Table of Contents
What is a Self Signed Certificate? How to Create a Self Signed Certificate Using OpenSSL?
Secure communication over the internet relies on two critical components – encryption and authentication. Encryption protects data from being spied on or tampered with while in transit. Authentication ensures you are communicating with whom you intended, not an impersonator.
Public key infrastructure (PKI) provides a framework to enable trusted encryption and authentication for any communication over the internet. It uses digital certificates and certificate authorities (CAs) to establish identity and distribute keys.
A digital certificate is an electronic document that contains identifying details like name, address, company etc. along with a public key. This certificate is digitally signed and issued by a trusted certificate authority (CA), which vouches for the identity of the certificate holder.
Browsers and operating systems trust certificates issued by reputed CAs like Symantec, Comodo, DigiCert etc. They maintain lists of trusted root and intermediate CAs based on standards like Mozilla’s CA Certificate Program. So when you visit a website that presents a valid certificate issued by a trusted CA, you can be rest assured that communication is securely encrypted and you are connecting to the intended server, not an imposter. This trusted public key infrastructure enabled by CAs is vital for ecommerce and other sensitive online transactions.
Self-signed certificates offer an alternative approach when identity validation is not important, like in testing environments. In this post, we will dive into what self-signed certificates are, their pros and cons, and how to create Self-signed certificates using OpenSSL.
What is a Self Signed Certificate?
As we said before, secure sockets layer (SSL) and transport layer security (TLS) protocols use digital certificates to establish encrypted communication and authenticate identities between two parties over the internet. These digital certificates confirm the ownership of a public key by an entity like an organization, domain, or individual. Public key infrastructure (PKI) provides a framework to issue, distribute, and validate these certificates using certificate authorities (CAs).
Before we go to self signed certificate, we feel it’s good to know the types of Certificate Authorities (CAs). There are two types of certificate authorities that can issue SSL/TLS certificates:
Public CAs – Trusted third party organizations like Symantec, Comodo, DigiCert etc. that issue certificates after verifying the identity of the applicant based on a set of procedures. Browsers and operating systems trust certificates issued by these CAs by including their root certificates in the trust store. For example, Microsoft trusts root certificates from CAs that follow the CA/Browser Forum’s Baseline Requirements. Public CAs issue SSL/TLS certificates mainly for public-facing websites and internet communication.
Private or Local CAs – Organizations can run their own private CA server like Microsoft Active Directory Certificate Services to issue certificates for internal use. These certificates will be trusted only within the organization network. Private CAs are used to issue certificates for intra-organization communication between servers, systems, devices etc. where extensive identity validation is not required.
Based on the issuing CA, there are two types of SSL/TLS certificates:
Public Certificates – Issued by trusted third party public CAs like Comodo, DigiCert, Symantec etc. after validating the applicant’s identity. They are universally trusted by browsers and operating systems. But the issuance process involves time, cost and sharing identity proofs with the external CA.
Private Certificates – Issued by an organization’s own Private CA server for internal usage like encrypting backups, securing internal communications etc. They are only trusted within the organization’s systems. The issuance process can be automated and is free, but does not validate identity extensively.
Self-signed certificates belong to the private certificate category, but with a key difference – they are not issued by any CA, private or public!
