Table of Contents
How To Protect Azure Active Directory From Undetected Brute-Force Attacks?
Security researchers identified a flaw in Azure AD (Active Directory) Single Sign-On protocol which could let an attacker perform single-factor brute-force attacks against Azure AD (Active Directory) without generating sign-in events. Let’s see how to protect Azure AD (Active Directory) from undetected brute-force attacks.
What Is Azure Active Directory?
Azure Active Directory is Microsoft’s enterprise cloud-based Identity Service Provider which provides IAM (Identity and Access Management) solutions to the enterprise apps from any ware. Azure AD offers Single Sign-On, Conditional Access, and multi-factor authentication services to the apps. It helps organizations to securely manage the user from on-premises or remote locations. It automates workflows for user lifecycle and provisioning. It saves both time and resources with self-service management.
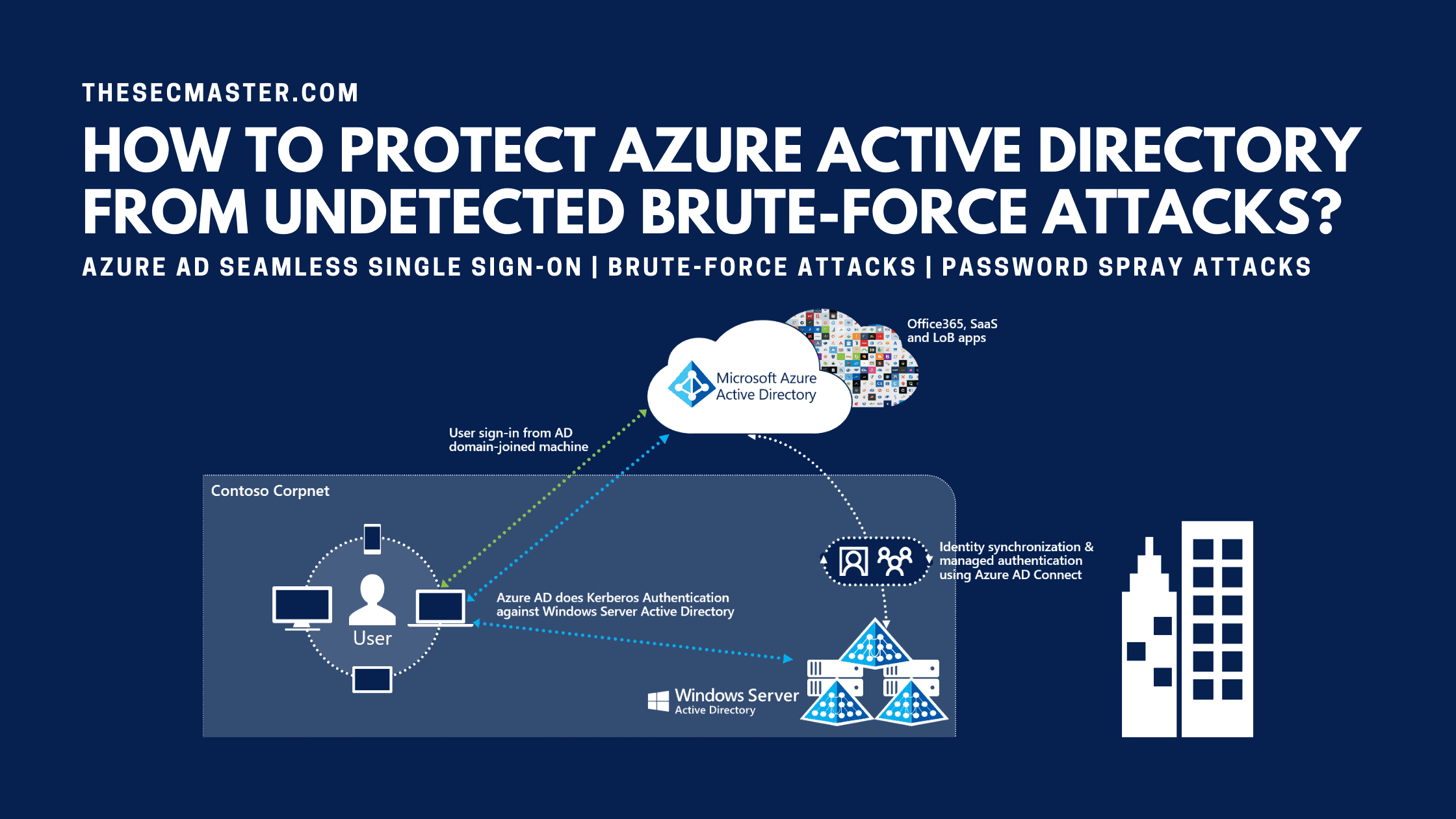
How Does Azure AD Seamless Single Sign-On Work?
The prime function of Azure AD Seamless Single Sign-On is to facilitate a user in managing his auto logins. Seamless SSO ensures the user doesn’t need to log in to the Azure AD when he has logged in to his computer with his domain account. When Seamless SSO is configured on the Azure AD, a computer object named AZUREADSSOACC will be created on the on-prim AD domain with a Service Principal Name (SPN), a unique identifier of a service instance for a service logon account during Kerberos authentication. On-premises AD will send the name and password hash of the AZUREADSSOACC computer object to the Azure AD so that Azure AD will accept Kerberos tickets through the Autologon service.
