Table of Contents
What are Splunk Receivers and Forwarders? How to Create and Delete Receivers and Forwarders in Splunk via the Web UI and CLI?
Welcome to another important topic in the world of Splunk: Receivers and Forwarders. These components are pivotal in managing the data inputs and outputs within Splunk's architecture. If you're familiar with the phases of the Splunk data pipeline—Data Input, Data Store, and Data Search—or the Event Processing Tiers, then you know we're focusing on the Data Input and Output phase in this post.
In this article, we'll dive into some essential questions about the receiving and forwarding processes in Splunk. You'll learn what receivers and forwarders are, how they operate, and how to manage them. We'll cover both the web UI and command line interface (CLI) methods to create and delete Receivers and Forwarders, ensuring you have the practical knowledge to handle these tasks efficiently. Let’s get started on understanding these crucial elements that help Splunk efficiently process and forward data.
By the end of this post, you will have a solid understanding of these essential components and the skills to manage them effectively in your Splunk environment.
What is a Splunk Receiver?
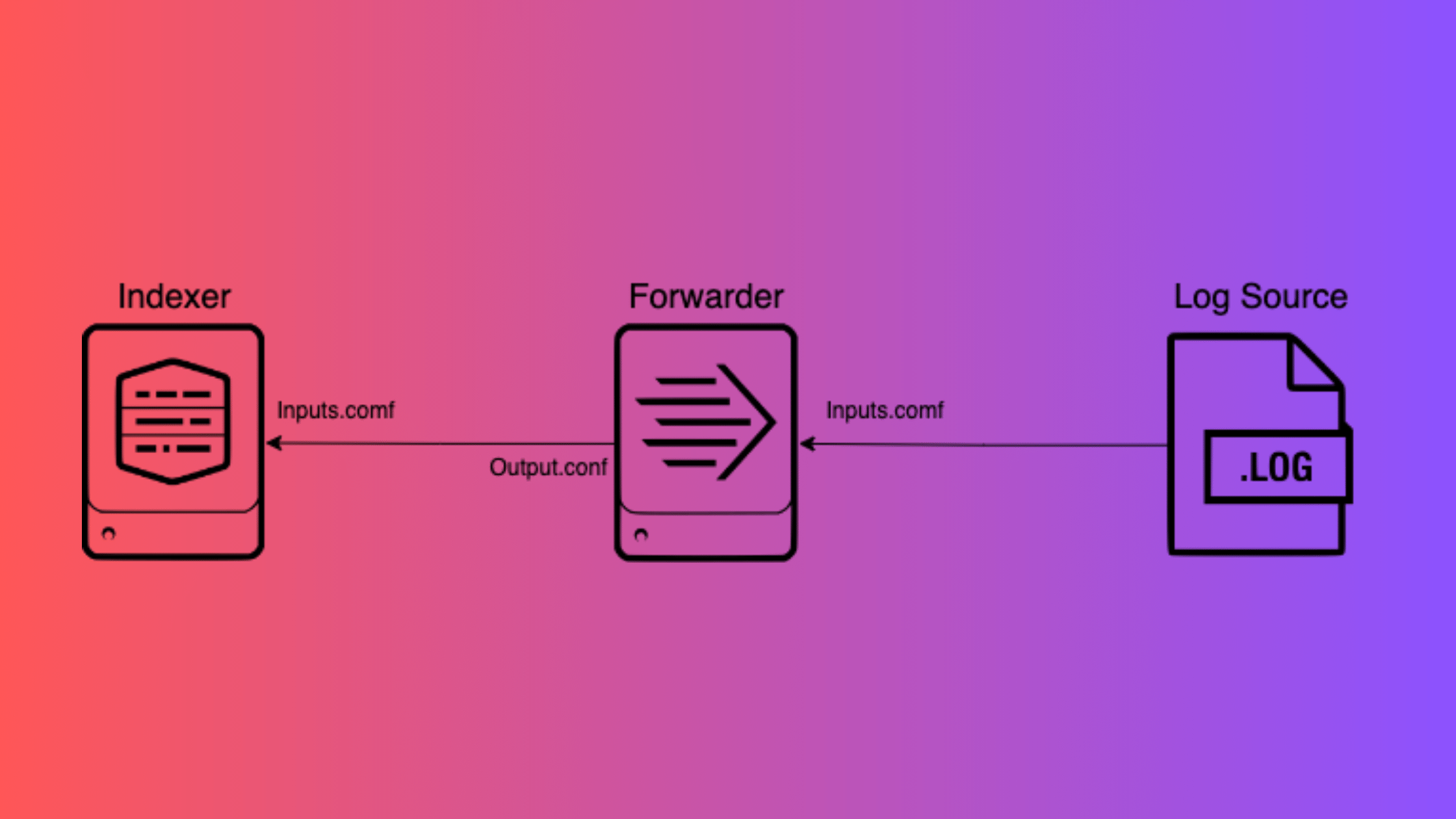
A Splunk Receiver is a critical component in the Splunk architecture that enables the system to receive and ingest data from various sources. It acts as an entry point for data to flow into Splunk, allowing you to collect, process, and analyze data efficiently. Receivers are configured using the inputs.conf file, which defines the settings and parameters for each data input.