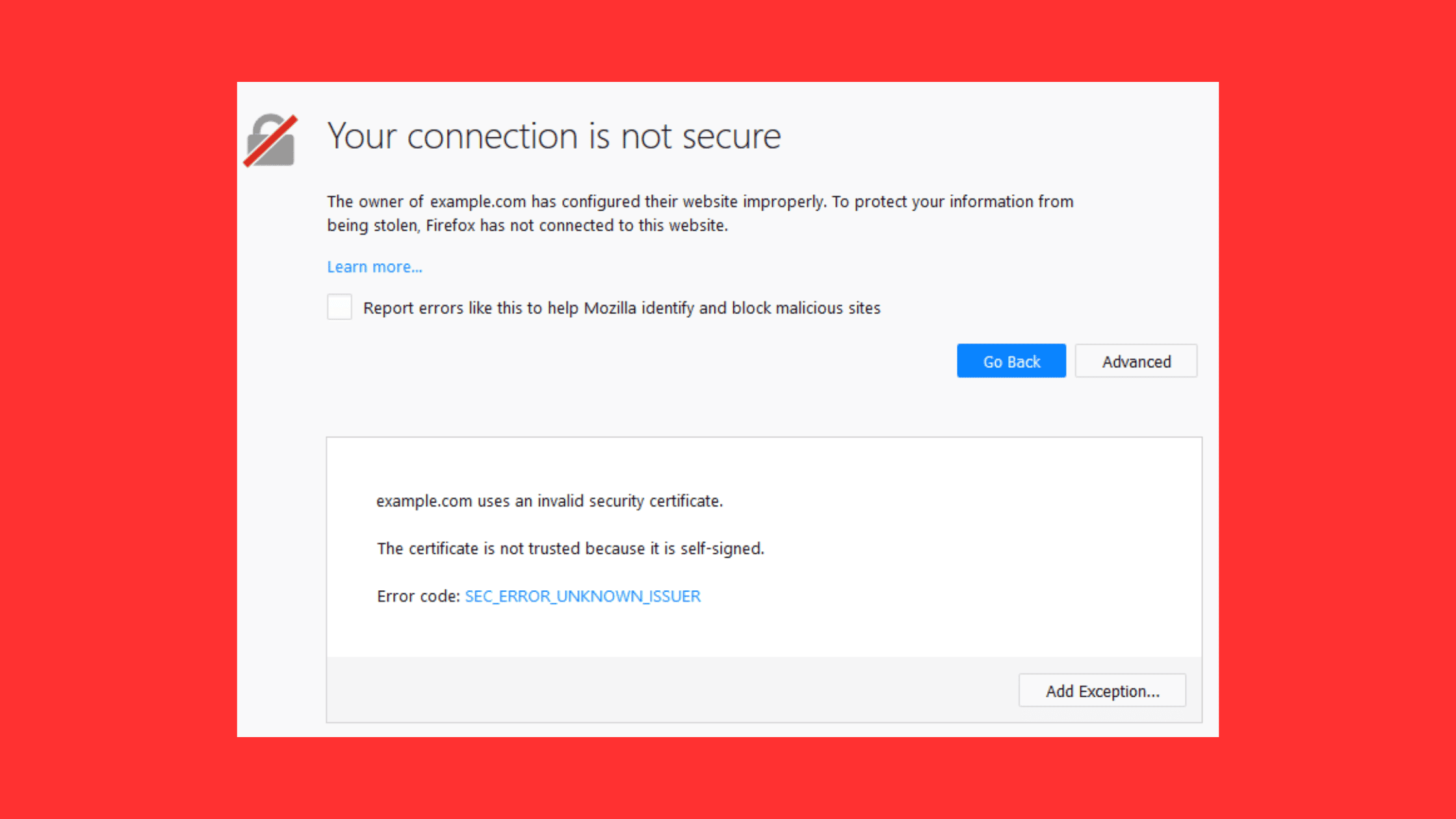
A self-signed certificate is signed by its own private key rather than being signed by a trusted CA. There is no external validation or proof of identity involved. The key pair generation and signing process is fully under the control of the entity requiring the certificate.
This distinction makes self-signed certificates untrusted by default. Browsers and operating systems will show security warnings when users try to access a website using a self-signed certificate. It does not assure users that they are communicating with the intended server. Additional steps have to be taken to manually trust or distribute a self-signed certificate.
The main scenarios where self-signed certificates are used are:
During development to test applications, APIs, configurations etc. before deploying the final trusted certificates from a public CA.
Securing internal-only communications and systems within an organization where deep identity validation is not crucial.
The drivers for using self-signed certificates are cost, convenience and flexibility. But the lack of inherent trust limits their usage for public facing production websites and systems accessible from outside the organization’s network.
What are the Advantages and Disadvantages of Self Signed Certificates?
After we learn what is a self signed certificate, let’s decide whether it full fills your requirement by listing some of the advantages and disadvantages of self signed certificates. Self-signed certificates provide certain benefits but also come with some downsides compared to CA-signed certificates. Let’s look at the key advantages and disadvantages of using self-signed certificates:
Advantages of Self Signed Certificates
Cost – There is no cost involved in creating self-signed certificates unlike public SSL/TLS certificates which need to be purchased annually.
Convenience – Anyone can instantly generate a self-signed certificate using tools like OpenSSL without any application process. No identity validation needed.
