Table of Contents
Turn Your Raspberry Pi as a IDS/IPS Box and Hunt for Potential Intrusions on Your Network
You've probably guessed from the title what we're about to dive into. That's right – we're going to show you how to transform a compact Raspberry Pi into a fully functional IDS/IPS system, capable of detecting potential intrusions on your network. This tutorial is designed to empower security professionals and enthusiasts alike with a powerful tool for network protection.
Our approach involves installing Snort, a free open-source intrusion detection and prevention system, on Kali Linux, a Debian-based operating system renowned among security professionals. While we're using a Raspberry Pi for its portability, low power consumption, and sufficient processing power, you can replicate this setup on any physical or virtual machine running Debian, Ubuntu, Kali Linux, Mint Linux, or any Linux distribution that uses the apt package repository.
By the end of this guide, you'll have a compact, always-on device that's constantly monitoring your network for suspicious activity. So, let's roll up our sleeves and get started on building your personal IDS/IPS box!
Fundamental Knowledge Required:
Before we dive into the technical details, let's discuss the knowledge and skills you'll need to successfully follow this tutorial and set up your Raspberry Pi as an IDS/IPS box.
To get the most out of this guide, you should have:
1. Basic understanding of networking concepts
* IP addressing
* Network protocols
* Firewalls
2. Familiarity with Linux command line
* Basic terminal commands
* Package management with apt
3. Knowledge of cybersecurity fundamentals
* Understanding of common network attacks
* Familiarity with IDS/IPS concepts
4. Experience with Raspberry Pi (optional but helpful)
* Setting up and configuring a Raspberry Pi
* Basic Pi maintenance
5. Comfort with reading and modifying configuration files
Don't worry if you're not an expert in all these areas. We'll guide you through each step, providing explanations along the way. However, having this foundational knowledge will help you better understand the process and troubleshoot any issues that may arise.
If you need help, consider checking out these tutorial posts:
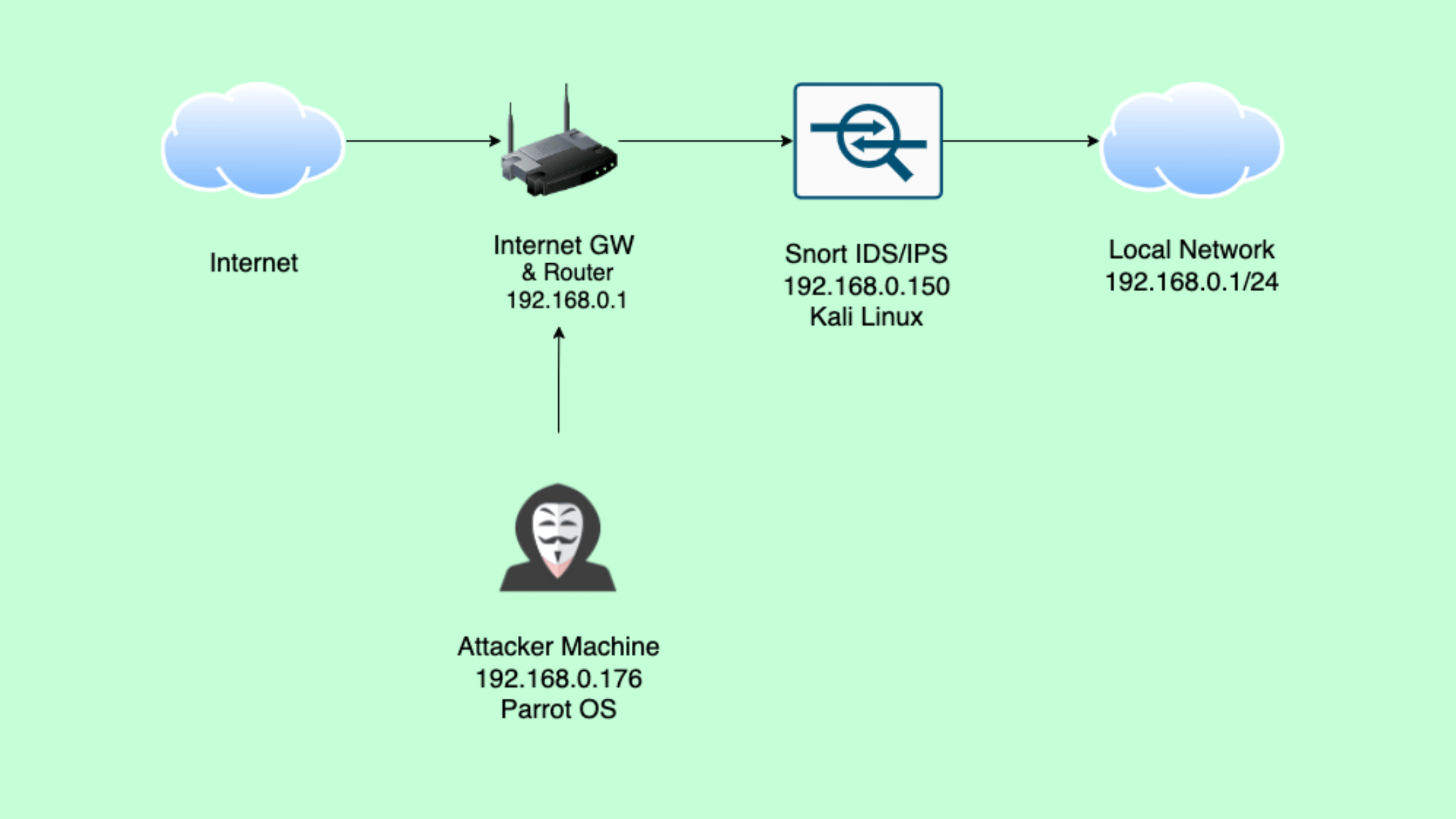
Our Lab Setup
For this tutorial, we'll be using a simple yet effective setup to demonstrate this tutorial. Here's what our lab environment looks like:
1. IDS/IPS Box (Defender)
* Device: Raspberry Pi
* Operating System: Kali Linux
* IP Address: 192.168.0.150
* Role: This will be our primary focus, serving as the IDS/IPS system to monitor and protect the network.
2. Attacker Machine
* Device: Raspberry Pi
* Operating System: Parrot OS
* IP Address: 192.168.0.176
* Role: We'll use this to simulate attacks and test our IDS/IPS setup.
