Table of Contents
What Is Sender Policy Framework (SPF)? Why Do We Need SPF? How to Set up an SPF Record? How to Check an SPF Record?
The sender policy framework (SPF) is one of the email authentication protocols which helps the sender identify phishing emails and protect the organization from fraud.
In the previous article, we discussed what is email authentication and its importance. In this article, we will look into one of the main email authentication protocols Sender Policy Framework aka SPF. This article gives an in-depth view of what is SPF, why do we need SPF, how to set up an SPF record for your organization, and finally, how to check an SPF record.
What is SPF?
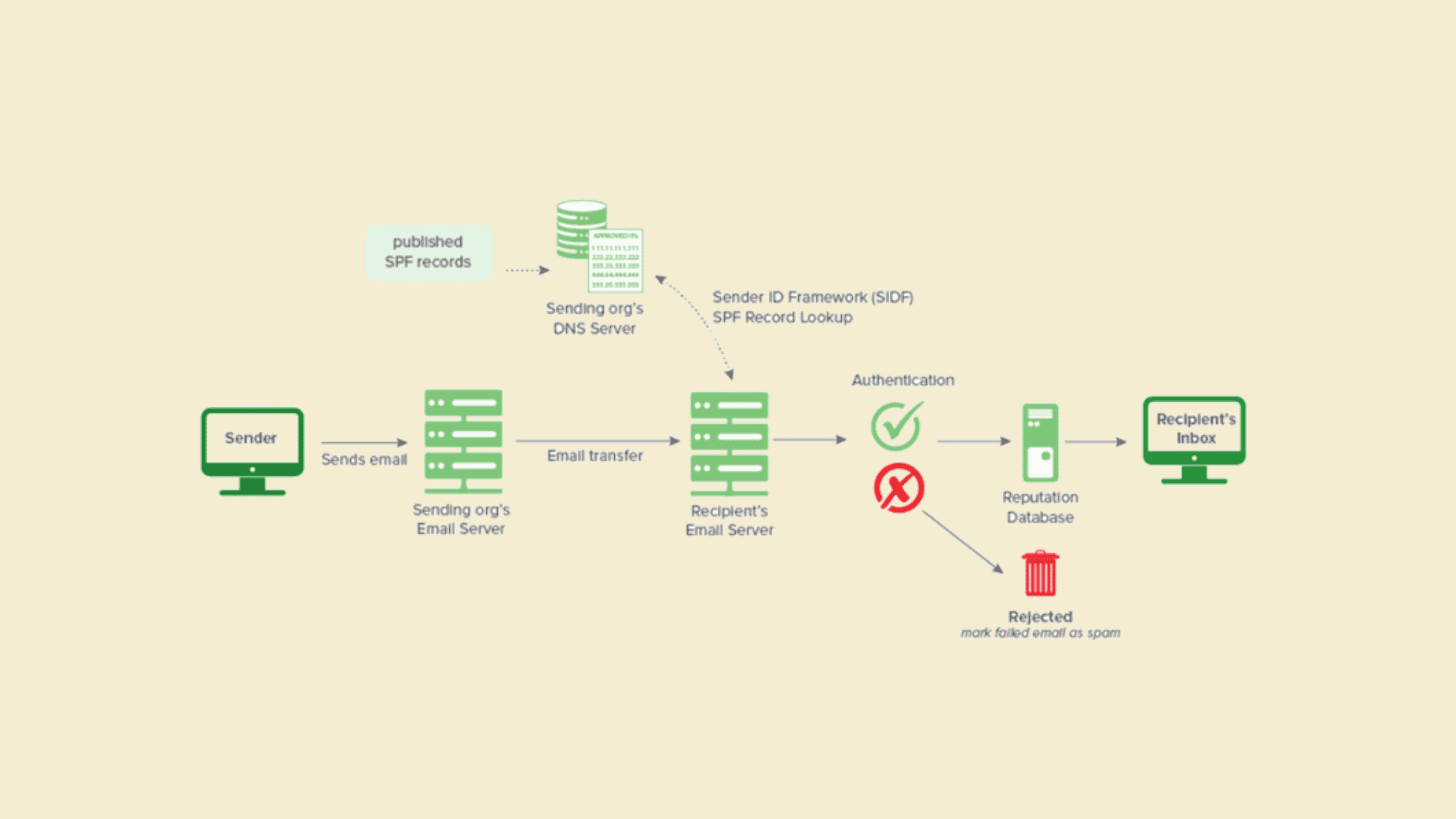
An SPF record is added as a TXT record in DNS (Domain Name Service), which informs the recipient mail server if the mail is from an authorized sender. SPF verifies if the email sender’s IP matches the list of IP addresses that are configured by the domain owner.
SPF provides an additional layer of security to SMTP (Simple Mail Transfer Protocol), which is the protocol used for sending and receiving mail since it does not have any authorization features.
Why Do We Need SPF?
Every organization needs an SPF record setup to discourage scammers who are trying to exploit legitimate emails. This record is an entry in DNS containing the IP of the sender’s email servers (or third-party services) from which emails will be sent on the company’s behalf.
This feature improves the deliverability of a legitimate email. If managing emails are done by third-party email systems like google suits etc. You need to set up SPF records that tell the recipient server that the system has the authorization to send mail on behalf of the organization.
