Table of Contents
How To Export A Private Key File From A Windows Machine?
It is easy to locate and export a private key file on non-windows platforms. Both public and private keys will be created and saved in a separate file in .key or .pem extensions on non-windows platforms. However, Windows doesn’t store the private key in a separate file to view as a text file. you can’t export the private key alone. If you need to export the private key from either MMC or IIS, you should export the certificate in .pfx (PKCS#12) file format along with the private key. If this is the case, you may ask if it is not possible to export a private key file on the Windows platform. To answer this question, there is no direct way. However, there is a way. Let’s see how to export a private key file from a Windows machine.
Procedure To Export A Private Key File From Windows:
We have broken down the procedure into four sections to make it simple to understand.
Note: We have covered right from the beginning from creating a CSR to exporting the private key for those who need help in getting a certificate. If you have the certificate in your hand or it’s deployed on your Windows server, then you can skip the first three steps. You can start directly from the fourth step.
Create CSR.
Submit the CSR to a CA and get the Certificate.
Import the Certificate on your Windows machine.
Export the Certificate in PFX format.
Install OpenSSL on your Windows machine.
Export the private key file from the PFX certificate.
How To Export a Private Key File from a Windows Machine?
Step 1: Create a CSR
1. Open MMC console:
Win + R > mmc > Ok > File > Add/Remove Snap-in > Certificates > Add > Computer account > local computer > Finish > Ok.
2. Create a CSR file:right-click the Personal folder > All Tasks > Advanced Operations > Create Custom Request > Next > Proceed without enrollment policy > Click Next > PKCS # 10 > Next > Details > Properties.
3. Add CSR contents:
Subject tab > Fill Subject name
Common Name (CN) = Host or domain name
DNS (SAN) =
Organization (O) =
Organizational Unit (OU) =
City/Locality (L) =
State/County/Region (S) =
Country (C) =
Email Address =
Private Key tab > Key options > select Key size: 2048 > Ok
4. Save the CSR file:Select Base 64 and Click Next > Click Browse.
Please visit this post to see how to create a CSR on a Windows machine.
Step 2: Submit the CSR to a CA and get the Certificate
Submit the CSR to your Certificate Authority (CA) or you can also submit it to third party CA to sign the certificate.
If you have Microsoft’s ADCS CA service and want to sign the CSR with your internal CA. Please read how to submit and download the certificate from ADCS.
Step 3: Import the Certificate on your Windows machine
After CA has issued the certificate. You should download that and import it along with the chain certificates.
Note: If you don’t have the chain certificates imported to trusted stores, please import chain certificates (intermediate & root CA certificates) on your machine.
Right Click on the Certificate > Install Certificate > Next > Automatically select the certificate store > Finish > Ok
Step 4: Export the certificate in PFX format
This is the place where the export of the private key happens. Windows doesn’t store the private key in a separate file. you can’t export the private key alone. If you need to export the private key from either MMC or IIS, you should export the certificate in .pfx (PKCS#12) file format along with the private key.
1. Open MMC console:
Win + R > mmc > Ok > File > Add/Remove Snap-in > Certificates > Add > Computer account > local computer > Finish > Ok.
2. Export the certificate in PFX:
Right Click on the Certificate > All Tasks -> Export > Next > yes, export the private key > Next > Personal INformation Exchange – PKCS # 12 (PFX) > Include all certificate in the path > Next > Passwords > Browse > Finish.
Step 5: Install OpenSSL on your Windows machine.
OpenSSL is a powerful full cross-platform open-source utility used in various digital certificate activities? The installation procedure is very simple and straightforward. Read this post to learn how to install OpenSSL on a Windows machine.