Both Raspberry Pi devices are connected to the same local network, allowing us to simulate a realistic scenario where an attacker attempts to infiltrate a protected network.
Installing and Configuring Snort3 on Kali Linux
Now, you know our setup. Let's see how to install the Snort on the Kali box. In the following to this section, we will how to configure the Snort rules and also download the snort community rules to identify the potential intrusions on the network.
Installing Snort on Kali Linux
Let's install Snort on our Kali Linux Raspberry Pi. It's always a best practice to update the apt repos before installing the compiled packages from the repository.
Let's update the repository with this command:
sudo apt updateNext, we proceed to install Snort. We use the following command:
sudo apt install snortThis command triggers the installation process. The system first selects and unpacks various packages that Snort depends on, such as snort-common, libstro, libfastjson4, and others.
This installation process sets up Snort and its necessary components on our Kali Linux Raspberry Pi. Once completed. Just installation is not enough, Snort without any rule is a like a empty box. I strongly believe you are not hear to run an empty box.
We'll have Snort ready for configuration, which we'll cover in the next section.
Remember, the exact version numbers and package sizes may vary depending on when you're performing this installation, but the overall process remains the same.
Well, if you are curious to know the version info, run the snort command with -V option like this.
snort -VImportant Files and its Locations
Before jump into the configuring the Snort, it's recommend to learn some of its important files and its locations. Don't worry, it will not take more than 2 minutes.
IMP Note: We must tell you that we are talking about the Snort3 in this post. If you are coming from Snort2, you should see a lot of changes from v2 to v3. Example, now snort default configuration file has changed from snort.conf to snort.lua.
Snort 3 has a different file structure compared to its predecessors. Here are the key locations and files you need to know:
1. Main Configuration File
* Location: /etc/snort/snort.lua
* Snort 3 uses a Lua-based configuration file instead of the traditional text-based format.
2. Rules Directory
* Location: /etc/snort/rules/
* This directory contains various rule files that Snort uses to detect suspicious activities.
3. Snort Binary
* Location: /etc/bin/snort
* This is the executable file for Snort 3.
4. Log Directory
* Location: /var/log/snort/
* By default, Snort 3 stores its log files and alerts in this directory.
5. Local Rules File
* Location: /etc/snort/rules/local.rules
* You can add your custom rules in this file.
6. Default Policy File
* Location: /etc/snort/snort_defaults.lua
* This file contains default configurations and can be included in the main configuration file.