If the SPF record is not present, the recipient mail server might present it with a warning that it can be phishing mail. In some cases, the mail without an SPF record can end up in spam mail or even never get received by the recipient. These kinds of situations can create potential damage to a company as the client/customer might miss important pieces of information shared.
Therefore, every domain owner should invest some time in creating an SPF record and add it to DNS so that their mail will not end up in a scam box. Personal third-party systems like Gmail, Yahoo, etc., have their own SPF record set up; hence personal users do not have to create SPF records separately.
How does an SPF Record work?
A domain name is a user-friendly name (easy to remember) that is connected to an IP address on the internet using the domain name service (DNS). The record added in DNS maps the domain name and the IP address. DNS can have several types of records added to it, like A record, MX record, etc.
SPF is a TXT record that lists the IP address of your domain that will allow the recipient mail server to identify if the mail is legitimate. An SPF record can have more than one IP address added to the record, which is authorized to send mail on behalf of the sender.
If the SPF protocol is set correctly and a legitimate email is sent, the receiver email server will perform a DNS check to find the TXT entry to verify if the sender IP and authorized list of IPs match the sender’s domain.
If no SPF record is available, email server administrators have preset rules defined to categorize a message. Sender’s email message will be notified that the mail is a ‘soft fail’ or a ‘hard fail.’ Depending on the settings in the recipient email server the ‘soft fail’ might reach the intended person, or it can also be dropped by the email server. In case of a ‘hard fail’, the mail may be dropped or end up in the scam folder of the recipient server.
Credits: Dmarcian
Every email communication is based on the email security configurations and filters set up by both sender and receiver mail servers. If the recipient mail server has an elevated level of security, it might straight away block incoming mail without an SPF record. Hence to not get flagged by the recipient mail server, it is highly recommended to have an SPF record in place.
Example for SPF Record
An SPF record has more features than just the IP address. It also informs the recipient server what action needs to be taken if the sender IP is not matching with the authorized IP. SPF can accept both IPV4 and IPV6 IP addresses.
An email can have two headers one is the directly visible friendly header (containing ‘envelope from’) in the mail, and the other is the technical header (return-path, mfrom).
Visible header
Technical Header
An SPF record looks like this:
v=spf1 ip4:48.213.51.127 ip6:2a05:d018:e3:8c00:bb71:dea8:8b83:851e include:authorized-domain.com -all
‘V=spf1’ – indicates the version of the SPF record (for now version will be always SPF1).
‘IP4’, and ‘IP6’– indicated the IPV4 and IPV6 addresses of your authorized mail server. We can list several IPs in an SPF records by adding the prefix IP4 or IP6 and adding space to it.
‘Include’ – Indicates that the mentioned third party is authorized to send mail on behalf of your domain.
‘-all’ – indicates the recipient server on what needs to be done if the sender IP does not match the listed IP. It sets the flag to fail.
‘~all’ results in a ‘soft fail’ which indicates the mail will reach the recipient with a warning that the mail could be malicious.
‘+all’ bypass all security and allows the mail to reach the recipient server without any problem.
How to Set up an SPF Record?
We read about all the components of an SPF record. Now to set up a record for your domain the first step is to customize and create an SPF record on your own by adding the IP address of your domain and third-party mail server details if you are using any. This should be hosted in your domain’s DNS server.
If you are using the DNS server of your domain registrar, a dashboard will be provided by the registrar where we can add or remove DNS entries. Before adding in DNS make sure to choose the entry type as TXT since the SPF record is a TXT entry.
Most of the time, the DNS server will be managed by a third-party provider or the company which hosts your domain. They will provide support if necessary. After adding your SPF record, it might take 72 hrs. to get enabled. After successfully implementing, you can test your new configuration by sending a mail. Check the email header to see the SPF authentication details.
If you find the SPF as “pass” it means the SPF record is working fine and the mail successfully reached the recipient server. If you check the spam box of your mail server, there will be emails with SPF fail and a warning message.
Things to keep in mind while you set up your SPF records:
Make sure to accurately update your records as your business grows and multiplies. If these changes are not applied in real-time, your SPF records will go outdated.
SPF is a signal to notify of fraud mail, and SPF failure will not guarantee that the mail is blocked.
SPF record breaks if the mail is forwarded
There are methods to bypass SPF hence it is recommended to apply additional security measures to SPF.
Hence having only an SPF record set up for your domain will not protect your organization, always be updated on the latest technologies, and update your domain security to avoid being an email compromise victim.
How to Check SPF Record?
There are multiple open-source platforms that will let you know if a domain has a valid SPF or not. Below are a few SPF lookup sites
The authentication policies SPF, DKIM, and DMARK are the main three authentication protocols to verify the authenticity of an email. In this post, we covered what SPF is and its need. We also learned how to set up an SPF record for your domain from scratch. In the upcoming articles, we will discuss in-depth on DKIM and DMARK.
We hope this post would help you understand what is SPF, why do we need SPF, how to set up an SPF record for your organization, and finally, how to check SPF records. Thanks for reading this post. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium & Instagram, and subscribe to receive updates like this.
You may also like these articles:
Aroma Rose Reji
Aroma is a cybersecurity professional with more than four years of experience in the industry. She has a strong background in detecting and defending cyber-attacks and possesses multiple global certifications like eCTHPv2, CEH, and CTIA. She is a pet lover and, in her free time, enjoys spending time with her cat, cooking, and traveling. You can connect with her on LinkedIn.