following argument as order. The command is executed by the shell specified in the target user’s
etc/passwd
If the su command is successfully executed, it will return the exit value of the command that was executed. In the event that a signal terminates the command then su will return the value of the signal along the lines of plus 128. Moreover, if su terminates or kills a command, then it will return 255.
The chgrp Command In Linux
The Linux chgrp command is used to change the group ownership of a file or directory. First, you must have admin rights to add or remove groups. You can connect as root or use sudo to connect. To add a new group, you can use:
sudo addgroup groupname
Example 1: Change the group ownership of a file.
sudo chgrp groupname filename
Example 2: To change the group ownership of a folder.
sudo chgrp groupname foldername
Example 3: Recursively change a group’s ownership of a folder and all other subfolders and files, files within a subfolder
sudo chgrp -R groupname foldername
Example 4: Using the group name of a reference file to change the group of another folder or file:
sudo chgrp -R –reference=filename foldername
Example 5: Describing the action of a file whose group has been changed
sudo chgrp -c groupname filename
Example 6: Suppression of error messages
sudo chgrp -f groupname filename
Example 7: Describing the non-action and action of every file
sudo chgrp -v groupname filename
We hope this post will help you in explore package management in Linux. Thanks for reading this post. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.