Location: The inputs.conf file resides in the `$SPLUNK_HOME/etc/system/local/` directory. If you need more granular control per app or environment, you might place it in `$SPLUNK_HOME/etc/apps/<AppName>/local/`.
To configure a Splunk Receiver in the inputs.conf file, you need to specify the type of data input and the corresponding settings. The general format for configuring a receiver in the inputs.conf file is as follows:
[<input_type>://<input_name>]
<setting1> = <value1>
<setting2> = <value2>
...Here, <input_type> represents the type of data input, such as tcp, udp, http, or splunktcp. The <input_name> is a unique identifier for the specific input configuration. The subsequent lines define the settings and their corresponding values for the receiver.
Example:
[udp://514]
connection_host = ip
sourcetype = syslog
no_appending_timestamp = true This configuration tells Splunk to listen on UDP port 514 for incoming syslog data, treating each data source as a separate host.
Splunk supports various types of data streams that can be received through the inputs.conf file. Some common data input types include:
1. TCP (Transmission Control Protocol): Splunk can receive data over TCP, which is a reliable, connection-oriented protocol. To configure a TCP receiver, you would use the [tcp://<port>] stanza in the inputs.conf file, specifying the port number on which Splunk should listen for incoming data.
2. UDP (User Datagram Protocol): Splunk can also receive data over UDP, which is a connectionless protocol. To set up a UDP receiver, you would use the [udp://<port>] stanza in the inputs.conf file, specifying the port number for incoming UDP data.
3. HTTP (Hypertext Transfer Protocol): Splunk provides the ability to receive data via HTTP or HTTPS. To configure an HTTP receiver, you would use the [http://<port>] or [https://<port>] stanza in the inputs.conf file, depending on whether you want to use plain HTTP or secure HTTPS.
4. Splunk TCP (Splunk-to-Splunk Communication): Splunk has its own proprietary protocol called Splunk TCP, which is optimized for efficient data transfer between Splunk instances. To set up a Splunk TCP receiver, you would use the [splunktcp://<port>] stanza in the inputs.conf file.
In addition to these common data input types, Splunk also supports other input methods, such as file monitoring, scripted inputs, and modular inputs. These input types allow you to collect data from various sources and integrate Splunk with external systems and applications.
When configuring a Splunk Receiver, it's essential to consider factors such as data format, security, and performance. You can specify settings like the source type, index, and time stamping behavior for each input. Additionally, you can configure authentication, encryption, and access controls to ensure the security of your data during transmission and ingestion.
Splunk Instances Where inputs.conf file Can be Configured
The inputs.conf file can be configured on various Splunk instances to define data inputs and their respective settings.
1. Splunk Indexer: You can configure data inputs on the indexer to receive data directly from sources or from Splunk Forwarders. The inputs.conf file on the indexer defines the input settings for the data sources it receives.
2. Splunk Heavy Forwarder: You can configure the inputs.conf file on a Heavy Forwarder to specify the data inputs and their settings. The Heavy Forwarder then processes and forwards the data to the indexers based on the configured rules.
3. Splunk Universal Forwarder: You can configure the inputs.conf file on the Universal Forwarder to define the data inputs and their settings. The Universal Forwarder then sends the data to the specified destination based on the configuration.
It's important to note that the specific Splunk instance where you configure the inputs.conf file depends on your Splunk architecture and data flow requirements. In a distributed Splunk deployment, you typically configure data inputs on the Forwarders (Universal or Heavy) and the Indexers. The Forwarders collect data from the sources and send it to the Indexers, while the Indexers receive and store the data for searching and analysis.
What is a Splunk Forwarder?
In the Splunk architecture, a forwarder is the component responsible for collecting logs, data streams, or other telemetry from various sources and forwarding it to a Splunk deployment for indexing and analysis. The most common type of forwarder is the Universal Forwarder (UF), which is lightweight, easy to install, and designed for high-performance data collection and forwarding with minimal impact on system resources.