1. Download the OpenSSL installer from the official OpenSSL download link: https://slproweb.com/products/Win32OpenSSL.html
2. Run the installer to complete the installation.
3. Add OPENSSL_CONF and Path environment variable on System Properties:
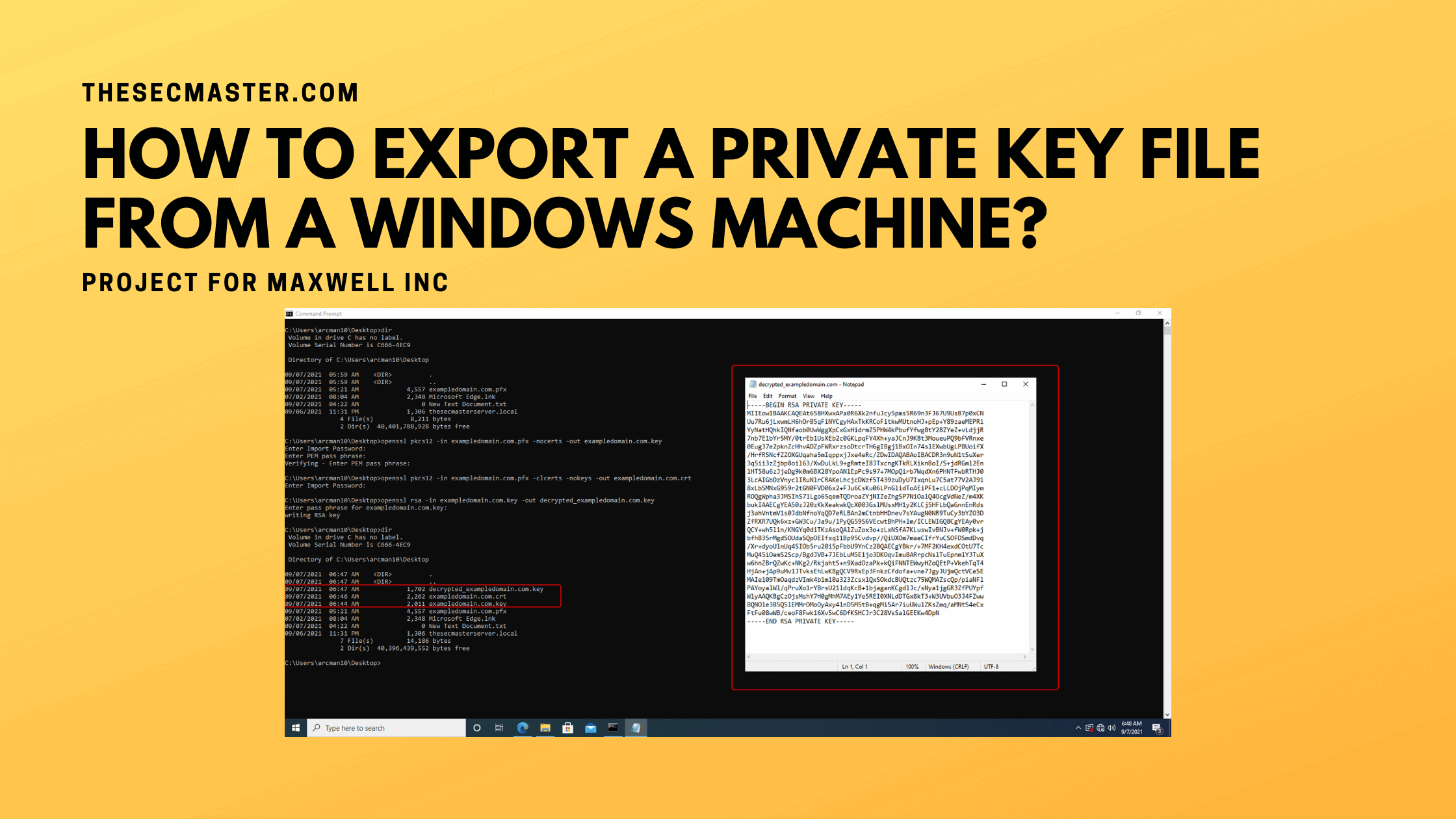
Step 6: Export the private key file from the PFX certificate.
Run this command to extract the private key from PFX file:
> openssl pkcs12 -in [yourfile.pfx] -nocerts -out [drlive.key]
Run this command to extract the certificate from PFX file:
> openssl pkcs12 -in [yourfile.pfx] -clcerts -nokeys -out [drlive.crt]
Run this command to decrypt the private key:
> openssl rsa -in [drlive.key] -out [drlive-decrypted.key]
In this way, you can export a private key file from the Windows machine.
Thanks for reading this post. Please let us know if you want to know more about this. We recommend reading the below post to know in detail.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.