Validate the default configuration file
You already know where is the configuration file: /etc/snort/snort.lua
Let's validate running this command:
sudo snort -c /etc/snort/snort.luaThe command retuns something like this:
--------------------------------------------------
o")~ Snort++ 3.1.82.0
--------------------------------------------------
Loading /etc/snort/snort.lua:
Loading snort_defaults.lua:
Finished snort_defaults.lua:
references
classifications
ftp_server
alerts
daq
decode
host_tracker
network
process
so_proxy
smtp
file_policy
js_norm
stream_ip
stream_tcp
stream_user
arp_spoof
dns
pop
rpc_decode
trace
ssh
appid
wizard
binder
http2_inspect
http_inspect
ftp_data
ftp_client
ips
file_id
port_scan
gtp_inspect
dce_http_server
dce_http_proxy
dce_udp
dce_tcp
dce_smb
s7commplus
modbus
mms
iec104
dnp3
cip
telnet
ssl
sip
normalizer
netflow
imap
back_orifice
stream_file
stream_udp
stream_icmp
stream
output
host_cache
hosts
search_engine
packets
active
Finished /etc/snort/snort.lua:
Loading file_id.rules_file:
Loading file_magic.rules:
Finished file_magic.rules:
Finished file_id.rules_file:
--------------------------------------------------
ips policies rule stats
id loaded shared enabled file
0 208 0 208 /etc/snort/snort.lua
--------------------------------------------------
rule counts
total rules loaded: 208
text rules: 208
option chains: 208
chain headers: 1
--------------------------------------------------
service rule counts to-srv to-cli
file_id: 208 208
total: 208 208
--------------------------------------------------
fast pattern groups
to_server: 1
to_client: 1
--------------------------------------------------
search engine (ac_bnfa)
instances: 2
patterns: 416
pattern chars: 2508
num states: 1778
num match states: 370
memory scale: KB
total memory: 68.5879
pattern memory: 18.6973
match list memory: 27.3281
transition memory: 22.3125
appid: MaxRss diff: 3084
appid: patterns loaded: 300
--------------------------------------------------
pcap DAQ configured to passive.
Snort successfully validated the configuration (with 0 warnings).
o")~ Snort exitingIf you see "Snort successfully validated the configuration (with 0 warnings)." your configuration file has no errors or warnings. You are good to proceed.
Create a Simple Rule and Test
You can create a rule in any location. However, you should keep two things to run the rule file:
A read permission is set for the file.
Rules file should end with the .rules file extension.
It's good practice to keep the rule file under /etc/snort/rules/ directory. Let's create a file with name local.rules underneath /etc/snort/rules/.
sudo nano /etc/snort/rules/local.rulesAdd this simple rule to test the Snort.
alert icmp any any -> any any (msg:"ICMP Echo Request detected"; sid:1000001;)This rule we created to detect ICMP Echo Request packets (commonly known as ping requests) on your network. Here's a detailed explanation of each part:
1. alert: This is the action the rule will take when triggered. In this case, it will generate an alert.
2. icmp: This specifies the protocol the rule is watching for. Here, it's looking at ICMP traffic.
3. any any: These two "any" values represent the source IP address and port. In this case, it means the rule will trigger for ICMP traffic from any source IP and any source port.
4. ->: This arrow indicates the direction of traffic. It separates the source and destination information.
5. any any: These represent the destination IP address and port. Again, "any" means it will match any destination IP and port.
6. (msg:"ICMP Echo Request detected";: This is the message that will be included in the alert when the rule is triggered. It provides a human-readable description of what was detected.
7. sid:1000001;: This is the Signature ID (SID) for the rule. It's a unique identifier for this specific rule. SIDs under 1,000,000 are usually reserved for official Snort rules, so custom rules typically start at 1,000,001.
In summary, this rule will generate an alert for any ICMP Echo Request (ping) packet, regardless of its source or destination.
Let's test the Snort rule against its configuration. To do that, you need to supply the Snort configuration file with -c flag and rule file with -R flag. Like this:
sudo snort -c /etc/snort/snort.lua -R /etc/snort/rules/local.rulesYou should see "Snort successfully validated the configuration (with 0 warnings)." if your configuration file and rules have no issues.
Now, it's time to test the rule against the live traffic.