Configuring a Splunk Forwarder
To configure a Splunk Forwarder, you need to modify the outputs.conf file, which defines the settings and destinations for data forwarding. The outputs.conf file specifies where and how the Forwarder should send the data.
Location: The `outputs.conf` file is typically located in `$SPLUNK_HOME/etc/system/local/`, although it can also be placed in `$SPLUNK_HOME/etc/apps/<AppName>/local/` for app-specific configurations.
Here's an example of configuring a Splunk Forwarder in the outputs.conf file:
[tcpout]
defaultGroup = my_forwarder_group
[tcpout:my_forwarder_group]
server = splunk_receiver.example.com:9997
[tcpout-server://splunk_receiver.example.com:9997]
connectionTimeout = 10
sendCookedData = trueIn this example, we define a TCP output group called my_forwarder_group under the [tcpout] stanza. The defaultGroup setting specifies the default output group to be used for forwarding data.
Next, we configure the my_forwarder_group by specifying the destination server and port under the [tcpout:my_forwarder_group] stanza. In this case, the Forwarder will send data to splunk_receiver.example.com on port 9997.
Finally, we provide additional settings for the specific destination server under the [tcpout-server://splunk_receiver.example.com:9997] stanza. Here, we set the connectionTimeout to 10 seconds, specifying the maximum time the Forwarder should wait for a connection to be established. We also set sendCookedData to true, indicating that the Forwarder should send processed and formatted data to the receiver.
Splunk Instances Where Outputs.conf file Can be Configured
The outputs.conf file is used to configure data forwarding and output settings in Splunk. It defines where and how the data should be sent from a Splunk instance to another Splunk instance or an external system.
1. Splunk Universal Forwarder: You can configure the outputs.conf file on the Universal Forwarder to specify the destination(s) where the data should be sent. This can include Splunk Indexers, Heavy Forwarders, or even non-Splunk systems.
2. Splunk Heavy Forwarder: You can configure the outputs.conf file on a Heavy Forwarder to define the data forwarding rules and destinations. The Heavy Forwarder can send data to Splunk Indexers, other Forwarders, or external systems based on the configured output settings.
3. Splunk Indexer: In some scenarios, you may need to configure data forwarding directly on a Splunk Indexer. Although the primary role of an Indexer is to index and store data, it can also forward data to other Splunk instances or external systems. You can configure the outputs.conf file on the Indexer to define the data forwarding settings and destinations.
It's important to note that the specific Splunk instance where you configure the outputs.conf file depends on your Splunk architecture and data flow requirements. In a distributed Splunk deployment, you typically configure data forwarding on the Forwarders (Universal or Heavy) to send data to the Indexers or other destinations. The Indexers can also forward data to other Splunk instances or external systems if needed.
How to Create and Delete Receivers and Forwarders in Splunk via the Web UI?
Managing receivers and forwarders in Splunk via the Web UI is a straightforward process, allowing for easy setup and maintenance directly from your browser. Here’s how you can create and delete these components without needing to directly edit configuration files.
Creating a Receiver in Splunk Web UI
To set up a receiver in Splunk, you typically configure a Splunk instance to accept incoming data. Here's how to enable receiving from the Splunk Web interface:
1. Start by logging into the Splunk Web on the instance you want to configure as a receiver.
2. Go to `Settings > Forwarding and receiving`.
3. Click on `Configure receiving`.
4. Select `New Receiving Port`.
5. Enter the port number on which this receiver will listen for incoming data. The default port is `9997`.
6. Click `Save` to enable the receiver.
Your Splunk instance is now set up to receive data from forwarders configured to send data to this port.
Creating a Receiver in Splunk Web UI
In additions to the creating Receivers in the above method, In this section, we will walk you through the other way of creating Receivers in Splunk.
Log in to the Splunk Web UI using your credentials.
Once logged in, click on the "Settings" menu in the top navigation bar.
From the dropdown menu, select "Add Data".
On the "Add Data" page, you will see various options for data sources.
Click on the "Monitor" tab to create a Receiver for data inputs.
Under the "Monitor" tab, you will find different Receiver types such as "Files & Directories", "HTTP Event Collector", "TCP/UDP", etc.
Choose the appropriate Receiver type based on your requirements. For example, let's select "TCP/UDP".
Configure the Receiver Settings
After selecting the Receiver type, you will be prompted to configure the Receiver settings.
Provide a unique name, port number, and the name of the Receiver.
Select the appropriate source type for the incoming data from the list and follow the instructions to create the Receiver.
By following these steps, you can easily create a Receiver in Splunk. The "Add Data" options provide a user-friendly interface to configure and manage Receivers for various data inputs.
