Table of Contents
What is an MFA Fatigue Attack? How to Defend Against an MFA Fatigue Attack?
Leaked or stolen credentials are one of the primary sources that cybercriminals use to breach your network and collect sensitive and critical information such as bank details, client details, etc. A normal authentication contains a username and password. To increase an additional level of security, we use two or more-layer authentication, which is known as multifactor authentication. Even after multiple layers of protection, the attackers are still capable of breaching a network.
In this post, we will discuss multifactor authentication, what is an MFA fatigue attack, how to defend against an MFA fatigue attack, and how to prevent an MFA fatigue attack.
What is MFA? Why is MFA Used?
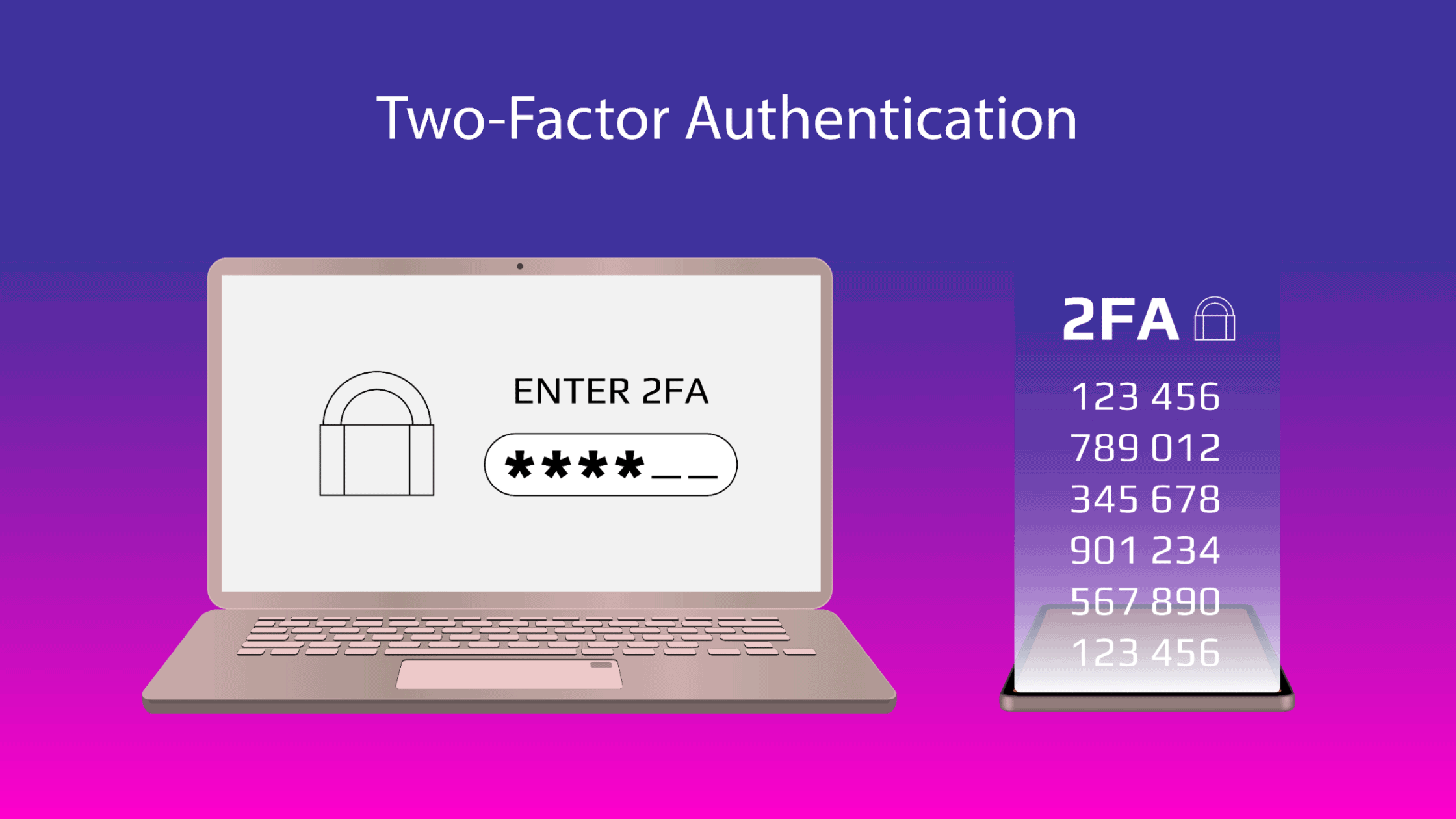
MFA or multifactor authentication is a technology where two or more layers of authentication are used. The authentication methods primarily consist of something the user knows(password), something the user is (biometrics), and something the user has (authentication code, mobile). The authentication methods used in multifactor authentication should be independent, which creates a layered defense that makes it more difficult for the attacker to breach into your network even if they could compromise one factor.