When a user tries accessing Azure AD from his browser, Azure AD validates the Seamless SSO service and recognizes that the user’s tenant is configured to use Seamless SSO. Of Axure AD identifies the Seamless SSO configurations, it redirects the user’s browser to Autologon.
When the user tries accessing the Azure AD, the Autologon service will send a Kerberos challenge to the user. At this point in time, the user’s browser behaves like a logged-in user and requests a Ticket Granting Ticket (TGT) from on-premises AD. The on-premises AD sends a TGT to the user’s browser.
The user’s browser requests Autologon access from the on-premises AD and provides the TGT as proof of identity. On-Premises AD locates the corresponding computer object and creates a Service Ticket (ST) encrypted with the AZUREADSSOACC computer account’s password hash.
The user’s browser will send a subsequent request to Autologon and provides the Service Ticket. Autologon decrypts the Service Ticket with the AZUREADSSOACC computer account’s password hash and issues a DesktopSSOToken access token for the user’s browser via a redirect request to Azure AD.
At last, the user’s browser sends a substituent request to the Azure AD using the DesktopSSOToken as the SAM assertion.
How Attackers Abuse Azure AD Seamless SSO Flaw To Perform Undetected Brute-Force Attacks?
The flaw exists in the Azure AD Seamless Single Sign-On, a service that allows users to login Azure AD without entering the username and passwords when they are connected to the corporate network.
When a user tries accessing Azure AD from his browser, Azure AD validates the Seamless SSO service and recognizes that the user’s tenant is configured to use Seamless SSO. Of Axure AD identifies the Seamless SSO configurations, it redirects the user’s browser to Autologon.
When the user tries accessing the Azure AD, Autologon tries to authenticate to Azure AD with the provided credentials. If the authentication is successful, then Autologon issues the DesktopSSOToken access token and sends it to Azure AD. If else, Autologon generates one of these errors (Error Code Table).
| Error code | Explanation |
| AADSTS50034 | The user does not exist |
| AADSTS50053 | The user exists and the correct username and password were entered, but the account is locked |
| AADSTS50056 | The user exists but does not have a password in Azure AD |
| AADSTS50126 | The user exists, but the wrong password was entered |
| AADSTS80014 | The user exists, but the maximum Pass-through Authentication time was exceeded |
Table 1. Autologon error codes.
These error codes are developed to know the cause of the problem. However, attackers utilize these error codes to discover the account information. The real threat lics in the logging information. As per the design, successful authentication events generate sign-in logs in step 2. Autologon authentication to Azure AD is not logged. This means initial login attempts are not logged. However, Autologon authentication failure events are logged. This feature allows the attacker to carry out the brute-force covering under the radar. This flaw could create a massive disruption if attackers could find the correct combination of username and password. For organizations, It is important to know how to protect Azure AD (Active Directory) from undetected brute-force attacks.
How To Protect Azure Active Directory From Undetected Brute-Force Attacks?
Logs are the main source to examine the activities of a system. Logs play a vital role in the analysis of incidents. Since there are no login attempt logs were generated, it is highly difficult to detect brute-force attacks. Since this flaw is by design. There are no clear mitigations to address this flaw. This has to be fixed only at the Vendor level. By the way, Microsoft has responded to this flaw and working to implement these things with the release of monthly patching updates.
Microsoft has published that it will enable logging to the Seamless SSO endpoint to ensure everything will be logged. After Microsoft enables the Seamless SSO logging, all the authentication and authorization successful and failed events can be recorded and revived later if needed. This enables the administrator or security team to quickly detect and react to brute-force attacks.
Microsoft is going to add the ability to have the Seamless SSO endpoint on/off. This feature offers tenants to enable Seamless SSO the time they require and keep it off by default.
The above two updates can defend the Azure AD from such brute-force password spray attacks. However, they can’t completely prevent the attacks. It’s the tenant’s responsibility that how efficiently they manage Seamless SSO and authentication logs.There are some best practices. Such cyber-attacks can be prevented by following them.
Enable Dynamic Banned Password: This is the best and cost-effective method to prevent brute-force attacks. Strong password describes the frequency of passwords being guessed, phished, and stolen. Enable Azure AD’s dynamic banned password feature. This feature prevents users from setting weak passwords.
Enable Password Hash Sync: This feature helps in identifying the compromised or leaked credentials.
Azure AD Smart Lock Out: AD FS Smart Extranet lockout protects against brute force attacks.
Block legacy authentication: It reduces security risk with an advanced security evaluation.
Implement Azure AD Privileged Identity Management: It optimizes account privileges with roles.
Implement sign-in risk policy: The policy will help in evaluating the security risk of a specific user or group.
Multi-factor Authentication: MFA is the next best solution against credential harvesting attacks.
Monitor Azure AD Identity Protection events: It’s a native Azure tool to detect potential vulnerabilities affecting an organization’s identities. The tool helps to detect leaked credentials, login attempts from different geo locations, sign-ins from infected devices, anonymous IP addresses, and unknown locations.
We hope this post would help you in protecting Azure AD (Active Directory) from undetected brute-force attacks. Thanks for reading this threat post. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.