Table of Contents
Deploy and Configure Universal Forwarder on a Windows Machine
The Universal Forwarder in a Splunk environment is a component designed to collect machine data from almost any device, including Windows systems. This lightweight version of Splunk is optimized for gathering logs and forwarding them to a Splunk indexer for further processing and analysis.
In this tutorial, we will guide you through the steps to install and configure the Universal Forwarder on a Windows machine. Additionally, we will cover how to install the Windows Add-on and configure it to collect various types of logs from your Windows machine.
By the end of this tutorial, you will be able to:
Create an Index for Windows to store and index on Indexer machine
Install the Splunk Universal Forwarder on a Windows machine
Configure the Universal Forwarder to forward logs to a Splunk Indexer
Install and configure the Windows Add-on to collect specific types of logs
Verify that the logs are being successfully collected and indexed by Splunk
This tutorial assumes that you have a basic understanding of Splunk and its components. If you're new to Splunk, consider reading the Splunk Getting Started Guide before proceeding.
Lab Setup
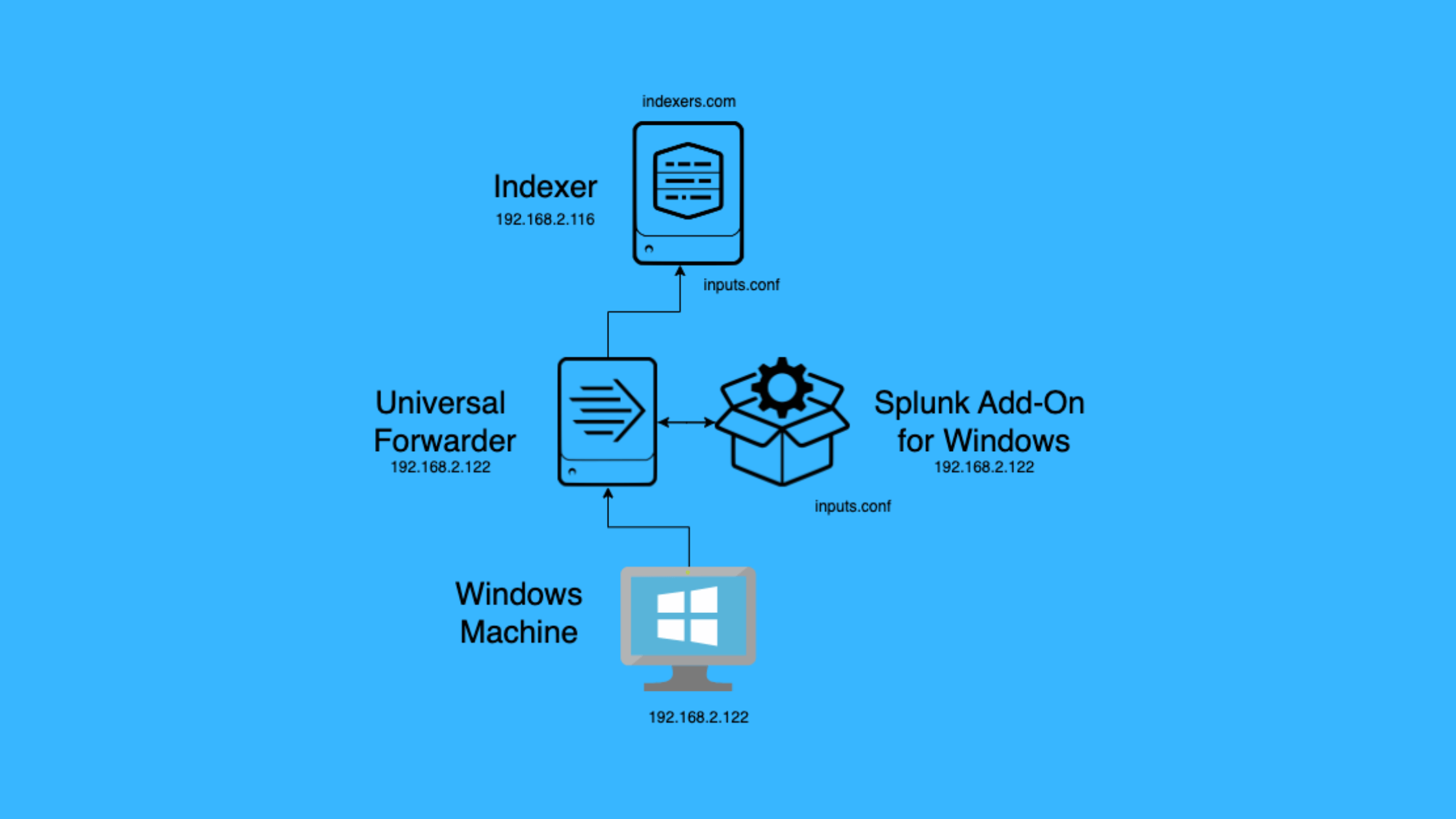
For this tutorial, we will be using a simple lab setup consisting of two machines: a Mac and a Windows machine. The Splunk Indexer instance is deployed on the Mac, while the Universal Forwarder will be installed on the Windows machine, which serves as our log source.