There is a huge amount of leaked credentials published over the dark or deep web after any security breach. This information can be used by an attacker to log in and steal sensitive information from the user. In order to protect from such scenarios, multifactor authentication helps greatly. An attacker will require a second set of authentications even if they can get their hands on the leaked password.
How Does MFA Work?
Once multifactor authentication is enabled, the user will be prompted to enter the second authentication after logging in with the username and password. The majority of the time, the second authentication factor will be a code sent to your phone via SMS or e-mail. It can also be via an app like Google Authenticator or by using biometrics like fingerprint or facial recognition.
If an authenticator app is used, the code provided only last for a few seconds, and you need to enter the code before the time expires. Such codes make it much more difficult for the attacker to crack since it is almost impossible for them to generate the code at the correct time.
This might feel like a bit tedious process and take up a bit of extra time, but it’s all worth the additional security that MFA provides.
Benefits of MFA
There are multiple benefits for MFA over single-factor authentication, such as:
Reduced risk
Protection against frail passwords
Improve user experience
Reduced cost of damage
There are multiple ways for an attacker to obtain your password or credentials, like keylogging, Phishing, etc. However, the second authentication is much more difficult to obtain as it depends on multiple other parameters. This also helps even if your password is weak and can be easily guessed.
The user involvement using multifactor authentication can be more convenient as they can use biometrics like fingerprint and face detection etc. This also makes the user more aware of what they are logging in to.
What is an MFA Fatigue Attack?
We have read about multifactor authentication and its benefits. It’s time to know that no security feature is not 100% un-hackable. One of the primary ways of using multifactor authentication in organizations is to push a notification prompt while the user tries to log in with the credentials. These push notifications are to verify if the login attempt is legitimate, where it also shows the location of the login and other details like the device used etc, if configured.
Image source: Microsoft
An attacker can misuse this feature by running a script that pushes multiple MFA login prompts on the account owner’s mobile device in a very short duration of time after trying to log in with a stolen credential, which will eventually confuse the user. The goal is to bombard the user with multiple MFA requests, thus inflicting a sense of “fatigue” on the user.
In many cases, the attacker might try to contact the user via e-mail, WhatsApp, or any other reliable messaging platform pretending as IT Service support and trick the user into accepting the MFA prompt.
Eventually, the user will get tired and unintentionally click the approve button once, to stop the flow of incoming MFA requests, which ultimately gives full access to the attacker. This type of social engineering technique is proven highly efficient by multiple ransomware gangs like Lapsus$ and Yanluowang and has breached multiple top organizations like Microsoft, Uber, etc.
Video source:
A Case Study on Uber Hack Using MFA Fatigue Attack
In the recent attack on Uber, the hacker breached the network using social engineering techniques. The threat actor gained access to one of the Uber employee’s credentials and tried an MFA fatigue attack on the user. The attacker also pretended to be Uber IT support to convince the user to accept the Multifactor Authentication request.
Image source: Kevin Beaumont
After successfully gaining access, the attacker logged into the internal network via the corporate VPN and started scanning the company’s network for any sensitive and critical information. The attacker was successful in getting the company’s sensitive data.
How to Defend Against MFA Fatigue Attacks
With the advancement of technology, the techniques used by attackers also grow exponentially. As a user or as an organization, we can implement some measures to prevent MFA fatigue attack
MFA fatigue attack can be reduced to a large extent by confirming a user’s identity by using any of the two factors, which include what the user knows, what the user owns, and what the user is.
A threshold limit should be set for MFA request numbers per user.
Instead of a push notification, OTP (one-time password) should be implemented.
Rather than having to allow or deny option in an MFA push notification, number matching authentication should be in place, which means the end user has to click the correct number before authenticating.
Proper password policies should be in place.
Avoid using the same passwords for multiple platforms, which will help in preventing the attacker from creating more damage even if one credential is leaked.
In most cases, the attacker targets a non-technical employee for breaching into a network as most of the users are not even aware that these types of attacks exist, which makes the MFA request and the fake IT support look legitimate. User awareness is one of the major criteria to avoid being a victim of an MFA fatigue attack.
Organizations should push more effective multifactor authentication methods, such as setting up an OTP instead of a push notification, as it requires more user involvement hence preventing accidental accepting of MFA requests. One of the other methods is to have a number matching which also encourages more user involvement by needing round-trip information for login. Such effective steps we’ll help an organization to protect itself from being a victim of cyber-attack.
I hope this article helped in understanding Multifactor Authentication, what is an MFA fatigue attack, how to defend against an MFA fatigue attack, and how to prevent an MFA fatigue attack. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium & Instagram, and subscribe to receive updates like this.
You may also like these articles:
Aroma Rose Reji
Aroma is a cybersecurity professional with more than four years of experience in the industry. She has a strong background in detecting and defending cyber-attacks and possesses multiple global certifications like eCTHPv2, CEH, and CTIA. She is a pet lover and, in her free time, enjoys spending time with her cat, cooking, and traveling. You can connect with her on LinkedIn.