Table of Contents
What Is Command Injection Vulnerability? And How To Prevent It?
Attackers usually target the system, server, or trusted infrastructure of an application. According to the OWASP, injection attacks are the most common web application security risks. Command injection is the most popular type of injection attack. In a command injection vulnerability, attackers change the application’s default function that usually executes commands of the system.
This article will discuss command injection vulnerability, how it works, its impacts, and ways to prevent it. Let’s get started.
What Is Command Injection Vulnerability?
Command injection is a type of attack in which the attacker injects malicious code into a legitimate command or query, in order to execute unauthorized actions on a system. This can be done either by manipulating the input data provided to the command (such as via user input) or by exploiting vulnerabilities in the way the command interprets and processes this data.
Command injection attacks are particularly dangerous because they can often be carried out without any prior knowledge of the system or even any authentication credentials. Moreover, once an attacker has successfully injected malicious code into a legitimate command, they can potentially gain full control over the system.
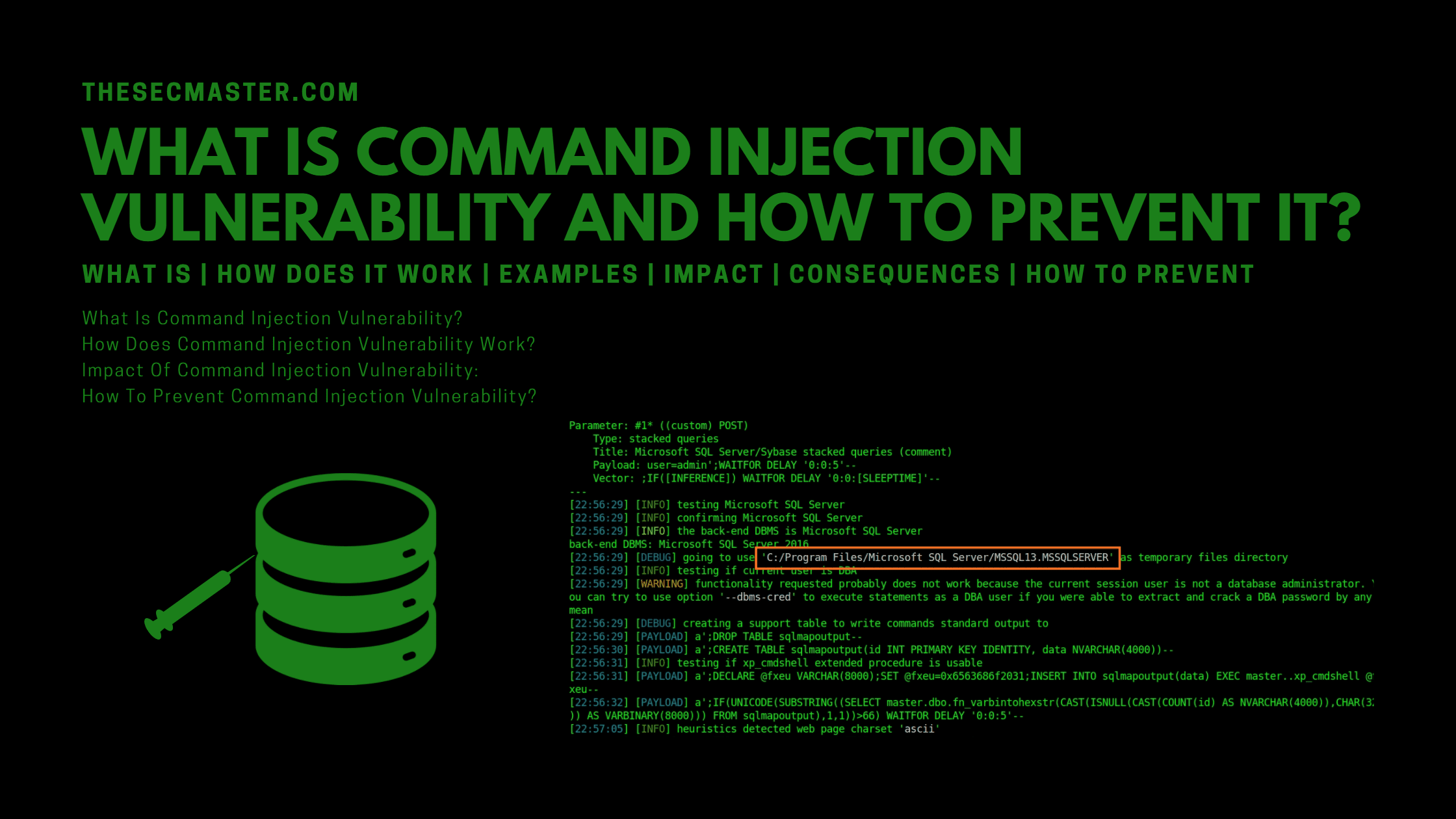
There are a number of ways in which attackers can carry out command injection attacks, but one of the most common is known as “SQL injection.” In a SQL injection attack, the attacker injects malicious code into an SQL query in order to execute unauthorized actions on the database.