The diagram above illustrates the lab setup, with the Universal Forwarder on the Windows machine will collect logs and forward them to the Splunk Indexer running on the Mac. This configuration allows for centralized log collection and analysis, making it easier to monitor and troubleshoot issues across your environment.
To follow along with this tutorial, you will need:
A Mac or Linux machine with a running Splunk Indexer instance (version 8.x or later)
A Windows machine (Windows 7 or later) to install the Universal Forwarder
Network connectivity between the two machines
If you haven't already set up your Splunk Indexer on the Mac or Linux, refer to the Splunk Installation Manual for detailed instructions on installing and configuring Splunk Enterprise.
In the next section, we will walk through the process of installing the Splunk Universal Forwarder on your Windows machine and configuring it to send logs to the Indexer.
In case, if you want to deploy Universal Forwarder on a Linux or Mac refer these two tutorials:
Configuration Overview
Before diving into the configuration of the Universal Forwarder and Indexer instances, let's take a moment to outline the steps we'll be taking on each machine.
Splunk Indexer Configuration (Mac)
1. Create a new App named "windows_logs_app" to keep our configurations organized and separate from other Splunk configurations.
2. Create a new index named "windows_logs" within the "windows_logs_app" to store the logs collected from the Windows machine.
3. Configure the inputs.conf file within the "windows_logs_app" to receive the logs forwarded by the Universal Forwarder.
Windows Machine Configuration
1. Download and install the Splunk Universal Forwarder on the Windows machine.
2. Download and install the Splunk Add-on for Windows to enable the collection of specific Windows log types.
3. Configure the inputs.conf file in the Splunk Add-on for Windows to specify which log types should be collected and forwarded to the Indexer.
By creating a dedicated App and index on the Splunk Indexer, we ensure that our Windows log data remains separate from other data sources, making it easier to manage and search. The inputs.conf configuration on the Indexer will specify the port and index to receive the logs from the Universal Forwarder.
On the Windows machine, the Universal Forwarder acts as the log collection agent, while the Splunk Add-on for Windows provides the necessary configuration files and parsing logic to collect specific Windows log types. By configuring the inputs.conf file within the Add-on, we can selectively collect the logs that are relevant to our use case.
In the following sections, we will walk through the detailed steps for configuring both the Splunk Indexer and the Windows machine to establish a robust log collection and forwarding pipeline.
Recommendations from the author: Read these articles before you start this article.
Configuring the Splunk Indexer
You already know what we will do in the Indexer from our previous section. Well, in this section, we will walk through the process in step by step way.
Step 1: Create a new App
Log in to your Splunk Web UI on the Mac.
Navigate to "Settings" > "Applications" and click on "Create app".
Enter "windows_logs_app" as the App name and provide a description (optional).
Click "Save" to create the new App.
From CLI:
ls -l /Applications/splunk/etc/appsWe published a dedicated articles on managing Apps and Add-ons, we recommend to refer for more detail.
Step 2: Create a new index
1. Within the Splunk Web UI, navigate to "Settings" > "Indexes".
2. Click on "New Index" and enter the following details:
- Index Name: windows_logs
- App: windows_logs_app
- Max Size: 500 MB (you can adjust this based on your requirements)
3. Click "Save" to create the new index.
Alternatively, you can create the index by editing the indexes.conf file directly:
1. Open a terminal on your Mac and navigate to $SPLUNK_HOME/etc/apps/windows_logs_app/local/.
2. Create a new file named indexes.conf (if it doesn't exist) and add the following content:
[windows_logs]
homePath = $SPLUNK_DB/windows_logs/db
coldPath = $SPLUNK_DB/windows_logs/colddb
thawedPath = $SPLUNK_DB/windows_logs/thaweddbSave the file and restart the Splunk Indexer.
Note: If you don't see the index on the Web UI console. Reload the configuration visiting this URL: "https://splunk_server:8000/debug/refresh". We covered creating Indexes in detail on a different article. We recommend to refer for more details.
Step 3: Configure inputs.conf
1. In the Splunk Web UI, navigate to "Settings" > "Forwarding and Receiving".
2. Click on "Configure Receiving" and then "New Receiving Port".
3. Enter the following details:
- Port: 10997 (or any available port of your choice. Ensure post no is not in conflict with other services)
4. Click "Save" to save the configuration.
Alternatively, you can configure inputs.conf directly from CLI:
1. Open a terminal on your Mac and navigate to $SPLUNK_HOME/etc/apps/windows_logs_app/local/.
2. Create a new file named inputs.conf (if it doesn't exist) and add the following content:
[splunktcp://10997]
index = windows_logs
disabled = 0Save the file and restart the Splunk Indexer.