Creating a Forwarder in Splunk Web UI
While detailed forwarder setup typically involves installation steps on the forwarder machine itself, you can manage some aspects via the Web UI, especially in distributed environments:
1. From the Splunk Web interface of your deployment server, navigate to `Settings > Forwarding and receiving`.
2. Click on `New Forwarding Host` to configure a new forwarder. You will need to input details such as the forwarder's hostname or IP address.
3. Assign the forwarder to a server class which contains the configurations it should receive.
Deleting a Receiver or Forwarder in Splunk Web UI
If you need to remove a receiver or stop a forwarder from sending data to your Splunk instance, you can also manage this from the Web UI.
Deleting a Receiver or Forwarder
1. Go to `Settings > Forwarding and receiving`.
2. Click on `Configure receiving` or `Configure forwarding`.
3. Find the receiver or forwarder you wish to delete and click `Delete` next to the respective port number.
These procedures ensure you can effectively manage your data flow within Splunk, keeping your environment optimised and secure.
How to Create and Delete Receivers and Forwarders in Splunk via CLI?
Managing Splunk receivers and forwarders can also be done effectively using the Command Line Interface (CLI), which provides a powerful way to automate tasks and perform configurations that might be repetitive or complex via the Web UI. Here’s a detailed guide to creating and deleting receivers and forwarders via the CLI.
Creating a Receiver in Splunk via CLI
To create a Receiver in Splunk via the CLI, follow these steps:
1. Open a terminal or command prompt and navigate to the Splunk installation directory: $SPLUNK_HOME/.
In Linux:
cd /opt/splunk/In mac:
cd /Applications/splunk/Run the following command to create a receiver:
./bin/splunk add input <input_type> -port <port_number> -sourcetype <source_type> -index <index_name>1. Replace <input_type> with the type of Receiver you want to create (e.g., tcp, udp, http), <port_number> with the desired port number, <source_type> with the source type for the incoming data, and <index_name> with the target index.
2. Save the changes and exit the CLI.
3. Restart Splunk for the changes to take effect:
./bin/splunk restartDeleting a Receiver in Splunk via CLI
To delete a Receiver in Splunk via the CLI, follow these steps:
1. Open a terminal or command prompt and navigate to the Splunk installation directory: $SPLUNK_HOME/.
2. Run the following command to delete a Receiver:
./bin/splunk remove input <input_type>://<port_number>1. Replace <input_type> with the type of Receiver you want to delete (e.g., tcp, udp, http) and <port_number> with the associated port number.
2. Save the changes and exit the CLI.
3. Restart Splunk for the changes to take effect:
./bin/splunk restartThe Receiver will now be deleted, and Splunk will stop listening for incoming data on the associated port.
Creating a Forwarder in Splunk via CLI
To create a Forwarder in Splunk via the CLI, follow these steps:
1. Open a terminal or command prompt and navigate to the Splunk installation directory: $SPLUNK_HOME/.
2. Run the following command to create a Forwarder:
./bin/splunk add forward-server <server_name>:<port_number>1. Replace <server_name> with the hostname or IP address of the destination Splunk instance or external system, and <port_number> with the desired port number.
2. Configure additional Forwarder settings if needed, such as data filtering or routing rules.
3. Save the changes and exit the CLI.
4. Restart Splunk for the changes to take effect
./bin/splunk restartSplunk will now start forwarding data to the specified destination based on the configured Forwarder settings.
Deleting a Forwarder in Splunk via CLI
To delete a Forwarder in Splunk via the CLI, follow these steps:
1. Open a terminal or command prompt and navigate to the Splunk installation directory: $SPLUNK_HOME/.
2. Run the following command to create a Forwarder:
./bin/splunk remove forward-server <server_name>:<port_number>1. Replace <server_name> with the hostname or IP address of the destination Splunk instance or external system, and <port_number> with the associated port number.
2. Save the changes and exit the CLI.
3. Restart Splunk for the changes to take effect:
./bin/splunk restartThe Forwarder will now be deleted, and Splunk will stop forwarding data to the associated destination.
Remember to carefully plan and configure your Receivers and Forwarders based on your data collection and forwarding requirements. Consider factors such as data sources, destinations, security, and performance when setting up your Splunk environment.
We hope this article helps understanding about the receiving and forwarding processes in Splunk. We covered creating and deleting indexes using both the Web UI and CLI, what receivers and forwarders are, how they operate, and how to manage them along with creating and deleting Receivers and Forwarders from both Web UI and CLI methods.
We are going to end this article for now, we will cover more information about the Splunk in the up coming articles. Please keep visiting thesecmaster.com for more such technical information. Visit our social media page on Facebook, Instagram, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive information like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.