A command injection attack can occur due to the following vulnerabilities.
XML external entity injection (XXE)
Insecure deserialization
Arbitrary file inclusion
Server-side template injection
How Does Command Injection Vulnerability Work?
Command injection vulnerability works in the following steps.
Step 1: In the first step, threat actors find vulnerabilities in applications that allow them to inject malicious commands.
Step 2: The attackers append a malicious command to the legitimate command that causes the execution of the desired action. Attackers usually use input mechanisms like cookies, form fields, or HTML code to inject these commands into the application.
Step 3: The system or application interprets the command and then translates it to the. Attackers execute particular commands on the infected system.
Example
Attackers add the semicolon and execute the arbitrary OS command to escape the ping command.
<?php
$ip = $_POST['ip'];
$cmd = system('ping '.$ip);
echo $cmd
?>Example input: ; cat /etc/passwd
To ensure command injection vulnerability in your web application, you need to validate user input and allow only required commands for the task. You can also clean the user input by removing special characters like a semicolon;
and other shells like &, &&, |, ||, <.Impact Of Command Injection Vulnerability:
Command injection vulnerabilities can be difficult to detect and exploit, making them a serious threat to businesses and individuals alike. It is often considered a high severity vulnerability due to the wide-ranging impact it can have on an organization. Many popular web applications and devices are vulnerable to command injection, which makes this type of attack relatively easy to carry out.
Some Consequences Of Command Injection Vulnerability are:
An attacker can execute arbitrary code on the target system, which can lead to a complete compromise of the system.
An attacker can gain access to sensitive information stored on the target system.
An attacker can Denial of Service (DoS) the target system by injecting malicious commands that consume all available resources.
An attacker can manipulate data stored on the target system, which can lead to incorrect results or data loss.
An attacker can redirect network traffic from the target system to another system under their control, allowing them to intercept and view confidential data.
An attacker can use command injection to pivot and attacking other systems on the same network as the vulnerable system.
Command injection can be used to bypass security controls such as firewalls and intrusion detection/prevention systems (IDS/IPS).
How To Prevent Command Injection Vulnerability?
Here are some common ways to prevent command injection vulnerability.
Sanitize user input: Make sure to properly validate and cleanse all user input before using it in shell commands.
Use parameterized queries: Use prepared statements with bound parameters instead of dynamically building up shell commands from user input.
Escape special characters: Properly escape all special characters in user input before using it in shell commands.
Disable command execution: Disable the ability to execute shell commands altogether if possible.
Use a web application firewall: use a WAF to help protect against command injection attacks.
Validate user input: Always validate user input to ensure that it is what you expect and is within the bounds of what is allowed.
Use a whitelist approach: Only allow input that matches a whitelist of known andexpected values.
Disabling dangerous functions and commands: Many shells provide built-in functions that can be used to execute commands. These functions should be disabled if not needed, or properly restricted if they are needed.
Use least privilege: Always run shell commands with the least amount of privileges necessary. This will help limit the damage that can be done if a command injection vulnerability is exploited.
Logging and monitoring: Properly log all shell commands that are executed, and monitor these logs for suspicious activity. This can help give you visibility into what is happening on your systems and help detect potential command injection attacks
Checking for malicious input: Always check user input for malicious content before passing it to any system command. This includes things like checking for illegal characters, attempting to execute commands, and more.
Updating and patching: Keep your systems up-to-date with the latest security patches and updates.
Implement security measures at the application level: In addition to implementing security measures at the operating system level, it is also important to implement security measures at the application level. This can help to further protect your systems against command injection attacks.
Educate your users: One of the best ways to help prevent command injection attacks.
We hope this post will help you know what is Command Injection Vulnerability and how to protect from it. Thanks for reading this post. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.