To do that you need to assign your network interface to listen to the traffic with -i flag and print the alert message on the console with -A flag. Let's construct the command.
sudo snort -c /etc/snort/snort.lua -R /etc/snort/rules/local.rules -i wlan0 -A alert_fastThis command lets Snort to listening mode and start listing the traffic and print alerts if there is traffic that matches the rule local.rules file.
Let's generate some ICMP traffic from another machine.
See the Snort console. If your rules and configuration files are configured correct, you should see ICMP alerts on Snort console. Which we can see in our case.
This validates that Snort is functioning as expected.
Monitor Intrusions with Snort Community Rules
Snort's effectiveness as an IDS/IPS largely depends on its rules. These rules define patterns of network traffic that may indicate malicious activity. Snort offers several types of rule sets:
Community Rules: Free, publicly available rules created and maintained by the Snort community. These rules provide a solid foundation for detecting common threats.
Registered Rules: Available for free after registration. These rules are more current than community rules and are updated more frequently.
Subscription Rules: Premium rules are available with a paid subscription. These offer the most comprehensive and up-to-date protection.
For our Raspberry Pi IDS/IPS setup, we'll start with the Community Rules. While not as extensive as the subscription rules, they still offer valuable protection against many common threats.
The procedure is quite simple and straightforward.
Download the community rules from the Snort official site:
wget https://www.snort.org/downloads/community/snort3-community-rules.tar.gzExtract the downloaded file:
tar -xvzf snort3-community-rules.tar.gzMove the rules to Snort's rules directory:
sudo mv snort3-community.rules /etc/snort/rules/Running Snort with Community Rules:
sudo snort -c /etc/snort/snort.lua -R /etc/snort/rules/snort3-community.rules
-i wlan0 -A alert_fastUse -q flag to print only the alert info and you can log the captured rules in a file with -l flag.
sudo snort -c /etc/snort/snort.lua -R /etc/snort/rules/snort3-community.rules -i wlan0 -A alert_fast -q -l /var/log/snort/This configuration allows Snort to monitor every packet that passes through the wlan0 interface. To monitor the whole network, you need to deploy Snort on a machine that acts as a network gateway. Simple as is.
Options to Run Snort
A tip for beginners: Learn about these flags to run snort command. This would let you know to try different configuration files, rule sets, interfaces, pcap files, and desirable output formats.
1. Configuration File (-c)
* Always specify your configuration file:
-c /etc/snort/snort.lua2. Interface Selection (-i)
* Specify the network interface to monitor:
* Use ifconfig or ip a to identify your network interfaces.
-i eth03. Verbose Mode (-v)
* For detailed output, useful when troubleshooting:
4. Alert Output (-A)
* Choose how alerts are displayed:
-A console # Display alerts on the console
-A cmg # Basic console output with timestamps
-A alert_fast # Fast alert output to a file5. Packet Logging (-l)
* Specify a directory for log files:
-l /var/log/snort6. Read PCAP File (-r)
* Analyze a captured packet file:
-r captured_traffic.pcap7. Don't Run as Daemon (-D)
* Keep Snort in the foreground:
8. Show Rule Sid (-s)
* Display the SID of the rule that triggered an alert:
9. Dump Application Layer (-d)
* Display the application layer in alerts:
10. Test Configuration (--treat-drop-as-alert)
* Useful for testing rules without blocking traffic:
Example command combining multiple flags:
sudo snort -c /usr/local/etc/snort/snort.lua -i eth0 -A console -v -l /var/log/snortThis is how we built a free IDS/IPS solution for our home network on small size computers like Raspberry Pi. We recommend using RPI 4 Mod B or RPI 5 with at least 4GB memory to handle the network traffic. You can replicate the setup on any physical or virtual computer.
If you want to try registered or subscription rules you should register with snort.org and get Oinkcode API key. And need to install pulledpork with a few other dependency packages & plugins. We will show how to run registered or subscription rules on a different tutorial post.
Please keep visiting thesecmaster.com for more such technical information. Visit our social media page on Facebook, Instagram, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive information like this.
You may also like these articles:
TStep-by-Step Guide to Install and Configure Snort3 on Kali Linux with Auto Rule Updates Using PulledPork
How to Configure Your SIEM to Identify Reconnaissance Attacks on Your Network?
Step-by-Step Guide to Install Raspberry Pi OS on a Raspberry Pi Single Board Computer!
How to Turn Your Raspberry Pi into a Network Scanning Device?
Step By Step Procedure To Build Your Own Surveillance System Using Raspberry Pi
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.