Your Splunk Indexer is now configured to receive logs from the Universal Forwarder on the specified port and index them in the "windows_logs" index within the "windows_logs_app".
We published a dedicated articles on configuring indexes.conf file, we recommend to refer for more detail.
In the next section, we will configure the Universal Forwarder on the Windows machine to collect and forward logs to the Splunk Indexer.
Deploying the Universal Forwarder on Windows
Let's come to the source side configuration. let's see how to set up the Universal Forwarder on your Windows machine in detail.
Step 1: Download and Install the Splunk Universal Forwarder
Visit the Splunk Universal Forwarder download page.
Select "Windows" as the platform and choose the appropriate CPU architecture (32-bit or 64-bit) for your Windows machine.
Click "Download" and save the installer file.
Double-click the downloaded installer file and follow the installation wizard:
Accept the license agreement. Choose the Splunk Indexer instance (Cloud or On-Premises).
Provide Username and Password for UF administrator.
Provide the host mane or IP address and listening port number of the Splunk Deployment Server. Leave blank if you don't have a Deployment Server.
Provide the host mane or IP address and listening port number of the Splunk Indexer.
Install Universal Forwarder.
Finish the installation.
Splunk Universal Forwarder installed in C:\Program Files\SplunkUniversalForwarder directory.
Check the Status of Universal Forwarder service.
If your configurations and network ncommunication between your Indexer and Universal Forwarder are good. Your UF will start reporting to the Indexer. Verify the Windows Universal Forwarder is reporting to the Indexer. To do that, Search this query on the Search app. If you see your Windows Hostname in the search result, your Universal Forwarder is started reporting to the Indexer.
index=_internal | stats count by hostSince, we can see our Windows host name in the search results, we can conclude the installation of Universal Forwarder is complete.
If you try searching for the logs from the Windows machine, you don't see anything at this point in time. Since, you haven't configured the log collection. You will have to configure the inputs.conf to collect the logs.
Well, you can configure the inputs.conf under the C:\Program Files\SplunkUniversalForwarder\etc\system\local directory or C:\Program Files\SplunkUniversalForwarder\etc\apps\<your_app>\local\. However, we recommend to install the Splunk Add-On for Windows add-on, which comes with preconfigured inputs.conf file with multiple configuration options and log parsers. This makes both Splunk's and our life easier. Let's see how to download and install Splunk Add-On for Windows in the next step.
Step 2: Download and Install the Splunk Add-on for Windows
Download the Splunk Add-on for Windows from Splunkbase.
Click the "Download" button on the add-on's page.
Log in to your Splunk account or create a new one if prompted.
Agree to the terms and conditions and click "Download".
Unzip the downloaded file and copy the directory 'Splunk_TA_windows' to C:\Program Files\SplunkUniversalForwarder\etc\apps\.
This completes the installation of Splunk Add-on for Windows.
Note: You can't see the local directory inside this Add-On. You will have to configure the preexisting configuration files under the default directory. Which we will configure in the next section.
Step 3: Configure inputs.conf in the Splunk Add-on for Windows
Open File Explorer and navigate to the directory where the Splunk Add-on for Windows is installed (default: C:\Program Files\SplunkUniversalForwarder\etc\apps\Splunk_TA_windows\default).
Look for a file named inputs.conf.
Open the inputs.conf file using a text editor (e.g., Notepad). Enable the desired log types by setting disabled = 0 for the stanza you need to enable. Each stanza represents a log type.
Also, it is important to add the index for each stanza to direct the Universal Forwarder to store and index the logs in a specific Index.
Example:
To enable the Security logs go the the [WinEventLog://Security] stanza and set the value of disabled to 0 and add index = windows_logs at the end of that stanza.
[WinEventLog://Security]
disabled = 0
start_from = oldest
current_only = 0
evt_resolve_ad_obj = 1
checkpointInterval = 5
blacklist1 = EventCode="4662" Message="Object Type:(?!\s*groupPolicyContainer)"
blacklist2 = EventCode="566" Message="Object Type:(?!\s*groupPolicyContainer)"
renderXml=true
index = windows_logsAfter enabling the logs of your choice. Restart the Splunk Forwarder service. Tat's it.
If you follow all the steps, your Universal Forwarder will start collecting and forwarding the logs to the Indexer.
Verify the Logs on the Indexer or Search Head
Let's take a look at some of the networks and processes running on the Windows machine.
Local network address of the machine:
2. Local Port opened:
3. Processes running on the host:
You can also see, remote address, remote host name, remote protocol, and more.
We hope this article helps understand how to deploy Universal Forwarder on a Windows machine and configure it to send logs to the indexer.
That's all for now, we will cover more informative topics about Splunk in the upcoming articles. Please keep visiting thesecmaster.com for more such technical information. Visit our social media page on Facebook, Instagram, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive information like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.