Flexibility – You have full control over the certificate contents like key type, signature algorithms, metadata fields etc. since you generate it yourself.
Avoid External Dependence – Self-signed certificates reduce reliance on external CAs that could potentially get compromised themselves.
Internal Usage – Perfectly suitable for testing environments or securing internal communications where extensive identity proofing is not required.
Life Span – Self signed certificates doesn’t come with mandatory expiry date. You can set the expiration date as long as you need it.
Disadvantages of Self Signed Certificates
No Trust – The biggest drawback is that self-signed certificates are not trusted by browsers and operating systems by default, necessitating manual intervention.
No Revocation Support – Unlike CA certificates, a self-signed certificate cannot be revoked by a CA if its private key is compromised. The entity has to manually distribute revocation status.
Lack of Support – You are on your own in terms of troubleshooting, updates etc. Public CAs provide dedicated technical support.
Overhead – Managing numerous self-signed certificates involves significant administrative overheads for tracking, renewing and distributing them.
How to Create a Self Signed Certificate Using OpenSSL?
OpenSSL is an open-source toolkit that implements SSL/TLS protocols and provides various cryptographic functions. We can use OpenSSL to easily create self-signed certificates from the command line.
Creating a self-signed certificate using OpenSSL is a relatively simple process. The first step is to generate the key pair, which has a private key as well as a public key. This will be used to sign the certificate in Step 4. The second step is to extract the public key from the key pair. The third step is to generate a Certificate Signing Request (CSR). This will be used by the certificate authority (CA) to create the self-signed certificate. You will be prompted to enter a variety of information, such as the common name, organization name, organization unit, country code, email address, and many more. Finally, generate the self-signed certificate using the private key and CSR. Simple, Isn’t it?
Follow these steps to generate a self-signed certificate using OpenSSL:
Step 1: Generate Key pair using OpenSSL
To create the key pair, run this command in your terminal:
openssl genrsa -out private.key 2048 This command will generate an RSA key pair with a length of 2048.
Step 2: Extract the public key from the key pair
Run this command to extract the public key from the key pair generated in step 1.
openssl rsa -in private.key -pubout -out public.keyStep 3: Create a Certificate Signing Request (CSR)
The next step is to create a Certificate Signing Request (CSR). This will be used by the certificate authority (CA) to create the self-signed certificate. To generate the CSR, run this command in your terminal:
You will be prompted to enter a variety of information, such as the common name, organization name, organization unit, country code, email address, optional password, and many more. Enter the valid input it asks to generate the CSR. For example, the country name should be two char country codes. The common name should be the FQDN or IP to which you are going to get the certificate. The CSR is now ready for the CA to generate a self-signed certificate.
openssl req -new -key private.key -out certificate.csrWe suggest verifying the CSR generated before you submit it to the Certificate Authority. Run this command to verify the details of your CSR.
openssl req -text -in certificate.csr -noout -verifyStep 4: Create the self-signed certificate
Finally, generate the self-signed certificate using the private key and CSR. Run this command to generate the self-signed certificate on the terminal:
openssl x509 -in certificate.csr -out certificate.crt -req -signkey private.key -days 365This creates a certificate valid for 365 days.
The process takes just a few simple OpenSSL commands and about 15 minutes. See how easy it is to create a self-signed certificate!
Bottom Line
Self-signed certificates provide an easy way to test encrypted communications and code before deploying production certificates from a trusted CA. They allow internal traffic to be secured without identity validation.
However, the lack of trust from browsers and potential security risks make self-signed certificates unsuitable for public facing websites and applications accessible externally. They can be useful in development and internal environments but need close monitoring and manual renewal when used extensively.
For any business-critical systems, it is always recommended to use certificates from a reputable CA that will be trusted by default across all devices and browsers.
We hope this guide helps understand everything about the self signed certificate and how to create a self signed certificate in 4 simple steps using OpenSSL. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website, thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
You may also like these articles:
How to Set Up A Certificate Authority On Ubuntu Using OpenSSL?
Step-By-Step Procedure To Set Up An Enterprise Root CA On Windows Server
The Most Useful OpenSSL Commands to Work With SSL Certificates
Step-By-Step Procedure To Install SSL/TLS Certificate On Nginx Web Server!
What Is A PKI Certificate? What Are The Different Types Of PKI Certificates?
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.